U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Saturday, July 14, 2007, at least 3,613 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,967 died as a result of hostile action, according to the military's numbers.
The AP count is two more than the Defense Department's tally, last updated Friday at 10 a.m. EDT.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
California: Re-Vote Likely After E-Vote Error
Stephen Lawson writes on PC World:
A California judge is likely to order a Berkeley city initiative back on the ballot because of local officials' mishandling of electronic voting machine data, a public-interest lawyer arguing the case said Friday.
In a preliminary ruling Thursday, Judge Winifred Smith of the Alameda County Superior Court indicated she would nullify the defeat of a medical marijuana proposal in Berkeley in 2004 and order the measure put back on the ballot in a later election. A hearing on Friday morning in advance of a final ruling brought out nothing that indicated Smith would deviate from her preliminary decision, said attorney Gregory Luke, who is representing Americans for Safe Access. The medical-marijuana advocacy group is suing the county, assisted by the technology rights group Electronic Frontier Foundation.
The case points to the dangers of electronic voting systems, which make it harder to ensure fair elections, Luke said. Electronic voting machines have been widely adopted in the U.S. since the disputed presidential election of 2000. Laws in California and some other states now require paper records of all votes, but the California law wasn't in place for the Berkeley election.
More
here.
Man Convicted in Plot to Blow Up U.S. Pipelines
An AP newswire article, via MSNBC, reports that:
A man who claimed he had been trying to root out terrorists on the Internet was convicted Friday of plotting to help a supposed al-Qaida operative blow up U.S. oil pipelines and refineries.
A federal jury took only 90 minutes to convict Michael C. Reynolds of providing material support to terrorists and other charges.
Reynolds, 49, of Wilkes-Barre, was arrested in December 2005 after authorities said he tried to meet someone he thought was an al-Qaida contact about 25 miles from a motel in Pocatello, Idaho, where he had been staying. The contact turned out to be Shannen Rossmiller, a judge from Conrad, Mont., who was working for the FBI.
More
here.
Internet Jihad: A World Wide Web of Terror

Via The Economist.
By his own admission, he never fired a single bullet or “stood for a second in a trench” in the great jihad against America. Yet the man who called himself “Irhabi007”—a play on the Arabic word for terrorist and the code-name for James Bond—was far more important than any foot soldier or suicide-bomber in Iraq. He led the charge of jihad on the internet.
In doing so, Irhabi007 was a central figure in enabling al-Qaeda to reconstitute itself after the fall of the Taliban and its eviction from Afghanistan. Al-Qaeda (“the base”) and its followers moved to cyberspace, the ultimate ungoverned territory, where jihadists have set up virtual schools for ideological and military training and active propaganda arms.
Irhabi007 pioneered many of the techniques required to make all this happen. He was a tireless “webmaster” for several extremist websites, especially those issuing the statements of the late Abu Musab al-Zarqawi, the leader of al-Qaeda in Iraq. Intelligence agencies watched powerlessly as Irhabi007 hacked into computers, for instance appropriating that of the Arkansas Highway and Transportation Department to distribute large video files, and taught his fellow cyber-jihadists how to protect their anonymity online.
Despite his celebrity, this was not good enough for Irhabi007. “Dude,” he complained to a fellow cyber-jihadist (who called himself “Abuthaabit”) during one encrypted web chat, “my heart is in Iraq.”
More
here.
Image source: The Economist
Shame, Shame: White House Cites 'Confidentiality' Over Tillman Death
 Fallen U.S Army Ranger, and former NFL Player, Pat Tillman.
Fallen U.S Army Ranger, and former NFL Player, Pat Tillman.An AP newswire
article, via
MSNBC, reports that:
Two influential lawmakers investigating how and when the Bush administration learned the circumstances of Pat Tillman’s friendly-fire death and how those details were disclosed accused the White House and Pentagon on Friday of withholding key documents and renewed their demand for the material.
The White House and Defense Department have turned over nearly 10,000 pages of papers — mostly press clippings — but the White House cited “executive branch confidentiality interests” in refusing to provide other documents.
House Oversight Committee Chairman Henry Waxman, D-Calif., and Tom Davis, R-Va., the committee’s top-ranking Republican, said Friday the documents were inadequate. They insisted that the Defense Department turn over the additional material by July 25 and asked that the White House do likewise.
More
here.
Indian Doctor Charged in U.K. Terror Plot... Over SIM Card
An AP newswire article, via MSNBC, reports that:
Australian federal police charged an Indian doctor with providing support to a terrorist organization Saturday, allegedly linking him to last month’s failed British bombings.
Muhammad Haneef, 27, is the second person to be charged over the botched attacks on London and Glasgow on June 29 and 30. The other is Bilal Abdullah, who is being held in London on charges of conspiring to set off explosions.
Haneef “has been charged with providing support to a terrorist organization,” police said in a statement. The maximum penalty is 15 years in prison.
More
here.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Friday, July 13, 2007, at least 3,610 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,967 died as a result of hostile action, according to the military's numbers.
The AP count is one less than the Defense Department's tally, last updated Friday at 10 a.m. EDT.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Los Alamos Lab May Face $3.3M Fine for Data Leak
An AP newswire article by H. Josef Hebert, via MSNBC, reports that:
The Energy Department proposed $3.3 million in fines Friday against managers of the Los Alamos nuclear weapons lab because of a security breakdown in which classified documents were found in a trailer-park drug raid.
The civil penalties, the bulk of them levied against the University of California, the longtime former manager of the lab, were the largest such fines the department has ever imposed.
The enforcement action stems from an incident in October 2006, when police found more than 1,000 pages of classified documents and several computer storage devices in a trailer occupied by a former worker at the lab.
More
here.
Praying for Divine Intervention Against Registerfly
Bret Fausett:
From New Orleans' NOLA.com:
"Ticket sales for the Randy Travis concert to be held at the Castine Center in Mandeville Sunday abruptly halted Wednesday when the ticketing portal at cornerstonecares.com was hijacked by a domain name registration company operating as Registerfly.com.
Cornerstone Church pastor Doug Gilford said he is disheartened.... 'It is a travesty to have such a great opportunity as the Randy Travis concert thwarted by a company's total disregard for others. I am praying that God will show his might at this 11th hour for us,' Gilford said."
More
here.
Wiretap Compliance Countdown: ACLU's Subpeona Checklist

Via The ACLU.
On June 27, Senate Judiciary Committee Chairman Patrick Leahy issued subpoenas to the White House, Vice President and the Justice Department for documents about warrantless surveillance. The deadline for compliance is July 18.
It's been a year and a half since we first found out that our own government has been tapping our phones and reading our emails. In that year and a half, the Senate Judiciary Committee has asked the Bush Administration nine times for information about the NSA's illegal spying.
The committee is now asking for the tenth time and has rightly chosen to use its subpoena power to compel an answer. It is high time we found out how our privacy was violated and whether our private information has been used against us. It's time that Congress step up and get answers. Polite requests for information have been ignored.
Congress has now brought its power to bear, subpoenaed the legal underpinnings of the program, and has begun the process of determining exactly what the government did and who should be held responsible. The White House should take note that this is how you run a thorough and legal investigation - in the open and with proper authorization.
More
here.
(
Props, Threat Level.)
Picture of the Day: Airport Security

Props, Bruce Schneier, sirbrett84.
U.S. Government Seeks Broader Tech Snooping Powers
Lisa Vaas writes on eWeek:
The Bush administration is itching to update a snooping law to encompass new technologies, even as a DOJ report shows the FBI is using data mining on a dizzying array of U.S. citizens' non-terrorist activities: Think auto insurance fraud and Medicare claims abuse.
"Today, cellular phones are the size of credit cards, you would be hard-pressed to find a computer with memory less than 512 megabytes and our greatest threats are independent transnational terrorists and terror networks," complained Michael McConnell, director of national intelligence, in a May 2007 column published by the Washington Post.
The law that McConnell and others in the Bush administration want to overhaul is FISA, the 1978 Foreign Intelligence Surveillance Act. The law, originally drafted to prescribe physical and electronic surveillance and spying procedures on foreign powers, came under scrutiny after the New York Times in 2005 chronicled the Bush administration's order for warrantless domestic wiretapping—called the Terrorist Surveillance Program—subsequently carried out by the National Security Agency, following the terrorist attacks of 9/11.
Critics have crossed party lines to accuse the Administration of criminally violating FISA with the Terrorist Surveillance Program. The Bush administration has admitted that it flaunts FISA, claiming that the act is an unconstitutional infringement on executive power and that Congress implicitly amended FISA when it passed the Authorization for Use of Military Force on Sept. 18, 2001.
The Adminstration may well scorn FISA, but it still wants to see it overhauled to cover modern technologies.
More
here.
LOBSTER’s Catch Offers Security Research Opportunity
Via TERENA News.
A selection of files is now available to researchers interested in evaluating cyber-attack detection methods, or in studying data from real life attacks.
The attack trace files can be downloaded from a website created as a spin-off of the LOBSTER pilot project, which has been monitoring Internet traffic across Europe since October 2004.
LOBSTER has captured more than 40,000 Internet attacks using 36 passive monitoring sensors deployed in nine different countries. It was a step towards an advanced European infrastructure that will improve our understanding of the Internet and help solve performance and security problems.
The full details of these thousands of attacks cannot be made public because of privacy issues. A very small sample has been carefully anonymised, using software developed by the LOBSTER team, in order to remove sensitive information that could identify either the source or the destination of each attack. This sample is accessible through the LOBSTER attack trace repository.
More
here.
ATM Reprogramming Caper Hits Pennsylvania

Kevin Poulsen writes on Threat Level:
Police in Derry, Pennsylvania are baffled by a June ATM robbery in which an unidentified man wearing flip flops and shorts strolled into Mastrorocco's Market and reprogrammed the cash machine to think it was dispensing dollar bills instead of twenties.
Along with a female accomplice, the crook netted over $1,540 in two visits on June 19 and 20, according to store owner Vince Mastrorocco. "They came in, they hit me the first day -- a man and a woman -- and they cleaned me out," Mastrorocco told THREAT LEVEL. "Then they came back the next day and cleaned me out again."
A sergeant with the Derry Borough Police Department they're still investigating the crime, and no arrests have been made.
Of course, THREAT LEVEL readers know exactly what happened. The machine was a Triton 9100, and like competitor Tranax, Triton printed its default administrative passcodes in its ATM service manuals, which have been widely available online.
More
here.
Image source: American Vending Sales, Inc.
AT&T and Verizon Balk at 'Open Access'
Barry Levine writes on CIO Today:
The battle over open access to the wireless spectrum that will be auctioned off in January heated up this week, with AT&T and Verizon Wireless attacking the concept.
The concept of open access is emerging as a key issue for the rules, now being drawn up, that will govern the spectrum in the 700-MHz bands. Among other things, open access would mean allowing any device or service to use the auctioned bandwidth, rather than locking wireless devices to specific carriers, as is currently done in the U.S.
According to news reports, AT&T sent a letter to the FCC this week, attacking Google's position to support open-access rules, including the provision that any reseller would be able to buy wireless services from the winning 700-MHz licensee on a wholesale basis.
If big carriers won the auction, Google had cautioned in a similar letter sent to the FCC, "they would probably use it to protect their existing business models and thwart the entry of new competitors." Google has joined with other companies and organizations in asking for open access.
More
here.
Eighty Percent of Success is Just Showing Up

Props, Military Motivator.
Media Defender Buys P2P.net: Preparing for their Next Scam?
Via TorrentFreak.
The infamous anti-piracy organization Media Defender recently bought the P2P.net domain. Currently P2P.net redirects to Google and at this point it is still unclear what their plans are for the domain. However, it is likely that they will use it for one of their pirate traps such a the fake video download service Miivi or the fake BitTorrent trackers they run.
P2P.net (not P2Pnet.net) was up for auction at eBay earlier this year. Initially it wasn’t sold because the original owner wanted a higher price for the domain. It turns out that Media Defender was one of the interested parties, and they probably paid thousands of dollars to get the domain in their possession. Because of the huge amount of money that’s involved it is not likely that the domain will stay unused for a long time.
Last week we discovered that Media Defender actively tried to lure people into downloading blockbuster movies from their fake download site, Miivi.com. As expected, only a few hours after we made the news public the site was taken offline.
More
here.
The New Black: The iPhone's BSOD
Kevin Ho writes on the C|Net News Blog:
Being a PC person, I've encountered the dreaded "blue screen of death."
I've never seen a comparable thing on Apple products. (I have heard of the sad Mac face, or the sick iPod face.) So, much to my surprise, starting a couple days ago I noticed what appeared to be a "black screen of death."
Everything stops working. The time bar at top is there, but the rest of the screen is black. No touching. No prodding of the home key. No pressing of the upper right key will get the thing working again.
More
here.
Contractor Caught Trying to Sell Disney Data
Bob Sullivan writes on The Red Tape Chronicles:
An employee who works for the company that processes Disney Movie Club transactions was caught trying to sell customer credit card information, Disney told its customers this week. The story echoes an incident revealed by Fidelity National Information Services earlier this month.
The employee was nabbed in an "undercover sting operation" run by a federal law enforcement agency, according to a letter sent July 6 by the Disney Movie Club to its members.
The employee did not work for Disney, but rather for Alta Resources Inc., which processes transactions and fulfills orders for the Disney Movie Club, the letter said. The employee has been dismissed and the Secret Service is continuing to investigate, according to Disney.
More
here.
Oracle UK Systems Accused in 'SSH Hacking Spree'
John Leyden writes on The Register:
Compromised computers at Oracle UK are listed among the 10 worst offenders on the net for launching attacks on servers which run SSH (secure shell) server software.
Oracle said it is investigating the reported problem, which it is yet to either confirm or refute.
A box (or group of boxes behind a proxy) at Oracle UK is among the worst offenders for launching attacks, according to statistics from servers running DenyHosts software to block SSH brute-force password attacks.
DenyHosts is a script for Linux system administrators designed to help thwart SSH server attacks. Around 6,800 users contribute to the data it collects.
More
here.
Toon of the Day: Fine Tuning
Click for larger image.
U.S. Goverment Struggles with Data Security

David Perera writes on CIO Today:
Security measures are restrictive by definition. They place barriers where once there was free-flowing traffic. They demand immediate attention from users who probably would prefer to do anything else but reconfirm their identity.
"We hear the complaints about things slowing down," acknowledges an information security officer at an agency deploying new encryption measures. But, he adds, "we don't care."
More
here.
(
Props, Flying Hamster.)
Man's Quest for $10 AT&T DSL Ends in Success... Kinda
 The New AT&T
The New AT&T
Joshua Topolsky
writes on
Engadget:
Mark "Rizzn" Hopkins' internet ordeal is over, and he has detailed all the painful, laborious, and clearly unnecessary steps needed to put yourself into Cashville with AT&T's cheap-o DSL service over on his website.
In the end, the poor guy spoke with what appears to be hundreds of the company's employees, had to "pay" $79.99 for a router (although they offer a mail-in rebate reimbursement), and forked over $50 for AT&T's "activation fee", yet still technically doesn't have service.
Regardless, when he's paying a measly $10 $18 a month for his phone and DSL service, and you're still Go-Go dancing on weekends just to cover your voicemail charge, who will really have the last laugh?
More
here.
Gapingvoid: Power
Via gapingvoid.com. Enjoy!
Copper Thefts Trigger Widespread Crackdown
Kathleen Haughney writes on Stateline.org:
A Texas legislator made headlines this week for shooting a man allegedly stealing copper pipes from a new home the lawmaker is constructing. Copper theft is so rampant that 20 states — including Texas — passed laws this year to try to squelch shady scrap-metal sales.
As the value of copper, aluminum and other scrap metals has risen in the past two years, so have complaints from homeowners and businesses about gutters stolen, air conditioners torn apart and cars tampered with by criminals seeking to salvage the metal and earn some quick cash. More than half of the states considered legislation this year to combat the reselling of stolen metals, according to the Institute of Scrap Recycling Industries, an industry trade group.
More
here.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Thursday, July 12, 2007, at least 3,610 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,967 died as a result of hostile action, according to the military's numbers.
The AP count is one less than the Defense Department's tally, last updated Thursday at 10 a.m. EDT.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
A Perfect Home for Secret Government Projects
 The Homestake Mine today.
The Homestake Mine today..
All top-secret government labs are either buried underground or hidden deep in a mountain. Everyone knows that, which is what makes the National Science Foundation’s recent announcement that it plans to convert the Homestake Mine, the deepest of its kind in the U.S., into a research facility, so surprising. How can it possibly be top secret if they’re telling everyone? The only answer, of course, is that they really are going to conduct legitimate research in astrophysics, biology and geology.
The Homestake Mine, located in Lead, South Dakota, extends 8,000 feet down into the Earth and has over 375 miles of tunnels. It already has a rich scientific history: In 1965, physicist Raymond Davis led a team that set up the world’s first underground solar neutrino detector in a cavern deep in the mine, and eventually earned the Nobel Prize for his work. Scientists at the new lab will also pursue astrophysics research, along with work on carbon sequestration, organisms living in extreme conditions and geophysics. Over the next 30 years, two laboratories will be constructed. One will extend down to 4,800 feet, and the other will lie all the way down at 7,400 feet. We’re guessing that’s where they’ll hide the aliens.
More
here.
Image source: Legends of America
Mounting Scrutiny for Google Security
Via InfoWorld.
Much as the ubiquity of Microsoft's Windows operating system and Office productivity tools has made the software giant a focal point of security research, search giant Google is facing new scrutiny as it diversifies its products and moves further into the business environment.
In a report to be published on July 16, researchers at Ponemon Institute will detail their findings about existing concerns among IT professionals regarding the overall security of Google Desktop, the company's PC search utility, specifically within the confines of business operations.
And while the research revolves around the only significant security flaw to be unearthed in the program thus far -- a cross site scripting vulnerability reported and subsequently patched by Google in February -- authors of the report contend that their work illustrates a growing level of concern over the massive company's rapidly-expanding footprint.
More
here.
The Rise of Anti-Forensics
Scott Berinato writes on WhiteHat Security:
Computer crime has shifted from a game of disruption to one of access. The hacker’s focus has shifted too, from developing destructive payloads to circumventing detection. Now, for every tool forensic investigators have come to rely on to discover and prosecute electronic crimes, criminals have a corresponding tool to baffle the investigation.
This is antiforensics. It is more than technology. It is an approach to criminal hacking that can be summed up like this: Make it hard for them to find you and impossible for them to prove they found you.
More
here.
Australia: Police Got Sensitive Student Data Just By Asking
Edmund Tadros writes in The Sydney Morning Herald:
The University of Sydney has provided confidential student information to law enforcement officials without demanding a warrant, subpoena or even an explanation.
Documents show university officials were willing to supply the details based on little more than emails or faxes from officers that stated they wanted the information. Twenty requests for information related to criminal matters have been received by the university since 2004, according to documents obtained under freedom of information laws.
The agencies involved include NSW Police, the Crime Commission and the Australian Federal Police. There are exemptions under the Privacy and Personal Information Protection Act 1998 for law enforcement organisations but civil libertarians say these agencies should be obtaining subpoenas and warrants before demanding private information from universities.
More
here.
Quote of the Day [2]: Larry Greenemeier
"A recent Government Accountability Office report noted the difficulty of linking data theft to identity theft, but the U.S. Secret Service is having no such problems."
- Larry Greenemeier, writing in InformationWeek, on the arrests and indictments earlier this week of four members of an organized fraud ring in South Florida, and the Secret Service has been able to trace the origin of the data used to perpetrate this identity theft and fraud back to the theft of millions of customer records from T.J. Maxx parent company TJX and from Polo Ralph Lauren.
Verizon Signs Florida Anti-Cramming Agreement
Via ConsumerAffairs.com.
Verizon is the latest telephone company to sign an anti-cramming settlement with the state of Florida.
The company agreed to develop an early warning system designed to identify third-party companies that may attempt to place unauthorized charges on consumers’ phone bills.
Embarq, once part of Sprint, signed a similar agreement with Florida last month and AT&T agreed to similar terms earlier. Verizon has more than 40 million access lines inside the coverage region affected by the agreement.
The practice known as “cramming” occurs when unauthorized charges are added to phone service bills without the consumer’s knowledge or consent.
More
here.
Quote of the Day: Larry Seltzer
"When I heard about the Google-Postini deal the first thought I had was about how Google would have a field day mining all the data that Postini filters."
- Larry Seltzer, Senior Security Editor at eWeek, commenting on the acquisition of Postini by Google.
Picture of the Day: Gut Feeling Threat Level

Props, Threat Level.
UK: Experian Rrejects ID Theft Notification Proposal
Joe Fay writes on Channel Register:
Anna Fielder, policy consultant at the National Consumer Council, said the UK should follow the example of California, where companies who expose individuals’ data have to contact and notify the individuals concerned.
She added that the UK should adopt another US trend, where customers have the right to lock or freeze their credit records, with companies only able to access records on the individual’s say so.
However, Gillian Key-Vice, Experience’s director of regulatory affairs, rejected the idea of a notification scheme.
Key-Vice said that while she recognised why people might “think it’s a good idea”, such a scheme could cause “unnecessary concern” amongst individuals where a breach has already been “managed”.
More
here.
SCADA Watch: Utility Firms Sitting on Hacking Time-Bomb
Iain Thomson writes on vnunet.com:
Utility companies could be facing a hacking time bomb owing to poor security measures.
As more utilities move control and billing systems online an analyst has warned that hackers are increasingly turning their attention to the possibilities of controlling the systems.
While there is little direct financial benefit in breaking into such systems, there may be other benefits.
"The utility companies are moving to completely digital systems and security is not prioritised," said Fran Howarth, partner at analyst firm Hurwitz & Associates.
More
here.
Note: This is something that I have been warning about for several years now, and for exactly the same reasons as outlined in this article.
- ferg
National Government Servers Hosting Phishing Sites
Nick Sullivan writes on the Symantec Security Response Blog:
In recent months, Symantec has detected a number of phishing sites that have been hosted on government URLs. In June alone, phishing sites were identified on government sites from the following countries: Thailand (.go.th), Indonesia (.go.id), Hungary (.gov.hu), Bangladesh (.gov.bd), Argentina (.gov.ar), Sri Lanka (.gov.lk), Ukraine (.gov.ua), China (.gov.cn), Brazil (.gov.br), Bosnia and Herzegovina (.gov.ba), Columbia (.gov.co), and Malaysia (.gov.my).
This might come as a surprise to some people, as governments are thought to have very secure computer systems. However, the quantity of phishing sites hosted on government domains around the world seems to suggest otherwise.
More
here.
Note: While this is not really news to anyone working in the security industry, it may indeed be news to others outside of those circles. It does, however, illustrate that the state of website security is amazingly poor these days, and websites that appear to be "official" are not immune to compromise if they implemented poorly and/or insecurely.
- ferg
Israel: Internet Censorship Could Start Within a Year
Eran Gabay writes on Haaretz.com:
Internet censorship in Israel will start in about a year. The law, proposed by Amnon Cohen of Shas and unanimously approved on Sunday by the Ministerial Committee on Legislation, will now be brought to the Knesset floor.
Senior officials in the Communications Ministry forecast that it will take seven to ten months to prepare for implementing the provisions once the law passes.
The proposed law would require Internet Service Providers (ISP) to only allow access to Internet sites featuring pornography, gambling and violence to those over 18 who specifically sign up for such access and identify themselves as adults.
The cost of implementing the bill is estimated at about NIS 10 million, based on figures provided by networking giant Cisco to the ministry at its request, TheMarker has learned.
More
here.
FBI: Expect More Spam Prosecutions
Grant Gross writes on InfoWorld:
U.S. Internet users should expect a growing number of prosecutions for sending spam and related activities, such as creating botnets, officials with two U.S. law enforcement organizations said Thursday.
The U.S. Federal Bureau of Investigation has 70 active investigations into spam-related crimes, said FBI special agent J. Keith Mularski, speaking at the U.S. Federal Trade Commission's spam summit. The FBI has worked with the National Cyber-Forensics and Training Alliance (NCFTA), a partnership between law enforcement agencies, universities, and private businesses, to identity spammers, he said.
The NCFTA, launched in 2002, has identified more than 100 "significant spammers," including five tied to traditional organized crime, Mularski said.
More
here.
FBI Employees Face Criminal Probe Over Patriot Act Abuse
Ryan Singel writes on Wired News:
FBI personnel who used misleading emergency letters to acquire thousands of Americans' phone records are the subject of a criminal investigation, top bureau officials told civil liberties groups Monday.
The unprecedented criminal probe, revealed at an outreach meeting led by FBI director Robert Mueller and general counsel Valerie Caproni at FBI headquarters, is looking at the actions of an antiterrorism team known as the Communications Analysis Unit, according to two people who attended the meeting independently and who informed Wired News, requesting anonymity.
The privately disclosed investigation would mark the first time government officials have faced possible prosecution for misuse of Patriot Act investigative tools, and highlights the seriousness of recent reports about the FBI's misuse of a powerful self-issued subpoena known as a National Security Letter.
More
here.
Sony BMG Sues CD Rootkit Software Firm
An AP newswire article, via The Hollywood Reporter, reports that:
Sony BMG Music Entertainment is suing a company that developed antipiracy software for CDs, claiming the technology was defective and cost the record company millions of dollars to settle consumer complaints and government investigations.
Sony BMG filed a summons in a New York state court against The Amergence Group Inc., formerly SunnComm International, which developed the MediaMax CD copy-protection technology.
Sony BMG is seeking to recover some $12 million in damages from the Phoenix-based technology company, according to court papers filed July 3.
The music company accuses Amergence of negligence, unfair business practices and breaching the terms of its license agreement by delivering software that "did not perform as warranted."
In a statement, The Amergence Group vowed to fight what it described as unwarranted allegations by Sony BMG.
More
here.
Hackers Focusing on Web 2.0 Sites (plus Comment)
Rene Millman writes on ITPro News:
Virus writers are turning their attention to social networking sites and other user-generated content networks to steal personal information and create botnets, according to an anti-virus expert.
Toralv Dirro, security strategist at IT security company McAfee's Avert Labs research team said that over the last ten years the threat landscape had changed beyond recognition and that hackers were now looking at attacking new web 2.0-style sites as they were rich in sensitive data.
"Malware is getting more commercial. We expect new platforms and applications to be attacked if there is any money to be made out of it," he said. "As users can just about post anything, so can hackers. We have seen many examples of profile pages containing malware that then get downloaded by victims."
Dirro pointed to an example of a worm that attacked Wikipedia users visiting a booby-trapped page created by hackers. The page was used to trick users into downloading malware thinking it was fix for the Blaster worm last year. It was just the start of a new trend in viruses.
"Web 2.0 sites are becoming more popular and I expect more worms to appear on these sites," said Dirro.
More
here.
Note:This should not really be news to anyone. But if it is, allow me to comment.
We've been saying for over 10 years that JavaScript, in and of itself, can be used for extremely evil shit. And since most of the newer, mash-up-style Web "Uh-Oh' stuff uses AJAX and requires users to open themselves up for JavaScript exploitation just to experience the content.
Having said that, this particular message [in this article] is something that I (and many others) have been saying for years -- and in fact led me to start calling some of the underlying mechanisms in "Web 2.0" as "Web Uh-Oh" with regards to their impact on network, and consumer, security.
I am in the process of writing a white paper on this topic which I'll let you know about when it its completed, but in the meantime I'll say this:
We (as the Internet-community-at-large) are doing a really fine job of allowing our customers to be exploited by enabling the very same technologies that deliver the very same "content-rich"
features that they want.
The real issue here is not that more "worms will appear on Web 2.0 sites", but rather, more worms and malware will appear which take advantage of the fact that most users & consumers are ripe to be exploited -- simply by the fact that if they protect themselves properly against these types of exploits, they cannot enjoy the "features" of this content-rich Web 2.0 Internet that we know and love today.
- ferg
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Wednesday, July 11, 2007, at least 3,610 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,966 died as a result of hostile action, according to the military's numbers.
The AP count is one less than the Defense Department's tally, last updated Wednesday at 10 a.m. EDT.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Why Silicon Valley has to break the Telco/Cable Comms Cartel
Tom Foremski:
Silicon Valley is teeming with established companies and startups whose services and products require communications services.
Some of the startups are called Web 2.0 companies, or social networking companies, social media companies etc. It doesn’t really matter what they are called, they all require a communications component to unlock the value they create.
This is also true for Silicon Valley’s largest companies such as Google and Cisco, they are all increasingly reliant on being able to quickly get to their end user.
Whether it is a text message, or email, or sharing a video clip, or a myriad other many-media forms of communications–they all have to go through one of the big telecommunications or cable companies.
Last mile = Gold Mile.
More
here.
Feds Pushing States on Gun Database
John Gramlich writes on Stateline.org:
Following the deadliest mass shooting in U.S. history at Virginia Tech on April 16, Congress and the Bush administration are mounting a campaign to get states to participate in a federal program designed to keep the mentally ill from buying firearms.
Only 22 states, including Virginia, now provide records of those with disqualifying mental health histories to the National Instant Criminal Background Check System (NICS), an FBI database that lets gun dealers across the country identify potentially dangerous buyers before selling them weapons.
The database, set up by Congress as part of the 1993 Brady Handgun Violence Prevention Act, essentially serves as a registry of those prohibited from buying guns for reasons ranging from illegal residence in the United States to dishonorable discharge from the armed services. In the case of the mentally ill, the law bans sales to those “who have been adjudicated as a mental defective or have been committed to a mental institution.”
More
here.
Illinois Puts Pizazz Back in PKI?
Ellen Messmer writes on NetworkWorld:
In 1999 Illinois placed a big security bet on public-key infrastructure for e-commerce, but three years ago its PKI project faltered as state agencies foundered badly when issuing the digital certificates to citizens.
It wasn’t supposed to turn out that way. The state’s landmark Electronic Commerce Security Act had given digitally signed documents an equal legal status to wet-signature paper ones in 1999, putting Illinois on the cusp of the PKI revolution. “Over the next 18 months we hope to distribute over a million digital IDs to citizens and businesses to enable them to do business with the state of Illinois as an integrated secure Web-driven government,” proclaimed then-Governor George Ryan.
More
here.
Note: This is worth watching -- even a small push in the PKI space to gain some traction would be a great thing.
- ferg
Holy Crap Alert: GAO Stings Nuclear Agency; Obtains License to Buy Radioactive Materials

Brian Ross and Joseph Rhee report on ABC News' "The Blotter":
To start, the investigators set up a dummy construction company that in reality was no more than a mail drop in Martinsburg, W.Va.
Twenty-eight days and no questions from the Nuclear Regulatory Commission later, the "company" received a license to legally buy certain quantities of Americium-241 and Cesium-137.
"It was much too easy, much too easy, to get the licenses that would have allowed individuals setting up a dummy corporation to obtain enough material to create a dirty bomb," said Sen. Norm Coleman, R-Minn., who initiated the investigation in his role as ranking member of the Senate Permanent Subcommittee on Investigations.
More
here.
Canada: Probe Finds Phone Companies Failed to Protect Customers' Personal Data
Via CBC News.
An investigation by Canada's federal privacy watchdog has found that three telephone companies failed to protect customers from data brokers mining for personal information.
The Office of the Privacy Commissioner said Tuesday that Bell Canada, Telus Mobility and Fido did not provide adequate training to staff, allowing a data broker to gain unauthorized access to customers' phone records.
The OPC found that Locatecell.com, a U.S.-based data broker that sells telephone records, was able to fool customer service agents into providing customers' confidential information.
More
here.
Sound familiar?
Boeing Employee Charged With Stealing 320,000 Sensitive Files
Sharon Gaudin writes on InformationWeek:
A disgruntled Boeing employee was charged Tuesday with 16 counts of computer trespass for allegedly stealing more than 320,000 company files over the course of more than two years and leaking them to The Seattle Times.
Gerald Lee Eastman, who was a quality assurance inspector at Boeing at the time of the thefts, is slated to be arraigned on July 17, according to a spokesman for the King County Prosecuting Attorney's Office. He faces up to 57 months in prison if convicted on all counts.
According to a criminal complaint, a search of Eastman's home found computers and storage devices containing more than 320,000 pages of "very sensitive" documents related to Boeing's business operations. Boeing estimated in an arrest report that if only a portion of the stolen documents were given to competitors, it could cost the company between $5 billion and $15 billion.
Eastman used what prosecutors called his "unfettered access to Boeing systems" to download large amounts of data from information stores he had no legitimate reason for accessing, according to the criminal complaint. He allegedly transferred the information to a thumb drive and then removed it from company property.
More
here.
U.S. Military Files Left Unprotected Online
An AP newswire article by Mike Baker, via PhysOrg.com, reports that:
Detailed schematics of a military detainee holding facility in southern Iraq. Geographical surveys and aerial photographs of two military airfields outside Baghdad. Plans for a new fuel farm at Bagram Air Base in Afghanistan.
The military calls it "need-to-know" information that would pose a direct threat to U.S. troops if it were to fall into the hands of terrorists. It's material so sensitive that officials refused to release the documents when asked.
But it's already out there, posted carelessly to file servers by government agencies and contractors, accessible to anyone with an Internet connection.
In a survey of servers run by agencies or companies involved with the military and the wars in Iraq and Afghanistan, The Associated Press found dozens of documents that officials refused to release when asked directly, citing troop security.
More
here.
British ISPs Stand Firm After File-Sharing Ruling
David Meyer writes on C|Net News:
A group representing Internet service providers in the U.K. has reasserted that ISPs should not be responsible for illegal file-sharing that takes place over their networks.
Speaking Wednesday in the wake of a recent ruling in a Belgian court, a representative of the Internet Service Providers' Association maintained that ISPs should not be "set up to play judge and jury" over alleged copyright infringement.
More
here.
Consultant Sentenced To 5 Years In Jail For Stealing Customer Information
Sharon Gaudin writes on InformationWeek:
A business software consultant who stole identifying information on more than 110,000 people from the insurance company he was working for was sentenced to five years in federal prison this week.
Binyamin Schwartz, 28, of Oak Park, Mich., was sentenced to 60 months on charges of identity theft, aggravated identity theft, access device fraud, and wire fraud. According to a report from the U.S. Attorney's Office, Schwartz admitted to investigators that he stole Social Security numbers and related information from two databases within Wisconsin-based Sentry Insurance Company while he was working as a consultant for them, developing business software.
More
here.
Australia Bankers Association: Australia Safe From NZ Banking Code
Brett Winterford and Liam Tung write on ZDNet Australia:
The Australian Bankers Association says it won't be following New Zealand's lead after its Kiwi peer opted to make users of online banking held liable for Internet fraud.
Earlier this month, The New Zealand Banking Association introduced its 2007 Banking Code of Practice, which leaves customers potentially liable for losses when cheated of their funds by online fraudsters.
If customers of New Zealand banks fail to update their operating system, antivirus, firewall, anti-spyware and anti-spam, or if they fail to follow procedures outlined by the bank, they may find themselves liable if they fall victim to Internet banking fraud.
The changes also allow Kiwi banks to request access to customers' computers to verify standards have been met in cases of fraud. The code states: "If you refuse our request for access then we may refuse your claim."
More
here.
U.S. Toll in Iraq, Afghanistan
Via The Boston Globe (AP).
As of Tuesday, July 10, 2007, at least 3,609 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,966 died as a result of hostile action, according to the military's numbers.
The AP count is the same as the Defense Department's tally, last updated Tuesday at 10 a.m. EDT.
As of Tuesday, July 10, 2007, at least 345 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures June 30, 2007.
Of those, the military reports 224 were killed by hostile action.
Outside the Afghan region, the Defense Department reports 61 more members of the U.S. military died in support of Operation Enduring Freedom.
More
here &
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
FBI Plans (Yet Another) Initiative To Profile Terrorists - UPDATE
Ellen Nakashima writes in The Washington Post:
The Federal Bureau of Investigations is developing a computer-profiling system that would enable investigators to target possible terror suspects, according to a Justice Department report submitted to Congress yesterday.
The System to Assess Risk, or STAR, assigns risk scores to possible suspects based on a variety of information, similar to the way a credit bureau assigns a rating based on a consumer's spending behavior and debt. The program focuses on foreign suspects but also includes data about some U.S. residents. A prototype is expected to be tested this year.
Justice Department officials said the system offers analysts a powerful new tool for finding possible terrorists. They said it is an effort to automate what analysts have been doing manually.
"STAR does not label anyone a terrorist," the report said. "Only individuals considered emergent foreign threats (as opposed to other criminal activity such as U.S. bank robbery threats) will be analyzed."
Some lawmakers said, however, that the report raises new questions about the government's power to use personal information and intelligence without accountability.
More
here.
UPDATE: 00:16 11 July 2007: An AP newswire article, via
MSNBC, with additional details can be found
here.
Quote of the Day: The Global Attitudes Project
"Global distrust of American leadership is reflected in increasing disapproval of the cornerstones of U.S. foreign policy."
- A passage from a new report from The Global Attitudes Project, as quoted in this blog post by W. David Stephenson.
GSA, Sun, and More Questions To Come
Robert O'Harrow Jr. writes on Government Inc.:
The troubles with the General Services Administration's contract with Sun Microsystems became well known this spring.
Investigators for Rep. Henry A. Waxman, the Democratic Chairman of the House Oversight and Government Reform committee, turned up evidence in documents and interviews that appeared to show that the giant software maker had overcharged taxpayers for years.
The amount of alleged gouging -- involving charging the government more than the private sector for the same stuff -- could be tens of millions.
More
here.
Accuser Says Web Site Has X-Rated Link
Brad Stone writes in The New York Times:
Parents and child safety experts concerned about the online activities of teenagers have been particularly nervous about a Web site called Stickam, which allows its 600,000 registered users, age 14 and older, to participate in unfiltered live video chats using their Web cameras.
But those Internet safety advocates might be even more anxious if they knew of Stickam’s close ties to a large online pornography business.
More
here.
Google Helps Bumbling Burglars Steal $12K
R. Scott Rappaold writes in The Colorado Springs Gazette:
The two burglars had door keys, pass codes and combinations for the safes at a Colorado Springs indoor amusement center.
But when it came to actually opening a combination lock, they did what most of us do when we’re stumped — they called Google to the rescue.
The burglary at Bigg City, formerly Mr. Bigg’s Family Fun Center, turned into a comedy of errors early June 10. The burglars tried to disable a security camera by repeatedly spraying it with WD-40 — it only cleaned the lens — and spent an hour and 15 minutes trying to open three safes, apparently unaware that some types require the dial to be turned two or three times.
They finally did a Google search for “how to open a safe” and “how to crack a safe” on a computer in the next room.
“They’re not professional safe people,” said Colorado Springs police detective Chuck Ackerman. “No, they’re not.”
On the other hand, the Google query apparently worked: The burglars haven’t been caught, and they did get about $12,000.
More
here.
(
Props, Google Watch.)
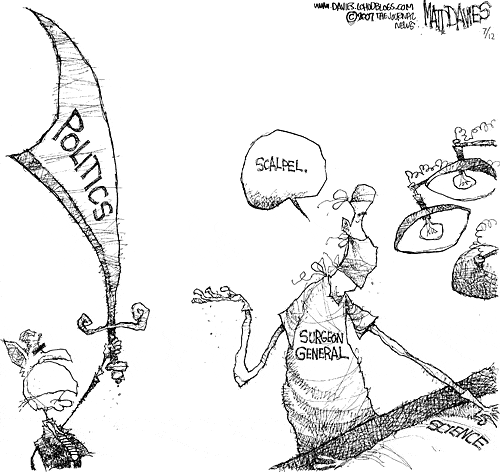
Former U.S. Surgeon General Says He Was Muzzled by Bush Administration
A Reuters newswire article, via MSNBC, reports that:
The first U.S. surgeon general appointed by President Bush accused the administration on Tuesday of political interference and muzzling him on key issues like embryonic stem cell research.
"Anything that doesn't fit into the political appointees' ideological, theological or political agenda is ignored, marginalized or simply buried," Dr. Richard Carmona, who served as the nation's top doctor from 2002 until 2006, told a House of Representatives committee.
"The problem with this approach is that in public health, as in a democracy, there is nothing worse than ignoring science, or marginalizing the voice of science for reasons driven by changing political winds. The job of surgeon general is to be the doctor of the nation, not the doctor of a political party," Carmona added.
More
here.
Greek Wiretapping Scandal: The Athens Affair
Vassilis Prevelakis and Diomidis Spinellis write in IEEE Spectrum:
On 9 March 2005, a 38-year-old Greek electrical engineer named Costas Tsalikidis was found hanged in his Athens loft apartment, an apparent suicide. It would prove to be merely the first public news of a scandal that would roil Greece for months.
The next day, the prime minister of Greece was told that his cellphone was being bugged, as were those of the mayor of Athens and at least 100 other high-ranking dignitaries, including an employee of the U.S. embassy.
The victims were customers of Athens-based Vodafone-Panafon, generally known as Vodafone Greece, the country's largest cellular service provider; Tsalikidis was in charge of network planning at the company. A connection seemed obvious. Given the list of people and their positions at the time of the tapping, we can only imagine the sensitive political and diplomatic discussions, high-stakes business deals, or even marital indiscretions that may have been routinely overheard and, quite possibly, recorded.
More
here.
TJX, Polo Data Surfaces in Credit Card Bust
A Ziff Davis Internet article by Evan Schuman, via eWeek, reports that:
After more than $75 million in bogus credit card charges, several Cuban nationals in Florida have been arrested with more than 200,000 credit card account numbers, many of which came from the TJX and Polo Ralph Lauren data breaches, according to U.S. Secret Service officials, commenting on the July 9 announced arrests.
The numbers were sent to the Florida defendants, who specialize in manufacturing bogus credit cards complete with embossing, logos, holograms and properly encoded magnetic strips, from a group of Eastern European residents who specialize in collecting the stolen credit card numbers, the Secret Service said.
That Eastern European group of fiduciary Fagans obtained those numbers from many different sources, but many of the numbers were traced back to two specific major retail data breaches: the 2006 TJX breach and a 2005 Polo Ralph Lauren breach, said a Secret Service case agent involved in the investigation and who asked that his name not be used.
Credit card numbers from the TJX theft have reportedly found themselves in multiple bogus credit card and giftcard probes, including a major gift fraud probe— which was also in Florida— as well as investigations in Alabama, North Carolina and Virginia.
More
here.
Botnets, Spam Used in Stock Scheme
Grant Gross writes in InfoWorld:
The U.S. Securities and Exchange Commission has filed securities fraud charges against two Texas men who allegedly hijacked computers nationwide to send millions of spam e-mails and cheat investors out of more than $4.6 million.
The men used networks of compromised computers, often called botnets, to send out spam about at least 13 penny stock companies, the SEC said Monday. The SEC began to investigate the operation after one of its enforcement attorneys received one of the e-mail messages at work.
Darrel Uselton and his uncle, Jack Uselton, both repeat securities law violators, illegally profited during a 20-month scalping scam, the SEC said. The two obtained shares from 13 or more penny stock companies and sold those shares after pumping up the market through manipulative trading, spam e-mail campaigns, direct mailers and Internet-based promotions, the SEC said.
More
here.
FBI Would Skirt the Law With Proposed Phone Record Program, Experts Say
Justin Rood reports on ABC News' "The Blotter":
A proposed new FBI program would skirt federal laws by paying private companies to hold millions of phone and Internet records which the bureau is barred from keeping itself, experts say.
The $5 million project would apparently pay private firms to store at least two years' worth of telephone and Internet activity by millions of Americans, few of whom would ever be considered a suspect in any terrorism, intelligence or criminal matter.
The project would involve "the development of data storage and retrieval systems...for at least two years' worth of network calling records," according to an unclassified budget document posted to the FBI's Web site. The FBI did not respond to requests for comment for this story.
The FBI is barred by law from collecting and storing such data if it has no connection to a specific investigation or intelligence matter.
More
here.
UK Home Office: Encryption Laws to Come Into Force Soon
Fiona Raisbeck writes on SC Magazine Online:
The section of the Regulation of Investigatory Powers Act (RIPA) that deals with the release of software encryption keys could come into force soon, according to the Home Secretary, Jacqui Smith.
Part III of RIPA 2000 is aimed at fighting terrorism and organised crime by giving the police new powers to decrypt files for use as evidence and force the release of encryption keys. Although the power was included in the legislation five years ago, it has not come into effect yet.
Speaking in a parliamentary debate in the House of Commons yesterday, Smith said that the Government was in the process of reviewing the law and would make a decision shortly.
More
here.
Feds Use Key Logger to Thwart PGP, Hushmail
Declan McCullagh writes on the C|Net News Blog:
A recent court case provides a rare glimpse into how some federal agents deal with encryption: by breaking into a suspect's home or office, implanting keystroke-logging software, and spying on what happens from afar.
An agent with the Drug Enforcement Administration persuaded a federal judge to authorize him to sneak into an Escondido, Calif., office believed to be a front for manufacturing the drug MDMA, or Ecstasy. The DEA received permission to copy the hard drives' contents and inject a keystroke logger into the computers.
That was necessary, according to DEA Agent Greg Coffey, because the suspects were using PGP and the encrypted Web e-mail service Hushmail.com. Coffey asserted that the DEA needed "real-time and meaningful access" to "monitor the keystrokes" for PGP and Hushmail passphrases.
The aggressive surveillance techniques employed by the DEA were part of a case that resulted in a ruling on Friday by the 9th Circuit Court of Appeals, which primarily dealt with Internet surveillance through a wiretap conducted on a PacBell (now AT&T) business DSL line used by the defendants.
More
here.
Sun's Handling of Java Security Update Prompts Concerns
Dan Goodin writes on The Register:
Sun Microsystems in the next few days plans to issue an update that plugs a serious security hole in the most recent version of its Java Runtime Environment, more than a week after providing a fix for the same vulnerability in an earlier version of the program. The lag has prompted a prominent security researcher to lambaste the effectiveness of the company's security team.
"Sun is one of the few companies that is still unable to coordinate the simultaneous release of security patches," Marc Maiffret, chief hacking officer at eEye Digital Security, wrote in an advisory warning of the flaw. "This organizational failure puts customers at undue risk. Hopefully in the future Sun will be able to bring their security and development process out of the dark ages."
More
here.
Report: Gonzales Knew of FBI Violations
John Solomon writes in The Washington Post:
As he sought to renew the USA Patriot Act two years ago, Attorney General Alberto R. Gonzales assured lawmakers that the FBI had not abused its potent new terrorism-fighting powers. "There has not been one verified case of civil liberties abuse," Gonzales told senators on April 27, 2005.
Six days earlier, the FBI sent Gonzales a copy of a report that said its agents had obtained personal information that they were not entitled to have. It was one of at least half a dozen reports of legal or procedural violations that Gonzales received in the three months before he made his statement to the Senate intelligence committee, according to internal FBI documents released under the Freedom of Information Act.
More
here.
Gapingvoid: Ideal Working Conditions
Via gapingvoid.com. Enjoy!