Gurong Rootkit: From Russia With Love
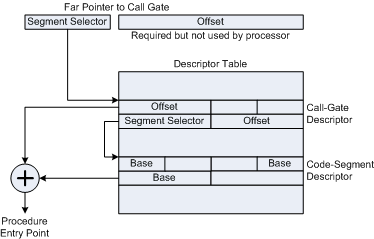
Illustration of the procedure to install a call gate to the
Global Descriptor Table (GDT).
Image source: F-Secure
Global Descriptor Table (GDT).
Image source: F-Secure
Kimmo writes over on the F-Secure "News from the Lab" Blog:
Yesterday we received an interesting email-worm sample, detected as Gurong.a, that uses rootkit techniques to hide its file, process and launch point in the registry. It is based on the infamous Mydoom code and it is in the wild but currently spreading very slowly.More here.
Gurong.a modifies the operating system kernel, specifically the system service table and process object structures, so it is a kernel-mode rootkit. What makes it different from other kernel-mode rootkits we have seen is the way it installs the rootkit payload into kernel. Often malware uses a special purpose driver or the physical memory device to modify the kernel from user mode.
Gurong.a uses the physical memory device as its initial injection vector to install a call gate to the Global Descriptor Table (GDT) that resides in system address space. Call gates are things we do not see everyday. Below is a definition from Wikipedia:
“Call gate is a mechanism in intel x86 architecture for changing privilege level of CPU when it executes a predefined function call.”








0 Comments:
Post a Comment
<< Home