Mainstream: Columbus Day Protest Leads to Arrests
 Russell Means
Russell MeansA
Reuters newswire
article, via
MSNBC, reports that:
About 75 protesters, including American Indian activist Russell Means, were arrested on Saturday after blocking Denver's downtown parade honoring the Italian-born discoverer Christopher Columbus, an event they denounced as "a celebration of genocide."
Police loaded protesters onto buses after they refused orders to disperse. Most will be charged with obstruction of a roadway or disrupting a lawful assembly, Denver Police Lt. Ron Saunier said.
Police delayed the parade's start for more than an hour as they tried to head off confrontations.
American Indian groups and their supporters have disrupted the city's annual Columbus Day parade every year for nearly two decades, leading to clashes with Colorado's Italian-American community over the century-old celebration, the longest-running such commemoration in the United States.
More
here.
Gapingvoid: Drowning
Via gapingvoid.com. Enjoy!

Democrats to Offer Dangerous New Surveillance Compromise
Ellen Nakashima writes in The Washington Post:
House Democrats plan to introduce a bill this week that would let a secret court issue one-year "umbrella" warrants to allow the government to intercept e-mails and phone calls of foreign targets and would not require that surveillance of each person be approved individually.
The bill is likely to resurrect controversy that erupted this summer when Congress, under White House pressure, rushed through a temporary emergency law that expanded the government's authority to conduct foreign surveillance on U.S. soil without a warrant. The Protect America Act, which expires in February, has been criticized as being too broad and lacking effective court oversight.
The Democrats' legislation, drafted by the Intelligence and Judiciary committee chairmen, is aimed to reconcile civil liberties, privacy and national security concerns. It would overhaul the Foreign Intelligence Surveillance Act (FISA), a 1978 law amended many times that the Bush administration argues has been outstripped by technology.
More
here.
PLEASE: Contact your representatives NOW and tell them that any compromise on this issue is UNACCEPTABLE.
Background Checks at NASA JPL Blocked
An AP newswire article by John Antczak, via The Washington Post, reports that:
A federal appeals court on Friday blocked a Bush administration directive requiring background checks and access to personal information of employees of NASA's Jet Propulsion Laboratory, which some contend amounts to an invasion of privacy.
The JPL employees had until Friday to comply with the directive or face the possibility of losing their jobs. They would have been required to fill out questionnaires and submit a waiver allowing the investigations.
The U.S. Court of Appeals for the 9th Circuit issued the emergency temporary injunction requested by the 28 employees after a lower court denied the request Wednesday. The lab, managed for NASA by the California Institute of Technology, has about 5,000 employees.
More
here.
U.S. Toll in Iraq, Afghanistan
Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Saturday, Oct. 6, 2007, at least 3,815 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 3,105 died as a result of hostile action, according to the military's numbers.
The AP count is nine higher than the Defense Department's tally, last updated Friday at 10 a.m. EDT.
As of Saturday, Oct. 6, 2007, at least 381 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures Sept. 29, 2007.
Of those, the military reports 254 were killed by hostile action.
More
here and
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Quote of the Day: Benny Bleiman
"In a breakthrough heralded by some as 'a major advancement toward the annihilation of the human species,' a military contractor known as the Defense Advanced Research Projects Agency (DARPA) is utilizing robotic hybrid insects for surveillance and intel gathering."
- Benny Bleiman, writing on Zooillogix.
FCC Will Not Probe Telco Disclosure of Phone Records
Peter Kaplan writes for Reuters:
The head of the U.S. Federal Communications Commission declined to investigate reports that phone companies turned over customer records to the National Security Agency, citing national security concerns, according to documents released on Friday.
FCC Chairman Kevin Martin turned down a congressional request for an investigation as a top intelligence official concluded it would "pose an unnecessary risk of damage to the national security," according to a letter National Intelligence Director Michael McConnell sent to Martin on Tuesday.
Intelligence officials "support your determination not to initiate an investigation," McConnell wrote to Martin.
At issue are reports last year that some big telephone companies allowed the U.S. government access to millions of telephone records for an anti-terrorism program.
More
here.
Lawmaker Shows Naked Woman During School Lecture
An AP newswire article, via CNN, reports that:
A state legislator surprised a high school class when the computer he was using projected a photo of a nude woman during a lecture on how a bill becomes a law.
State Rep. Matthew Barrett was giving a civics lesson Tuesday when he inserted a data memory stick into the school computer and the projected image of a topless woman appeared instead of the graphics presentation he had downloaded.
Police interviewed Barrett and school officials and seized the data memory stick and the computer to determine where the image came from, a state highway patrol spokesman said.
Barrett said there were a few snickers from the approximately 20 students in the senior government class at Norwalk [Ohio] High School when the image appeared. He said he immediately pulled the memory stick out of the computer.
More
here.
(Props, Emergent Chaos.)
Retail Group Takes a Swipe at PCI
Jaikumar Vijayan writes on ComputerWorld:
Simmering discontent within the retail industry over the payment card industry (PCI) data security standards erupted into the open this week with the National Retail Federation (NRF) asking credit card companies to stop forcing retailers to store payment card data.
In a tersely worded letter to the PCI Security Standards Council, which oversees implementation of the standard, NRF CIO David Hogan asked credit card companies to stop making retailers "jump through hoops to create an impenetrable fortress" to protect card data. Instead, "retailers want to eliminate the incentive for hackers to break into their systems in the first place."
More
here.
Germany: Credit Card Data Theft Affects Tens of Thousands of Kartenhaus Customers
Via heise Online.
The Hamburg ticket sales office Kartenhaus informed its customers on Thursday that still unidentified culprits had stolen credit card numbers and billing addresses. Some 66,000 customers who purchased tickets with a credit card from the Kartenhaus.de website between October 24, 2006 and September 30, 2007 were affected. The only exceptions were credit card purchases of tickets to sporting events featuring Hertha BSC, HSV Handball, and Eisbären Berlin.
The parent company, Ticketmaster, advised customers to "check your credit card bills as soon as possible to identify any irregularities or abuse". It is still not known how the thief or thieves gained access to the data. Apparently only one server was affected. Ticketmaster Europe's Vice President, Tommy Higgins, said that as soon as the attack was discovered, an internal team was assembled to track down the security hole and to inform all necessary personnel.
More
here.
(Props, Pogo Was Right.)
See Any Resemblence?


I do.
Details here. - ferg
Quote of the Day: Ray Beckerman
"A verdict of $222,000.00, for infringement of 24 song files worth a total of $23.76?"
"In a case where there was zero evidence of the defendant having transferred any of those files?"
"It is one of the most irrational things I have ever seen in my life in the law."
- Ray Beckerman, writing on The Recording Industry vs. The People.
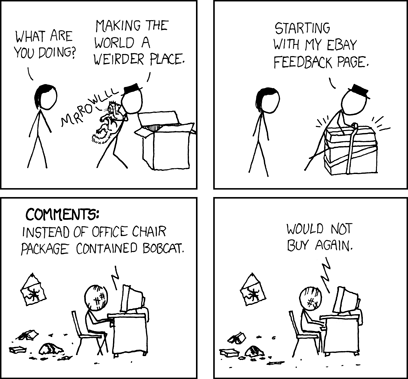
xkcd: The Cost of Doing Business
Click for larger image.
We
love xkcd.
U.S. Toll In Iraq
Via The Boston Globe (AP).
As of Thursday, Oct. 4, 2007, at least 3,809 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 3,105 died as a result of hostile action, according to the military's numbers.
The AP count is three higher than the Defense Department's tally, last updated Thursday at 10 a.m. EDT.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Stupid Security: Woman Told to Ditch Bra to Enter Court
An AP newswire article, via The Boston Globe, reports that:
Security guards refused to allow a woman into a federal courthouse until she removed a bra that triggered a metal detector.
Lori Plato said she and her husband, Owen Plato, were stunned when U.S. Marshals Service employees asked her to remove her bra after the underwire supports set off the alarm.
"I asked if I could go into the bathroom because they didn't have a privacy screen and no women security officers were available," Plato said Wednesday. "They said, 'No.'
More
here.
The Great Firewall of China Turns Its Attention to RSS Feeds
Jacqui Cheng writes on ARS Technica:
As many readers who follow the antics of the Chinese government know, when it comes to enforcing the "Great Firewall of China," consistency isn't exactly its strong point. While certain phrases, concepts, and entire web sites are regularly blocked from reaching the eyeballs of many Chinese Internet surfers, things like high traffic are enough to let a number of forbidden concepts slip through.
And then there's the indecision of China's Public Security Bureau (PSB), which has blocked certain sites (such as Blogspot and Wordpress blogs) on and off for some time now, and enforces the blocks inconsistently between providences. For a One True China, there are certainly many interpretations of what is and isn't allowed through the country's cyber connection.
More
here.
Nature Conservancy Says Spyware Compromised Employee Data

Joe Stephens writes in The Washington Post:
A human resources employee at the Nature Conservancy in Arlington used his laptop last month to visit a sports Web site. A short time later, computer technicians at the world's largest environmental organization noticed a torrent of data flowing out of its computer network.
The bad news arrived in the in-boxes of Conservancy staff members a week later: The employee had inadvertently downloaded a spyware program from the Web site, which allowed the software to seize personal and financial information about thousands of Conservancy employees from his hard drive. The rogue program moved the information through a sophisticated network of servers in a number of countries, cloaking the final destination.
Officials say 14,000 people are in danger of having their identities stolen. The hijacked data includes names, home addresses, Social Security numbers, payroll direct-deposit account numbers, bank routing numbers, and benefits and beneficiary information. Those affected include employees, former employees and dependents of employees who worked for the Conservancy between 2000 and Aug. 3 of this year.
More
here.
Note: People may wonder at times why security breaches at public websites is a big deal (just two recent examples
here and
here). Well, wonder no more.
- ferg
Google Earth Spots Two More Chinese SSBNs

Hans M. Kristensen writes on The Strategic Security Blog:
China appears to have launched two more ballistic missiles submarines from the Bohai shipyard at Huludao approximately 400 km east of Beijing. This could bring to three the number of Jin-class (Type 094) nuclear-powered ballistic missile submarines (SSBNs) launched by China in the past three four years.
The two submarines were discovered during analysis of newly published commercial satellite images on Google Earth. This is the second time in three months that FAS has discovered new Chinese ballistic missile submarines on commercial satellite images. The first time was in July 2007, when the first Jin-class was disclosed on the FAS Strategic Security Blog.
The submarines on the new image have the same dimensions as the previous submarine.
More
here.
Image source: Strategic Security Blog / Google Earth
Canadian Computer Breaches Exposed
Jeremy Loome writes on The Edmonton Sun:
Security holes at Alberta's government offices and educational institutions contributed to computer network breaches at Alberta Health and Grant MacEwan College, according to the auditor general.
They were the most serious among dozens of security protocol issues at just about every level of government and the education community. In many, the breaches were as simple as not having proper password policies in place.
But in the cases of Mac-Ewan College and the health department, the breaches potentially exposed their networks. MacEwan left unfettered Internet access to private financial documents, while Alberta Health logged unknown, unauthorized connections during occasional security checks.
It's impossible to tell in either case whether important personal information was stolen.
More
here.
(Props, Pogo Was Right.)
Bad Things Lurking on Government Websites
Robert McMillan writes on InfoWorld:
The U.S. federal government took steps earlier this week to shut down Web sites in California in order to protect the public from hacked Web sites, but new incidents show that the problem is not going away any time soon.
On Thursday, compromised pages hosted by the Brookhaven National Laboratory and the Superior Court of Madera County, California, were still hosting inappropriate content. Brookhaven had links that redirected visitors to pornographic Web servers, and the Madera County court site featured ads for porn and Viagra.
Brookhaven has begun an investigation into the incident, said Tom Schlagel, a manager with the lab's information technology division. "From what I've been told, there isn't any evidence that there's any pornography on the server," he said. "It's all just redirections."
Brookhaven is a U.S. Department of Energy lab that specializes in nuclear and high-energy research.
More
here.
U.S. Anti-War Activists Denied Entry to Canada
An AP newswire article, via The Globe and Mail, reports that:
U.S. peace activists Medea Benjamin and Ann Wright have had a tough time entering Canada lately because their names send up red flags in border agents' computers.
Both women have been arrested in the United States protesting against the Iraq war, which has landed them in an international criminal database. When they visited Canada in August, they were told they would have to apply for "criminal rehabilitation" and pay $200 if they ever wanted to visit again. Neither applied.
Yesterday, Ms. Benjamin, co-founder of the anti-war group Code Pink, and Ms. Wright, a retired U.S. army colonel, walked into Canada at Niagara Falls to test whether they really would be denied entry because of their anti-war-related arrests.
They were.
More
here.
The Internet: Made For Hacking

Andy Greenberg writes on Forbes.com:
Vint Cerf, Google's chief Internet evangelist, says the Internet is insecure. And he should know — he helped build the thing.
Cerf, who helped design the first protocols that allowed information to be sent across computer networks in the late 1970s, expressed regret in a speech Tuesday that he hadn't designed the Internet to be a safer, more regulated system.
"We didn't pay a great deal of attention to the security side of the Internet when it was first being designed because we didn't really know if it would work at all," Cerf said in the keynote address at Georgia Tech's annual security summit. "Much of the problems that you all face every day might be caused by that."
More
here.
ESet: Storm Worm Traffic Analysis
 Click for larger image.
Click for larger image.Pierre-Marc Bureau
writes on the
ESet Threat Blog:
The conspicuous spikes in traffic occurring when a node joins the Nuwar network and the subsequent control traffic appearing every hour will be quite noticeable to vigilant network administrators. The authors of this malware seem to have chosen reliability over network stealth.
The security industry needs to pay attention to the operational compromises attackers are making. These tradeoffs can point to design weakness which help us secure our infrastructure.
More
here.
Image source: ESet
Image of the Day: Sputnik

Via A Soviet Poster a Day.
Patch Tuesday: Microsoft to Issue Seven Patches
Robert Vamosi writes on the C|Net News Blog:
As part of this month's Patch Tuesday, coming next week, Microsoft plans to release seven patches, four rated "critical" and three "important." Affected software includes Windows (Windows 2000, XP, and Vista), Office (Word and SharePoint Server), Internet Explorer, Outlook Express and Windows Mail. One patch affects Microsoft Office 2004 for the Mac.
More here.
eBay: Phishers Getting Better Organized, Using Linux
Robert McMillan writes on InfoWorld:
When it comes to launching online attacks, criminals are getting more organized and branching out from the Windows operating system, eBay's security chief said Tuesday.
eBay recently did an in-depth analysis of its threat situation, and while the company is not releasing the results of this analysis, it did uncover a huge number of hacked, botnet computers, said Dave Cullinane, eBay's chief information and security officer, speaking at a Microsoft-sponsored security symposium at Santa Clara University.
Cullinane, who one year ago downplayed the role of organized crime in phishing ("It's not the Sopranos," he said), believes that online attackers are indeed becoming more sophisticated with malware developers now being funded to develop new and improved attacks.
More
here.
U.S. Study Urges Firmer Guard Against Atomic Terrorism
Mark Heinrich writes for Reuters:
Some sites with bomb-grade uranium have no more security than a night watchman and chain-link fence, researchers said on Wednesday, warning against complacency in deterring nuclear theft and terrorism.
A report commissioned by the U.S.-based Nuclear Threat Initiative (NTI) cited significant progress safeguarding and removing vulnerable nuclear stockpiles globally, but dangerous gaps persisted in Russia, Pakistan and elsewhere.
More
here.
San Francisco: Audit Finds City's IT in Disarray
Wyatt Buchanan writes in The San Francisco Chronicle:
The absence of central oversight and planning in the purchase of computer and information technology by San Francisco City Hall is wasting millions of dollars a year, inhibiting efficient use of government data and creating technological backwaters across municipal government, according to an audit released Wednesday.
The audit by the Board of Supervisors budget analyst also found city computer networks are vulnerable to outside attacks, and a large-scale project to consolidate criminal databases used by law enforcement and the courts is years behind schedule.
"It's pretty devastating. I don't think you can be too hyperbolic," said Supervisor Tom Ammiano, who requested the audit. "There doesn't really seem to have been anyone in charge of the store."
More
here.
Note: If San Francisco doesn't get it's collective IT act together, they are likely to find themselves in the
same situation as other California government network resources --
hacked.
- ferg
Portrait of an Alleged Young Cyber Punk
Dan Goodin writes on The Register:
Late in the evening of February 13, Paul and Robin Laudanski were planning the following day's Valentine's celebration when they received word that CastleCops, the volunteer security website they run, was under assault.
At its peak, the five-day attack flooded CastleCops with close to 1 gigabyte of data every second. The distributed-denial-of-service deluge was so severe that the husband-and-wife team were forced to take their site offline 15 minutes after it started. It also knocked CastleCops' webhost offline for two days, causing more than $160,000 worth of damage to the company and its customers.
"We were planning on having a family Valentine's event," said Paul Laudanski, who along with Robin was forced to spend the next several days migrating to a new hosting provider. "Then, of course, the DDoS started, which ruined those plans."
The attack, according to federal prosecutors, was the handiwork of Greg C. King, a 21-year-old California resident who at one point maintained a 7,000-node botnet. On Monday, he was publicly charged with four counts of illegal hacking, charges that carry a maximum penalty of 40 years in prison and a $1m fine.
More
here.
Note: Paul & Robin are friends of mine, and I'm delighted this kid was busted.
- ferg
Gathering 'Storm' Superworm Poses Grave Threat
Bruce Schneier writes on Wired's Security Matters:
The Storm worm first appeared at the beginning of the year, hiding in e-mail attachments with the subject line: "230 dead as storm batters Europe." Those who opened the attachment became infected, their computers joining an ever-growing botnet.
Although it's most commonly called a worm, Storm is really more: a worm, a Trojan horse and a bot all rolled into one. It's also the most successful example we have of a new breed of worm, and I've seen estimates that between 1 million and 50 million computers have been infected worldwide.
Worms like Storm are written by hackers looking for profit, and they're different. These worms spread more subtly, without making noise. Symptoms don't appear immediately, and an infected computer can sit dormant for a long time. If it were a disease, it would be more like syphilis, whose symptoms may be mild or disappear altogether, but which will eventually come back years later and eat your brain.
More
here.
Note: This is an excellent summary of the Storm situation. Great job, Bruce.
Hoax Tech: Did Russia Stage the Father of All Bombs Hoax?
David Axe writes on Wired News:
Western media reacted with alarm. An editor for Jane's told the BBC it was likely that FOAB [Father Of All Bombs] indeed represented "the world's biggest non-nuclear bomb." UPI claimed the device "would enormously boost Russia's conventional military capabilities."
But close analysis of the video reveals inconsistencies that have led some U.S. experts to question the veracity of the Russian claims, and to downgrade assessments of the weapon. It's possible, they say, that the video was partially faked, and that the test was hyped for political reasons.
More
here.
U.S. Toll in Iraq, Afghanistan
Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Wednesday, Oct. 3, 2007, at least 3,809 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 3,105 died as a result of hostile action, according to the military's numbers.
The AP count is three higher than the Defense Department's tally, last updated Wednesday at 10 a.m. EDT.
As of Wednesday, Oct. 3, 2007, at least 381 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures Sept. 29, 2007.
Of those, the military reports 254 were killed by hostile action.
More
here and
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
WTF? DHS Mail List Meltdown Becomes Internet Party for Exposed Gov Workers
Kim Zetter writes on Threat Level:
A Department of Homeland Security mailing list that provides unclassified daily news reports on critical infrastructure information experienced a meltdown today when the list apparently got misconfigured and began routing any reply that someone sent to another person on the list to every subscriber on the list.
The list was further configured to reveal the e-mail address of the senders so that the names and contact details of hundreds of list members -- including government workers in critical infrastructure positions -- were exposed. The mishap also revealed an interesting tidbit -- at least one member of the list works in some capacity with Iran's Ministry of Defense.
More
here.
California: State Government Web System Shutdown Takes Local Official by Surprise
Brad Breithaupt writes on the Marin Independent Journal:
A small Marin agency with the job of helping move cars and people up and down the freeway almost brought state government's access to the Internet super-highway to a grinding halt Tuesday night.
The Transportation Authority of Marin's Web site problem with a porn hacker prompted federal officials to pull the plug on California's "ca.gov" Web network, creating an emergency for the state Informational Technology Department until the connection was fully restored after several hours.
"The feds were probably taking appropriate action, but they were probably using a shotgun to kill a flea," said John Hanacek, spokesman for the state Department of Technology Services.
More
here.
Background
here,
here &
here.
Radiohead Website Crashes as Fans Rush to Order Album
Arifa Akbar writes on The Independent:
Radiohead's official website was back online last night after overwhelming demand for the band's new album caused it to crash. Traffic on the site slowed to a crawl after the rock group told fans on Monday that they could pre-order the new release, In Rainbows, from www.radiohead.com at any price they wanted.
The band's spokesman, Murray Chalmers, said the collapse of the site was caused by waves of British fans logging on after the announcement about the album. They were followed by fans on the east coast of the US, who woke to the surprise news, followed by Radiohead enthusiasts on the west coast.
More
here.
Web 2.0 is a Security Risk
Linda Rosencrance writes on ComputerWorld:
With the Web becoming central to the way companies do business, cybercriminals are taking increasing advantage of Web 2.0 and social networking sites to launch attacks, according to IDC analyst Christian Christiansen.
The Web isn't the benign resource for information that people once saw it as, said Christiansen, who spoke today at Kaspersky Lab Inc.'s Surviving CyberCrime conference in Waltham, Mass. "One of the things that's happened that's disconcerting -- and it's been growing over the last 10 years -- is the blending of people's private lives with their corporate lives," he said.
More
here.
AT&T Defends Plan to Detect Customers' Net Piracy
Anne Broache writes on the C|Net News Blog:
An AT&T executive on Wednesday sought to defuse fears that forthcoming tools aimed at identifying pirates on its network will harm the average Net surfer's online experience.
The planned tactic is "not about heavy-handed tactics that go after the vast majority of our customers that want to consume content legally," AT&T assistant vice president of regulatory policy Brent Olson said at an antipiracy summit here hosted by the U.S. Chamber of Commerce. "It's about making more content available to more people in more ways going forward."
In June, AT&T announced that it was collaborating with Hollywood studios and other copyright holders to come up with technological solutions to prevent users from swapping massive amounts of content in an unauthorized manner. The idea is to target and identify the most salient offenders, according to news reports at the time, but it remains unclear exactly how the technique will work.
More
here.
Quote of the Day: Richard Stiennon
"In the 7th-8th graders surveyed for instance: 21% have lied online about their age, 10% pretended to be someone else, 7% have circumvented security measures, 5% have used IT devices to cheat on school work."
"One interesting result is that he found juvenile high-tech crime offenders tend to specialize. They are either good data miners, hackers, crackers, etc."
- Richard Stiennon, writing on Threat Chaos.
Malware Boom Puts Pressure on Second-Tier AV Labs
Matt Hines writes on InfoWorld:
With the volume of malware attacks growing so rapidly, the pressure on AV research labs to find and defend against new threats to keep their products up to date and customers ahead of the curve has never been greater.
Based on the sheer number of threats, and the sprawl of massive research operations such as Symantec's 40,000 sensor-strong Global Intelligence Network, some experts maintain that only a few of the largest labs will be able to compete in the long run.
Beyond Symantec and its biggest rivals -- including McAfee, Microsoft, and Trend Micro -- it will be unlikely that additional AV researchers and technology vendors will be able to remain relevant, said Neil MacDonald, a longtime security industry analyst with Gartner.
More
here.
Trusted Websites Are Being Hacked and Don't Even Know It
Robert McMillan writes on InfoWorld:
It's getting harder and harder to know who to trust on the World Wide Web, according to online safety advocates StopBadware.org.
On Tuesday, the group released its 2007 Trends in Badware report [.pdf], saying the bad guys are finding new ways to place their malicious software on our computers -- often by compromising Web sites that we trust.
With the help of one of its sponsor companies, Google, StopBadware maintains a list of 200,000 Web sites that are known to be associated with malicious downloads. According to Max Weinstein, a project manager with StopBadware, more than half of these sites have been hacked and don't even realize it.
In fact, this move to delivering malicious software on legitimate sites has been a disturbing trend over the past year, he said.
More
here.
California: State Internet Services Shut Down Over Hacker Intrusion
Nancy Vogel writes in The Los Angeles Times:
A hacker who directed people from a county website to pornography triggered a federal shutdown of state government Internet and e-mail service late Tuesday afternoon, according to a spokesman for Gov. Arnold Schwarzenegger.
The state system, which uses the domain name "ca.gov," was never hacked and all of its websites and e-mail should be functioning within a few hours, spokesman Aaron McLear said.
He said the federal government moved to suspend the state's Internet and e-mail service after someone hacked into a county website that contained the domain name ca.gov and redirected people to a pornography site. McLear said he did not know which county website was hacked.
The unauthorized diversion of Internet traffic to pornography raised a red flag for federal regulators, who moved to shut down the entire ca.gov domain until California officials prevailed upon them to reverse the suspension, according to McLear.
More
here.
Toon of the Day: Blood, Oil, Blackwater
Click for larger image.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Tuesday, Oct. 2, 2007, at least 3,809 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 3,105 died as a result of hostile action, according to the military's numbers.
The AP count is three higher than the Defense Department's tally, last updated Tuesday at 10 a.m. EDT.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Again Tonight: Ken Burns' The War

This documentary has, thus far, proven to be a masterpiece.
Tonight, in Episode 7: "A World Without War"
This documentary has proven to be most extraordinary.
I will definitely be buying it on DVD.
- ferg
Footnote: This is where "The Man in the Grey Flannel Suit" comes into play.
Computers, Photos for Next 'Indiana Jones' Reported Stolen

Richard Winton writes in The Los Angeles Times:
Computers and photographs for director Steven Spielberg's upcoming fourth "Indiana Jones" film were stolen, and DreamWorks Pictures has asked local law enforcement to investigate, a studio spokeswoman said.
"An investigation is being conducted by law enforcement," said Kristin Stark, a spokeswoman for DreamWorks.
Stark declined to say where and when the theft took place. Officials from the Los Angeles Police Department, the FBI and the Sheriff's Department could not immediately confirm that they were investigating.
Marvin Levy, Spielberg's spokesman, said the director was concerned that the thieves might be trying to sell the materials.
More
here.
Off Beat: Group Renames Asteroid for George Takei

An AP newswire article by Samantha Gross, via MSNBC, reports that:
George Takei already had a place among the stars in the minds of millions of "Star Trek" fans. Now he's taking up permanent residence as the namesake of the asteroid formerly known as 1994 GT9.
The asteroid, located between Mars and Jupiter, has been renamed 7307 Takei in honor of the actor, who is best known for his role as Hikaru Sulu in the original "Star Trek" series.
"I am now a heavenly body," Takei said Tuesday, laughing. "I found out about it yesterday ... I was blown away. It came out of the clear, blue sky — just like an asteroid."
More
here.
Former U.S. Cyber Security Czar Calls for 'Closed Internet'
Cade Metz writes on The Register:
"Another idea that's already been rejected that I think we should look at again is the idea of a closed internet," [Richard] Clarke said. "Why should the part of the internet that's connected to the power grid be open? Why should that part of the internet that runs nuclear laboratories be open? Why shouldn't there be a closed internet? There are already relatively closed internets - and now we need to think seriously about expanding them."
Several years ago, when Clarke suggested the idea to Vint Cerf, the internet founding father had a fit. "[He] implied he was putting together a firing squad to take me out," Clarke said.
More
here.
Quote of the Day [2]: Mike Masnick
"Clearly, Viacom's strategic sickness comes from the top -- and it's going to strangle the company as others, who actually pay attention to basic economics and trends, run rings around Viacom over time."
- Mike Masnick, writing on techdirt.com, regarding commets made in a speech by Viacom CEO Philippe Dauman.
Justice Official: Details of Surveillance Program Tightly Guarded
Dan Eggen writes in The Washington Post:
Only four top officials at the Justice Department were given access to details about a warrantless surveillance program that Justice lawyers ultimately determined was partially illegal, a former department lawyer testified today.
Jack L. Goldsmith, former head of the Justice Department's Office of Legal Counsel, told the Senate Judiciary Committee that access to the surveillance program was so tightly controlled that even the attorney general did not know all the details.
Goldsmith also testified that the White House initially resisted allowing then-Deputy Attorney General James B. Comey to be briefed on the program at a time when the Justice Department was undertaking a legal review of the effort.
More
here.
Big Cheers for Qwest: Qwest Launches Customer Internet Protection Program
Via The Consumerist.
Qwest would like you to know they've launched some fancy new "Consumer Internet Protection."
According to Qwest, the new program notifies you that your computer is infected, gives you information on how to remove the infection, and then provides you with anti-virus software.
More
here.
Note: I applaud Qwest in this endeavor -- they have taken the lead among ISPs to at least begin seriously addressing
the botnet problem.
- ferg
Quote of the Day: Stephen Colbert

"Well that is completely unfair, everyone knows that Cheney’s pipe dream is driving a bulldozer into the New York Times while drinking crude oil out of Keith Olbermann’s skull."
- Stephen Colbert, on The Colbert Report. Watch this segment here.
Image source: Crooks and Liars
U.S. Telcos Grilled Over Government Access to Records
Via Reuters.
The House Energy and Commerce Committee asked AT&T Inc., Verizon Communications Inc., and Qwest Communications International Inc. on Tuesday to describe how U.S. government agencies sought to obtain information about customers' telephone and Internet use.
Last year, it was widely reported that some big telephone companies allowed the U.S. government access to millions of customers' telephone records for an anti-terrorism program. Qwest said it refused the government's request.
More
here.
Off Beat: Titan Missile Base for Sale on eBay

Asking price: $1.5 Million.
Details here.
(Props, Crooks and Liars.)
The Economist: Learning to Live With Big Brother
Via The Economist.
It used to be easy to tell whether you were in a free country or a dictatorship. In an old-time police state, the goons are everywhere, both in person and through a web of informers that penetrates every workplace, community and family. They glean whatever they can about your political views, if you are careless enough to express them in public, and your personal foibles.
What they fail to pick up in the café or canteen, they learn by reading your letters or tapping your phone. The knowledge thus amassed is then stored on millions of yellowing pieces of paper, typed or handwritten; from an old-time dictator's viewpoint, exclusive access to these files is at least as powerful an instrument of fear as any torture chamber. Only when a regime falls will the files either be destroyed, or thrown open so people can see which of their friends was an informer.
Much more
here.
(Hat-tip: Bruce Schneier.)
Chinese Internet Security Response Team Website Hosting Malicious Content - UPDATE
Via The Register:
A recent post by the team at the Chinese Internet Security Response Team to their English-language site indicates that some of the site visitors are experiencing an attack from the CISRT.org site as a result of an injected IFRAME tag.
Injected IFRAME tags are not a new means of using legitimate sites to launch attacks on unsuspecting users, with a recent notable case being the Bank of India hack. What is different in this case is that the hack is only being served to seemingly random site visitors.
More
here.
Note: I'm wondering if it is still hosting malicious content -- there is a lot of embedded JavaScript at that site that I just don't have time right now to examine in more detail. It is my opinion that a CERT/CSIRT webpage shouldn't be a JavaScript minefield.
-ferg
Update: 12:45 PDT: WARNING: Yes, the site is still hosting malicious content at this time.
Former DOJ Lawyer Couldn't Find Way to Legalize Bush Spying Program
Ryan Singel writes on Threat Level:
Senator Patrick Leahy (D- Vermont) wasted no time in pushing former administration lawyer Jack Goldsmith about the legality of the warrantless wiretapping program. Goldsmith, who in 2004 revised the opinion giving legal cover to the program, sparked a conflagration between the Justice Department and the White House, which peaked with the Intensive Care Showdown at then-Attorney General John Ashcroft's bedside.
"Is it fair to say in your opinion the warrantless wiretapping program or at least significant parts of it were illegal or without legal basis?" Leahy asked.
"It was a legal mess," Goldsmith said. "It was the biggest legal mess I encountered there."
"I'm worried about what label we attach to programs - I will say there were certain aspects of programs related to the [Terrorist Surveillance Program] that I could not find legal support for."
That's careful lawyerese for illegal. Especially when that lawyer's job at the time was to find any reasonable basis to support the Administration's work.
Much more
here.
Recall Chinese Toys
Click for larger image.
The State Department Kills Yet Another Source of Open Source Intelligence
R.I.P: The Arms Control Otaku.
Well folks, it appears that the State Department uncovered my true identity through their background investigation. My boss asked me very politely today to put the blog on ice and I have decided to honor his request.
To be honest, I hate the idea of self-censorship, but it looks like I have no way around it while I'm a Presidential Management Fellow. I can't have my (possibly controversial) personal views to undermine the credibility of the policy advice I will dispense over the next two years.
More
here.
Sayonara.
Again Tonight: Ken Burns' The War

This documentary has, thus far, proven to be a masterpiece.
Tonight, in Episode 6: "The Ghost Front"
This documentary has proven to be be most extraordinary.
Ken Burns, Kudos.
- ferg
Never Forget: Burma
Click for larger image.
Attention DDoS Bot Masters: You Can't Always Hide
Via CastleCops.
Today the arrest and indictment [.pdf] of Greg King, 21, of Fairfield California was announced. In the Indictment, the US Attorneys Office is alleging Greg King aka SilenZ was responsible for the DDoS of CastleCops last February. According to the Press Release he faces a maximum sentence of ten years imprisonment and a $250,000 fine.
There is no “good” reason for a DDoS. Targeting an individual or an online presence can and does have far reaching effects. It is excellent to see the US Attorneys Office taking an active stance with computer crime. Hopefully this is the beginning of a new trend where computer crimes are prosecuted with vigor which would diminish the feeling that the system fails. I have to tip my hat to Law Enforcement and the US Attorneys Office on this. We never expected to see any kind of prosecution so quickly.
More
here.
Bait & Switch: The NSA Grab for Domestic Wiretap Infrastructure
Ryan Singel writes on Threat Level:
The U.S. intelligence community's attempts to clarify its complaints to Congress that the nation's privacy protections hindered the NSA's spying on Iraqis suspected of kidnapping American soldiers actually not only demonstrates the intelligence community's bureaucratic slowness, but also the breadth of the powers temporarily handed to them by Congress this summer and the misleading rhetorical tricks it will play to get that power permanently.
More here.
U.S. Toll in Iraq, Afghanistan
Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Monday, Oct. 1, 2007, at least 3,807 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 3,100 died as a result of hostile action, according to the military's numbers.
The AP count is seven higher than the Defense Department's tally, last updated Monday at 10 a.m. EDT.
As of Monday, Oct. 1, 2007, at least 375 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures Sept. 22, 2007.
Of those, the military reports 249 were killed by hostile action.
More
here and
here.And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Satire: Country Music Stars Challenge Al-Qaeda With Patriotic New Song 'Bomb New York'

Via The Onion, America's Finest News Source.
Quote of the Day: Stephen Wellman
"Does AT&T Hate The First Amendment?"
- Stephen Wellman, writing on the InformationWeek "Over the Air" Blog.
Boeing Employee Fired for Discussing Computer Security Problems
Kim Zetter writes on Threat Level:
Boeing has fired an employee for speaking to the Seattle Post-Intelligencer after the newspaper published a story in July saying that Boeing couldn't properly protect data in its computer systems from theft, manipulation and fraud. The story also suggested that the company may have misrepresented the security of its data in filings to the Securities and Exchange Commission.
The fired employee says he was trying to save the company but was treated badly after he raised ethical concerns internally about how the company was conducting security audits of its systems. He then spoke with a reporter as well as the SEC about his concerns. Now he says the company is retaliating against him, instead of trying to fix its problems. An anonymous e-mail sent to the Seattle P-I also disclosed that Boeing is spying on other employees to ferret out whistleblowers by videotaping workers and reading their e-mail.
More
here.
FTC: Cyberspace Still a Dangerous Neighborhood
William Jackson writes on GCN.com:
The Federal Trade Commission this morning kicked off National Cyber Security Awareness Month by announcing a settlement in a case against a distributor of spyware that will cost the company $330,000.
The case, against an outfit called ERG Ventures that bundled malware with seemingly innocent software such as screensavers or video files, was one of a number of actions involving online fraud and data breaches pursued by the FTC in the past two years, FTC Chairwoman Deborah Platt Majoras said at the opening of the National Cyber Security Awareness summit in Washington.
More
here.
Contested UK Encryption Disclosure Law Takes Effect
Jeremy Kirk writes on InfoWorld:
British law enforcement gained new powers on Monday to compel individuals and businesses to decrypt data wanted by authorities for investigations.
The measure is in the third part of the Regulation of Investigatory Powers Act (RIPA), legislation passed in 2000 by the U.K. Parliament to give law enforcement new investigation powers with respect to evolving communication technologies.
The government contends law enforcement more frequently encounters encrypted data, which delays investigations. But RIPA Part III wasn't activated when the act was passed due to the less prevalent use of encryption.
But as of Monday, those served with a "Section 49" notice have to either make decryption keys available or put the data in an intelligible form for authorities. Failure to comply could mean a prison sentence of up to two years for cases not involving national security or five years for those that do.
More
here.
Thought of the Day: Don't Tread on Me

Again Tonight: Ken Burns' The War

Ken Burns' fantastic and eye-opening documentary picked back up tonight, covering the massive costs of the war on both the European and Pacific fronts.
Among the topics in this episode (entitled "FUBAR"):
More
here.
At What Cost? West is Taking Fight Against Terrorism Online
Doreen Carvajal writes in The International Herald Tribune:
In the name of counterterrorism, Western countries are moving to erect online security borders with aggressive proposals to block Web sites and to unleash Trojan e-mails containing spyware that would monitor jihadists.
Critics warn that the security measures could lead to censorship and privacy invasion, but governments are pressing for legislation aimed at thwarting attacks and walling off Web sites that espouse illegal activities or are "likely to have the effect of facilitating" crime.
In early November, Franco Frattini, the EU justice commissioner, will introduce a package of anti-terrorism proposals that includes the development of technology to block Internet sites offering bomb-making recipes and to make online recruiting of terrorists a punishable offense.
Countries are already moving individually to acquire tools that would give them the ability to reach beyond national borders. In Germany, where the authorities recently foiled a planned terrorist attack, Interior Minister Wolfgang Schäuble is seeking powers to spy virtually, using e-mails that could infect recipients' computers with spy software.
More
here.
International Community Concerned Over U.S. Plan to Bomb Iran
Anne Davies writes in The Sydney Morning Herald:
Australia, Britain and Israel have "expressed interest" in a US campaign to launch "surgical" bombing raids on Iran targeting the Revolutionary Guard facilities, one of the US's leading investigative reporters, Seymour Hersh, reports.
In a lengthy article in the latest issue of The New Yorker, Hersh details how the US is making plans for a strike on Iran, beefing up intelligence resources within the CIA and shifting its rhetorical campaign in a bid to win support from the American people should the strikes proceed.
Hersh says the Administration has stopped trying to justify the campaign on the basis of curtailing Iran's nuclear ambitions, to redefining the war in Iraq as a strategic battle.
More
here.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Sunday, Sept. 30, 2007, at least 3,803 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 3,099 died as a result of hostile action, according to the military's numbers.
The AP count is five higher than the Defense Department's tally, last updated Friday at 10 a.m. EDT.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Quote of the Day: Seymour Hersh
"The real thing in the mind of this president is he wants to reshape the Middle East and make it a model. He absolutely believes it. I always thought Henry Kissinger was a disaster because he lies like most people breathe and you can't have that in public life. But if it were Kissinger this time around, I'd actually be relieved because I'd know that the madness would be tied to some oil deal. But in this case, what you see is what you get. This guy believes he's doing God's work."
- Seymour Hersh, quoted in an interview with Speigel Online.
How to Obtain Free, Detailed .name WHOIS Information - UPDATE
Via The DomainTools Blog.
Wired Magazine shows why Dot-Name’s whois policy is bad. The registry is based in the UK and they claim detailed whois violates UK privacy policy. While the UK government has never prosecuted a case against a registry based in the UK they still convinced ICANN that they should be allowed to bend the mandated whois service registries are required to run. So ICANN has allowed a special exception to the Dot-Name Registry. If you want detailed access to Dot-name whois be prepared to pay $2 for it if you go directly to the Registry. That will get you five passwords that are good for 24 hours. So I guess the UK privacy policy doesn’t apply if you make people pay for whois? I just don’t follow that argument.
Either way, I want to let people know about a special back door! You can get detailed Dot-Name whois for free.
More
here.
Note: Nice work, Jay! Thanks!
UPDATE: 17:15 PDT: So, this only works if the registrar queried in actually allows you to query their WHOIS services. I have been informed by several people that this does not always work because of this.
- ferg