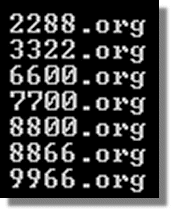
F-Secure: More on the 0-Day Word Exploit -- 3322, 8866, etc.
Image source: F-Secure
Mikko writes on the F-Secure "News from the Lab" Blog:
There's been quite a lot of buzz about the new 0-day Word vulnerability.More here.
While talking about details of the vulnerability, it's easy to forget what the vulnerability was actually used for.
According to the information we have, a US-based company was targeted with emails that were sent to the company from the outside but were spoofed to look like internal emails.
The emails contained a Word DOC file as an attachment. DOCs are a nasty attack vector. Few years ago, when macro viruses were the number one problem, many companies were not allowing native DOC files through their email gateways. Now that has changed, and DOCs typically get through just fine. But Word has vulnerabilities and users typically don't install Word patches nearly as well Windows patches.
When run, the exploit file ran a backdoor, hid it with a rootkit and allowed unrestricted access to the machine for the attackers, operating from a host registered under the Chinese 3322.org domain.








0 Comments:
Post a Comment
<< Home