Scottish Elections Scuppered by e-Counting Meltdown
Kelly Fiveash writes on The Register:
The Scottish elections have been marred by an electronic counting fiasco.
The Electoral Commission has already stepped in and said that it will immediately launch an independent review into how thousands of vote counts for the Scottish Parliament and local elections had been delayed due to "technical difficulties".
According to reports, seven constituencies had to abandon the e-counting machines last night after Scotland went to the polls yesterday [Thursday, 3 May 2007].
More
here.
Firms Hit Rivals With Web Attacks
Mark Ward writes for The BBC:
Legitimate businesses are turning to cyber criminals to help them cripple rival websites, say security experts.
The rise in industrial sabotage comes as some suggest cyber criminals are turning away from using web-based attack tools in extortion rackets.
Experts suspect this is because of the risks involved in mounting such an attack on a web shop or retailer.
Instead the tools, usually hijacked home computers, are being used to pump out junk e-mail.
More
here.
Nokia Siemens Networks Details Plans to Cut 9,000 Jobs
Phil Carson writes on RCR Wireless News:
The good news: The new Nokia Siemens Networks is intent on creating a “winning company” despite difficult market conditions.
But 9,000 workers have to go.
In a carefully worded press release, Nokia Siemens referred back to a statement made a year ago when the two parties announced a merging of their network businesses that a 10%-to-15% reduction in “headcount”—that is, people—would be necessary over four years, out of the merged entity’s base of 60,000 employees.
More
here.
TSA Loses Hard Drive With Personal Info
An AP newswire article by Matt Apuzzo, via The Houston Chronicle, reports that:
The Transportation Security Administration has lost a computer hard drive containing Social Security numbers, bank data and payroll information for about 100,000 employees.
Authorities realized Thursday the hard drive was missing from a controlled area at TSA headquarters. TSA Administrator Kip Hawley sent a letter to employees Friday apologizing for the lost data and promising to pay for one year of credit monitoring services.
"TSA has no evidence that an unauthorized individual is using your personal information, but we bring this incident to your attention so that you can be alert to signs of any possible misuse of your identity," Hawley wrote in the letter, which was obtained by The Associated Press. "We profoundly apologize for any inconvenience and concern that this incident has caused you."
The agency said it did not know whether the device is still within headquarters or was stolen.
More
here.
(
Props, Flying Hamster.)
Vista Draining Laptop Batteries, Patience
Tom Krazit writes on C|Net News:
Some of Microsoft's most important customers aren't happy with the battery life offered by notebooks running Windows Vista.
"It's a little scary," said John Wozniak, a distinguished technologist in Hewlett-Packard's notebook engineering department, referring to the work HP needed to do on making Windows Vista more suitable for notebooks.
Vista, while touted as having improved power management capabilities that would make it easier for users to extend battery life, isn't to some living up to that promise. The main culprit appears to be the Aero Glass interface, a spiffy new user interface that makes Vista more pleasing to the eye with transparent windows and animated transitions when moving from one application to another.
More
here.
Canada May Stop Using U.S. Passenger Profiling Lists
Declan McCullagh writes on the C|Net News Blog:
Canada currently is relying on a secret and sometimes problematic U.S. government database to identify people who are supposed to be barred from flying or subjected to greater screening.
For now, that is. But a Canadian government representative signaled this week at the 2007 Computers, Freedom and Privacy conference that this may change.
Stephen McCammon from the Ontario Information and Privacy Commissoner's Office said that Canada may develop and maintain its own lists that would not be as problematic. Constitutional law professors, dead people, and the president of Bolivia have reportedly appeared on the U.S. lists. The political flap over a Canadian computer engineer sent to Syria and tortured can't have helped either.
More
here.
TJX: How Credit-Card Data Went Out Wireless Door
Joseph Peretra writes in The Wall Street Journal:
The biggest known theft of credit-card numbers in history began two summers ago outside a Marshalls discount clothing store near St. Paul, Minn.
There, investigators now believe, hackers pointed a telescope-shaped antenna toward the store and used a laptop computer to decode data streaming through the air between hand-held price-checking devices, cash registers and the store's computers. That helped them hack into the central database of Marshalls' parent, TJX Cos. in Framingham, Mass., to repeatedly purloin information about customers.
The $17.4-billion retailer's wireless network had less security than many people have on their home networks, and for 18 months the company -- which also owns T.J. Maxx, Home Goods and A.J. Wright -- had no idea what was going on. The hackers, who have not been found, downloaded at least 45.7 million credit- and debit-card numbers from about a year's worth of records, the company says. A person familiar with the firm's internal investigation says they may have grabbed as many as 200 million card numbers all told from four years' records.
More
here.
Microsoft Reportedly Looking at Yahoo! Again
An AP newswire article, via MSNBC, reports that:
Microsoft Corp. is resuming its pursuit of search engine operator Yahoo Inc., a deal that could help it better compete with Web search leader Google Inc., published reports said Friday.
The New York Post reported that Microsoft has asked Yahoo to enter formal negotiations for an acquisition that could be worth $50 billion. Yahoo’s market capitalization was about $38 billion on Thursday.
More
here.
Programming Note
Well, looks like it's going to be one of those days.
The hard disk on my laptop has decided to crash, and until I can get it reformatted, a new OS installed, and the most recent back-up re-installed, I'll be posting from an older (pre- Civil War), slower desktop -- posting will be kind of sporadic for a few days, methinks.
Grumble, grumble....
- ferg
The Kent State Tragedy: 37 Years Later

We mourn the senseless tragedy at Kent State, 4 May 1970.Never Forget.
Toon of the Day: The Truce
Click for larger image.
We
love Mr. Fish.
Cellphones Studied as possible Attack Detectors
Mimi Hall writes in USA Today:
The government is researching whether the best defense against a chemical, biological or radiological attack might one day be right in everyone's hands — or on their ears.
Homeland Security officials are looking into outfitting cellphones with detectors that would alert emergency responders to radiological isotopes, toxic chemicals and biological agents such as anthrax.
"If it's successful, it'll change the way chemical, biological and radiation detection is done," says Rolf Dietrich, deputy director of the Homeland Security Advanced Research Projects Agency, which invests in high-tech solutions to secure the nation against terrorist attacks. "It's a really, really neat thing."
Dietrich says it's way too early to know whether the idea would work, and department officials are just beginning talks with phone companies and privacy advocates. If it does work, he says, it could be a "game-changer" in how the nation recognizes and responds to a deadly attack.
More
here.
Welcome to the Internet .ASIA
Via The ICANN Blog.
The first gTLD located in Asia has been added to the root zone. .ASIA was added to the root overnight, becoming the 16 gTLD under contract with ICANN to be delegated.
On 6 December 2006, ICANN and DotAsia signed the .ASIA registry agreement during the ICANN Annual Meeting in Sao Paulo, Brazil.
DotAsia intends to launch the new TLD later this year.
More
here.
Warrantless Surveillance: Immunity Sought Sought for Phone Companies - UPDATE
Ellen Nakashima writes in The Washington Post:
The Bush administration is urging Congress to pass an immunity law that would halt dozens of lawsuits charging phone companies and the government with invading ordinary citizens' privacy through a post-9/11 warrantless surveillance program.
The measure is part of a legislative package drafted by the Justice Department to relax restrictions in the 1978 Foreign Intelligence Surveillance Act (FISA) that govern the administration's ability to intercept electronic communications in the United States. If passed, the proposed changes would forestall efforts to compel disclosure of the program's details through Congress or the court system.
More
here.
Stop Illegal Spying -- before they make it law.
UPDATE: 21:06 PDT: Ryan Singel has some choice commentary over on
Threat Level here.
U.S. Toll in Iraq
Via Te Boston Globe (AP).
As of Thursday, May 3, 2007, at least 3,356 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,734 died as a result of hostile action, according to the military's numbers.
The AP count is two higher than the Defense Department's tally, last updated Thursday at 10 a.m. EDT.
More
here.
Study Concludes That Many Top News Sites Don't Do RSS Well
Via Editor & Publisher.
A new study from the International Center for Media and Public Agenda, looking at 19 top news sites, released today concludes that RSS feeds work very poorly for anyone who uses news for more than infotainment.
Cited as among the best users of RSS: The Los Angeles Times, ABC News, Christian Science Monitor, BBC World Service and Fox News.
Among the worst: Al Jazeera, The Guardian and The New York Times.
More
here.
Federal Data Breach Bills Clear Senate Panel
Brian Krebs writes on Security Fix:
A key Senate committee today approved two bills that would force businesses to notify consumers if their personal or financial data is lost or stolen.
The Personal Data Privacy and Security Act of 2007, sponsored chiefly by Senate Judiciary Committee Chairman Patrick Leahy (D-Vt.) and the panel's ranking member, Arlen Specter (R-Pa.), would require entities that experience a data breach or loss that jeopardizes sensitive personal data on consumers to notify law enforcement, consumers and credit reporting agencies.
More
here.
Florida to Dump Touch-Screen e-Voting Systems
Marc L. Songini writes on ComputerWorld:
In a major shift on e-voting that could ripple to other states, the Florida Legislature today voted to replace nearly all of the state's touch-screen voting systems with optical scan devices.
Florida Gov. Charlie Crist, who initially offered up the bill mandating a change in e-voting systems earlier this year, applauded the Florida Legislature for acting after the state House approved the measure. It had already been OK'd by the state Senate.
The law mandates the replacement of touch-screen systems with optical scan devices and also moves up the date of Florida's presidential primary to the last Tuesday in January. In 2008, that would be Jan. 29.
More
here.
U.S. Senators Voice Alarm Over Terrorist Net Presence
Anne Broache writes on C|Net News:
Politicians on Thursday said the U.S. government must do more to counteract propagandizing by al Qaida and radical terrorist groups on the Internet.
Leaders of the Senate Committee on Homeland Security and Governmental Affairs said they're troubled that extremists are increasingly flocking to the Web to recruit, organize, conduct online courses, raise funds and plan attacks in a manner that's cheaper and speedier than ever before.
"We cannot cede cyberspace to the Islamist terrorists because if we do, they will successfully carry out attacks against us in our normal environment," Committee Chairman Sen. Joseph Lieberman (I-Conn.) said at a morning hearing here titled "The Internet: A Portal to Violent Islamist Extremism."
Sen. Susan Collins (R-Maine), the committee's co-chairman, spoke of the need to "resist the perversion of the World Wide Web into a weapon of worldwide war."
More
here.
USDA: 'It Will Take Years to Clean SSNs From Systems'
Mary Mosquera writes on FCW.com:
The Agriculture Department may take several years to scrub all unnecessary Social Security numbers from systems or replace systems containing the personal identifiers to better protect the sensitive information of farmers and ranchers who do business with the agency, Charles Christopherson Jr., USDA's chief financial officer, told lawmakers.
USDA last month discovered through the complaint of a loan recipient that it had inadvertently made public the Social Security and/or employer identification numbers of 38,700 grant and loan recipients. The data was publicly available through the Federal Assistance Awards Data System, which the Census Bureau manages.
Nonprofit, university and state Web sites, such as fedspending.org, reposted the information, he said.
More
here.
FCC Chairman Martin to Telcos: No Blocking Iowa Calls
Paul Kapustka writes on GigaOm:
FCC Chairman Kevin Martin said Thursday that the commission told large telcos to stop blocking calls into numbers for the Iowa-based free calling operations, threatening punitive actions if the carriers didn’t comply.
While the immediate FCC pressure was a victory for the Iowa telcos and Internet calling concerns whose services had been blocked by AT&T and Qwest, left unsolved is the separate question of whether or not the large carriers have to pay up the millions in disputed connection fees into the Iowa-based operations. But Martin, after a scheduled public appearance in Silicon Valley, made it clear that the commission took immediate action against the moves to block or restrict calls, saying they were in violation of FCC rules.
More
here.
Hackers Hijack Satellite TV in Southern China
An AP newswire article, via MSNBC, reports that:
Hackers allegedly hijacked satellite TV signals in southern China to broadcast anti-government messages, news reports said Thursday.
Viewers complained that their TV screens went blank for nearly two hours or showed anti-government messages for 30 to 40 seconds Tuesday evening, the Shanghai-based Xinmin Evening News said in a report on the Web site Sohu.com.
The report didn't describe the content of the messages that aired in Guangdong province.
More
here.
Patch Tuesday Alert: Microsoft to Patch 7 Vulnerabilities - UPDATE
Via The Microsoft Security Response Center (MSRC) Blog.
Patches on tap for May 8, 2007:
- Two Microsoft Security Bulletins affecting Microsoft Windows. The highest Maximum Severity rating for these is Critical. These updates will require a restart. These updates will be detectable using the Microsoft Baseline Security Analyzer.
- Three Microsoft Security Bulletins affecting Microsoft Office. The highest Maximum Severity rating for these is Critical. These updates may require a restart. These updates will be detectable using the Microsoft Baseline Security Analyzer.
- One Microsoft Security Bulletin affecting Microsoft Exchange. The highest Maximum Severity rating for these is Critical. These updates will not require a restart. These updates will be detectable using the Microsoft Baseline Security Analyzer.
- One Microsoft Security Bulletin affecting Microsoft CAPICOM and BizTalk. The highest Maximum Severity rating for these is Critical. These updates will not require a restart. These updates will be detectable using the Microsoft Baseline Security Analyzer and the Enterprise Scan Tool
...and
does not include a patch for
Microsoft Security Advisory 935964 (Vulnerability in RPC on Windows DNS Server Could Allow Remote Code Execution).
More
here.
Court Denies Vonage Bid for Patent Case Retrial
Peter Kaplan writes for Reuters:
A U.S. appeals court has denied a request by Internet phone company Vonage Holdings Corp. that it order a retrial in the patent infringement case brought against it by Verizon Communications Inc..
The U.S. Court of Appeals for the Federal Circuit, in a ruling dated Wednesday, turned down a motion by Vonage to have an infringement verdict by a lower court vacated because of a landmark patent ruling by the U.S. Supreme Court on Monday.
The appeals court said Vonage can cite the new Supreme Court ruling as part of its pending appeal of the case.
More
here.
Scammers Randomly Target Checking Accounts
Holy crap.
Brian Krebs writes on Security Fix:
An alarming report published this week on the official Internet news service of the U.S. Air Force highlights the need for consumers to keep a close eye on their bank account statements for signs of fraud.
The piece tells the story of an investigation launched after an Colorado airman discovered that his bank account was $124.90 less than it should have been. The man's bank, a Peterson AFB branch of 5-Star Bank, found that scammers apparently generated random account numbers, into which they tried to deposit one cent. When one of the tiny deposits clears, the criminals know they've hit upon a live account and begin to withdraw funds from it.
Turns out the crooks had automated the process: A 5-Star manager said she'd handled approximately 100 phone calls from scam victims since at least 2006, and in every case the amount withdrawn was the same and occurred at the beginning of the month, no doubt to stay well ahead of the issuance of end-of-the-month bank statements.
More
here.
Library Coalition Comes Down Hard on National Security Letters
Ryan Paul writes on ARS Technica:
A coalition of library organizations which includes the American Library Association (ALA) sponsored a gathering this week in Washington DC to promote awareness and advocacy on a broad assortment of political issues that impact libraries. The ALA's priorities for the National Library Legislative Day (NLLD) include advocating net neutrality, promoting copyright reform, and voicing concerns about the Real ID Act and the Patriot Act.
The ALA also called for "ongoing investigations" into FBI use (and abuse) of National Security Letters (NSLs) and asked legislators to "incorporate judicial review and remove gag orders from NSLs." NSLs, a special kind of subpoena that can be issued without probable cause or judicial oversight, prohibit recipients from disclosing information about NSLs to the extent that recipients can't even publicly admit receiving one. Although the basic concept of NSLs has existed in American law since the late 70s, the Patriot Act expanded the potential for abuse by making it possible for federal law enforcement agents to use NSLs to investigate citizens who are not suspects in any criminal investigations.
More
here.
FISA Immunity for Telecom Firms Slammed
Via UPI.
The ACLU Tuesday warned that a new bill would give U.S. telecom companies immunity for participating in illegal surveillance.
The American Civil Liberties Union was commenting on proposals to amend the Foreign Intelligence Surveillance Act that have been submitted to the U.S. Congress by the Department of Justice and U.S. intelligence community officials. The amendments look like they will pass Congress, but they have infuriated U.S. civil-rights groups.
More
here.
UK: Stolen Government Laptop Contains Staff Payroll Data of 10,000
Tash Shifrin writes on ComputerWorld:
A laptop computer holding personal and financial information on 10,000 U.K. National Health Service staffers has been stolen from a hospital in Cornwall.
The machine containing payroll data -- including names, addresses and bank details -- was stolen from the Royal Cornwall Hospitals Trust, which hosts the payroll for NHS staff across the county. It was stolen from locked and alarmed premises in Truro, which were forcibly entered during the night on April 30 or in the early hours of May 1.
A trust spokeswoman said the laptop was password-protected, but she was unable to say whether any other security measures were in place. Security experts warned that relying on password protection and locking laptops away was "not enough" to protect sensitive data.
The spokeswoman said the data was usually held on a server but had been downloaded to the laptop for "a specific piece of work." She added, "From time to time, information is downloaded to enable specific pieces of analysis to be done."
No patient information was stored on the computer, she said.
More
here.
Picture of the Day: Your Fortune

Props, Boing Boing.
Perspective: National ID Card a Disaster in the Making
Richard Forno and Bruce Schneier write on C|Net News:
It's time to rethink some of the security decisions made during the emotional aftermath of 9/11 and determine whether they're still a good idea for homeland security and America.
After all, if Real ID was such a well-conceived plan, Maine and 22 other states wouldn't be challenging it in their legislatures or rejecting the Real ID concept for any number of reasons.
More
here.
Netcraft: May 2007 Web Server Survey
Via Netcraft.
In the May 2007 survey we received responses from 118,023,363 sites, an increase of nearly 4.4 million sites from last month. The Internet has added 12.8 million web sites thus far in 2007, roughly on pace with growth in 2006, when the Web gained a record 30.9 million sites.
With this month's survey, Netcraft has begun tracking Google's custom web server software known as GFE (Google Front End), which is currently found on 2.7 million hostnames, or 2.3% of all sites. Google customizes its web infrastructure, with in-house solutions for software and hardware, including energy-efficient servers and power supplies. GFE is the server found on Blogger sites at blogspot.com, while Google uses GWS (Google Web Server) on some other services, although none with the volume of hostnames seen at Blogger.
More
here.
In Passing: Wally Schirra

May 3: Support World Press Freedom Day

Gapingvoid: Just the Flash, Ma'am
Via gapingvoid.com. Enjoy!

PC World Editor Resigns Over Apparent Pressure Over Ads
Tom Krazit writes on C|Net News:
Award-winning Editor-in-Chief Harry McCracken of PC World resigned Tuesday over disagreements with the magazine's publisher regarding stories critical of advertisers, according to sources.
McCracken, reached Wednesday evening, confirmed that he resigned after 12 years at the magazine and 16 years at publisher International Data Group, over disagreements with management. He declined to comment on the nature of those disagreements.
But three sources, who spoke on the condition of anonymity, told CNET News.com that McCracken informed staffers in an afternoon meeting Wednesday that he decided to resign because Colin Crawford, senior vice president, online, at IDG Communications, was pressuring him to avoid stories that were critical of major advertisers.
More
here.
Bush Administration Pulls Back on Surveillance Agreement
James Risen writes in The New York Times:
Senior Bush administration officials told Congress on Tuesday that they could not pledge that the administration would continue to seek warrants from a secret court for a domestic wiretapping program, as it agreed to do in January.
Rather, they argued that the president had the constitutional authority to decide for himself whether to conduct surveillance without warrants.
More
here.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Wednesday, May 2, 2007, at least 3,354 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,733 died as a result of hostile action, according to the military's numbers.
The AP count is one higher than the Defense Department's tally, last updated Wednesday at 10 a.m. EDT.
More
here.
Google Gives $200K to Plug-In Hybrid Car Group
Matt Marshall writes on VentureBeat:
Google’s for-profit foundation Google.org has given a $200,000 grant to CalCars.org, a group that advocates the adoption of plug-in hybrid electric cars.
Plug-in hybrids are cars you can plug into an electricity outlet to recharge their batteries, and national automakers have been slow to develop them. PG&E and GM plan to enter the market over the next couple of years.
More
here.
Cable TV, Phone Calls Taxed at Twice the Rate of Other Goods
Sonia Arrison writes on Technology Liberation Front:
Those who care about free speech should consider why government taxes are higher on communications than on other goods and services. This new study by The Heartland Institute and the Beacon Hill Institute is eye opening.
Here’s a paragraph from the study [.pdf]:
"According to the Tax Foundation, the national average retail sales tax rate (combining local, county, and state sales taxes, weighted by personal income) is 6.61 percent. Taxes and fees on cable TV and telephone subscribers average 13.52 percent, twice as high. In other words, telephone calls and cable services are taxed at two times the rate as clothing, sporting goods, and other household products."
More
here.
Estimates Put T.J. Maxx Security Fiasco At $4.5 Billion
Sharon Gaudin writes on InformationWeek:
The security breach at TJX Companies Inc. could cost the company $100 per lost record, or a total of $4.5 billion, according to the calculations of a database security company.
IPLocks, a compliance and database security company, is basing the estimate on the accumulated costs of fines, legal fees, notification expenses and brand impairment, according to Adrian Lane, the company's chief technology officer. He added that $100 per lost record is an average figure for major data breaches, but they calculated expenses particular to TJX and came out with the same figure.
The Ponemon Institute, a think tank focused on record privacy and data protection, expects the TJX breach costs to be even higher. They cite costs in the range of $182.00 per record, based on research from November 2006 of the cost of breaches incurred in 31 separate incidents. For TJX, this translates to $8.6 billion.
More
here.
Google Home Page Bug Strikes Again
Juan Carlos Perez writes on ComputerWorld:
Google Inc. renamed and upgraded its Personalized Home Page this week, but the update couldn't shake a bug that began upsetting many users last Thursday and persisted until Wednesday.
The bug caused the free service, which lets users turn Google.com into a customized portal, to revert an undetermined number of pages to their default settings or to months-old versions.
The problem rattled users who spend significant time and effort tailoring their Google.com page with syndicated content feeds, as well as with "gadget" applications, to make it their hub for Web content, online services and applications.
More
here.
Cisco Security Advisory: LDAP and VPN Vulnerabilities in PIX and ASA Appliances
Via Cisco Systems.
Multiple vulnerabilities exist in the Cisco Adaptive Security Appliance (ASA) and PIX security appliances. These vulnerabilities include two Lightweight Directory Access Protocol (LDAP) authentication bypass vulnerabilities and two denial of service (DoS) vulnerabilities.
The Lightweight Directory Access Protocol (LDAP) authentication bypass vulnerabilities are caused by a specific processing path followed when the device is setup to use a Lightweight Directory Access Protocol (LDAP) authentication server. These vulnerabilities may allow unauthenticated users to access either the internal network or the device itself.
The two DoS vulnerabilities may be triggered when devices are terminating Virtual Private Networks (VPN). These denial of service vulnerabilities may allow an attacker to disconnect VPN users, prevent new connections, or prevent the device from transmitting traffic.
More
here.
DARPA Taps Silvus to Advance MANET
John Moore writes on GCN.com:
The Defense Advanced Research Projects Agency has tapped a spinoff of the University of California at Los Angeles to advance mobile ad hoc network technology (MANET).
DARPA awarded Los Angeles-based Silvus Communication Systems a $5.96 million contract in April to build and demonstrate multiple input/multiple output (MIMO) wireless communications technology for MANETs. MIMO uses multiple antennas in radio links. Multiple data streams are transmitted in parallel from different antennas, so each pair of antennas added to a communications system results in a linear increase in throughput, according to the company.
Consequently, MIMO increases throughput without increasing bandwidth, said Babak Daneshrad, Silvus Communication’s founder and chairman.
More
here.
Homeless Man Disrupts Internet2 Service
Adam Gaffin writes on NetworkWorld:
A fire started by a homeless man knocked out service between Boston and New York on the experimental Internet2 network Tuesday night.
Chris Robb, an engineer at Indiana University's Global Network Operations Center who works on Internet2, says Level 3 Communications cables used by the network went up in flames. The cables were on the Longfellow Bridge, which connects Boston and Cambridge across the Charles River.
Robb, who co-authors the Internet2 Network Upgrade blog, writes that Level 3 engineers estimate it could take one to two days to restore the circuit. Engineers are looking at rerouting a Chicago-to-New York OC-192 circuit that normally goes through Boston to Washington until service is restored.
Robb writes: "Question: When can a cigarette take down your network? Answer: When you throw it at a bridge and light it on fire."
More
here.
Data Breaches Seen to Threaten IT Job Security
Denise Dubie writes on NetworkWorld:
Most IT professionals feel their jobs would be on the line in the event of a security breach and at the same time feel ill-equipped to prevent such corporate or personal data loss, according to a survey released this week.
Nearly three-quarters of more than 250 IT professionals polled said they are concerned they would lose their jobs in the aftermath of a major security breach at their company. About two-thirds of the IT professionals working at Fortune 100,000 or midsize companies also said the responsibility associated with such breaches affects them personally.
And while 87% of IT organizations surveyed said they are confident in their ability to deal with viruses, spam, spyware and malware, just 35% felt they could deal with corporate or personal data loss.
More
here.
Is Any MPLS Alternative DOA?
Jim Duffy writes on NetworkWorld:
Granted, it was an MPLS-immersed conference. And Cisco had its best engineering SWAT team there to exterminate anything that threatened its router franchise.
But this week’s Future-Net conference -- formerly MPLScon -- showed just what a daunting uphill climb MPLS alternatives such as Provider Backbone Transport (PBT) have to gain market momentum.
More
here.
Quote of the Day: Ed Felten
"It turns out that the 'government' of Digg’s community gets its power from the consent of the governed. Users of other Web 2.0 sites will surely take note."
- Ed Felten, writing on Freedom to Tinker.
POS Vendors Now Targeted In Credit Card Receipt Error Case
Evan Schuman writes on eWeek:
Following lawsuits in February against some of the nation's largest retailers for allegedly revealing too much credit card information on printed receipts, two of those retailers are now suing their point-of-sale vendors.
In the initial lawsuits filed early this year, some 50 of the nation's top retailers—including Rite Aid, Harry & David, Ikea, KB Toys, Disney, Regal Cinemas and AMC Theaters—were accused of printing full credit numbers and expiration dates on printed customer receipts, violating a provision of the Fair and Accurate Credit Transactions Act, or FACTA, that makes it illegal for a retailer to print more than the last five digits or a credit/debit card number, and it also forbids printing the card's expiration data on that receipt. The rule took effect in phases, but by December 2006, the latest of its phases kicked in.
More
here.
Level 3 Selected by Second Life
Via Web Hosting Industry Review (WHIR).
Telecommunications provider Level 3 Communications announced on Wednesday that it has been selected by Linden Lab, the creators of 3D virtual world Second Life, to provide high speed Internet access and wavelengths via two 10 gigabits per second ports, connecting Second Life's data centers in San Francisco, California and Dallas, Texas.
Second Life is a 3D online world with a growing population of users, or "Residents," that create and build the world around them, which includes homes, vehicles, nightclubs, stores, landscapes, clothing and games. The Second Life Grid is a sophisticated development platform created by Linden Lab to create a revolutionary new form of shared 3D experience, says the company.
More
here.
How a Number Became the Latest Web Celebrity
Brad Stone writes in The New York Times:
The geeks are in open revolt.
A throng of tech-savvy Internet users have banded together over the last two days to publish and widely distribute a secret code used by the movie industry to prevent illegal copying of high-definition movies.
The broader distribution of the code may not pose a serious threat to the movie industry, because only sophisticated technologists can use it to tailor the decryption software capable of getting around the copy protection on Blu-ray and HD DVD discs. But its relentless spread has already become a lesson in mob power on the Internet and the futility of censorship in the digital world.
The online uproar came in response to a series of cease-and-desist letters from lawyers for a group of movie studios and electronics companies, demanding that the code be removed from several high-profile Web sites. Rather than wiping out the code, which is essentially one long number, the letters led to its proliferation on Web sites, in chat rooms, inside cleverly doctored digital photographs and on user-submitted news sites.
More
here.
Background
here.
xkcd: Sea of Memes
Click for larger image.
We
love xkcd.
Digg Goes Bananas -or- 'Even Jesus Hates the MPAA'

Ben Popkin writes on The Consumerist:
A wide-scale user revolt is disrupting popular social news networking Digg. It's a protest over Digg acquiescing to MPAA pressure and deleting a 15,000+ dugg story about a crack for the HD-DVD/Blu-Ray DRM system.
Now, every single story on the front page contains the cracked number in some way.
The madness began after not only was the initial story deleted, but the user's account was deleted as well. Other people who submitted stories linking to the number also got their accounts deleted and their sites received takedown notices. Even people who submitted stories about the deleting of other accounts, stories which did not contain the number, also got deleted. That's when things really got bonkers.
More
here.
Image source: newshappenings.blogspot.com
Senators Wary of Bush's Wiretap Proposal
An AP newswire article by Michael J. Sniffen, via The Boston Globe, reports that:
Citing FBI abuses and the attorney general's troubles, senators peppered top Justice and intelligence officials Tuesday with skeptical questions about their proposal to revise the rules for spying on Americans.
Senate Intelligence Committee members said the Bush administration must provide more information about its earlier domestic spying before it can hope to gain additional powers for the future.
For two hours, National Intelligence Director Mike McConnell, National Security Agency Director Lt. Gen. Keith Alexander, Assistant Attorney General Kenneth Wainstein and their lawyers tried to parry increasingly dubious and hostile questions. They deferred many answers to a committee session closed to the public.
More
here.
U.S. Army Forbids Troops From Blogging
Noah Shachtman writes on Wired News:
The U.S. Army has ordered soldiers to stop posting to blogs or sending personal e-mail messages, without first clearing the content with a superior officer, Wired News has learned. The directive, issued April 19, is the sharpest restriction on troops' online activities since the start of the Iraq war. And it could mean the end of military blogs, observers say.
Military officials have been wrestling for years with how to handle troops who publish blogs. Officers have weighed the need for wartime secrecy against the opportunities for the public to personally connect with some of the most effective advocates for the operations in Afghanistan and Iraq -- the troops themselves. The secret-keepers have generally won the argument, and the once-permissive atmosphere has slowly grown more tightly regulated. Soldier-bloggers have dropped offline as a result.
The new rules obtained by Wired News require a commander be consulted before every blog update.
More
here.
Police Want Computer Technicians to Help Nab Child Abusers
An AP newswire article by Susan Haigh, via USA Today, reports that:
Computer technicians would be obligated to report child abuse just like doctors, teachers and others who work closely with children, under measures being considered by lawmakers in two states.
At least five states — Arkansas, Missouri, Oklahoma, South Carolina and South Dakota — require computer technicians to report child pornography. Connecticut and California are considering legislation that would go a step further, adding technicians to the list of "mandated reporters" who notify authorities about any type of child abuse and neglect.
More
here.
Hackers Set Traps on Broad Websites
Jon Swartz and Byron Acohido write on USA Today:
Ordinary websites are fast-becoming a top security threat for PC users.
Tainted Web pages first appeared in late 2005. Now, they're turning up as Google advertising links, on Wikipedia and elsewhere, "from top-tier names to mom and pop bakery shops," says Dan Hubbard, vice president of security research at Websense.
Cybercrooks are corrupting Web pages by the tens of thousands. By tapping holes in the Internet Explorer browser, they implant tiny programs that connect the PC of anyone who simply clicks on the tainted page to a "mother ship" server, often in Russia or China.
That central server collects data typed into online forms — banking log-ins and shopping cart transactions, for instance. It also hijacks the captured PC into a network of compromised PCs, known as "bots," to spread spam.
In one recent sweep, security firm Cyveillance identified 50,000 corrupted pages. Websense estimates the actual number may be 10 times that.
More
here.
DRM Lobby Tries to Get HD-DVD Genie Back Into Bottle

Tom Sanders writes on vnunet.com:
A DRM licensing authority is strong-arming search engines, bloggers and open source advocates in a desperate attempt to stop the spread of a software key that discables copyright protections on Blu-ray and HD-DVD disks.
Copyright reform activist Cory Doctorow on Monday decided to remove the information from a group blog to which he contributes after he received a cease and desist letter from the Advanced Access Content System Licensing Administrator (AACS-LA).
The consortium is backed by technology vendors including IBM, Intel, Microsoft, Sony and the Walt Disney Company. It oversees the AACS digital rights management technology that is used on high definition DVDs.
The so-called processing keys that the blog published lets users disable the DRM technology that prevents users from copying the disks or from playing it on unlicensed equipment or software.
More
here.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Tuesday, May 1, 2007, at least 3,351 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,731 died as a result of hostile action, according to the military's numbers.
The AP count is the same as the Defense Department's tally, last updated Tuesday at 10 a.m. EDT.
More
here.
Job Cuts Said to Backfire On Circuit City's Results
Amy Joyce writes in The Washington Post:
Circuit City fired 3,400 of its highest-paid store employees in March, saying it needed to hire cheaper workers to shore up its bottom line. Now, the Richmond electronics retailer says it expects to post a first-quarter loss next month, and analysts are blaming the job cuts.
The company, which on Monday also revised its outlook for the first half of its fiscal year ending Feb. 29, 2008, cited poor sales of large flat-panel and projection televisions. Analysts said Circuit City had cast off some of its most experienced and successful people and was losing business to competitors who have better-trained employees.
More
here.
Comcast Preps Docsis 3.0 Trials
Jeff Baumgartner writes on Cable Digital News:
Comcast Corp. is looking to begin Docsis 3.0 trials this year, with deployments possibly following in 2008, according to Tony Werner, the MSO's executive vice president and chief technology officer.
Werner discussed those plans and other elements of Comcast's technology strategy Tuesday during the MSO's analyst and investor day.
Werner did not say where Comcast would trial or deploy the new platform, but did note that those decisions would be based on certain business requirements, and pointed out that 3.0 can be targeted to specific portions the market.
More
here.
Off Beat: DHL Wins Package Race, UPS Still In Transit

Meghhan Marco writes on The Consumerist:
Every year Georgia Tech's Supply Chain and Logistics Institute holds a shipping race to see who can deliver packages to remote locations the quickest. Unbeknownst to the companies, they're competing in the Olympics of shipping.
This year DHL won delivering first to 3 of the 5 locations, and second to the remaining 2.
Doesn't the DHL guy look happy? He was the first to Tikrit, Iraq. That's a Black Hawk helicopter behind him. Sadly, UPS never even made it.
The contest write up has some pretty hilarious commentary... highlights inside.
More
here.
Image source: The Consumerist
New Russian Privacy Law Deals With WHOIS Data
Via the ICANN Blog.
There’s a new law on data protection in Russia, and under its provisions, information for web site owners should not be accessible online.
The .ru WHOIS database has almost three years to fulfill the law requirements (until January 1, 2010), but RIPN, the largest registrar in .ru, says they may be ready to implement it in the coming months.
More
here.
Picture of the Day: Mission Accomplished

Paul Bedard writes in U.S. News & World Report's "Washington Whispers":
An only-In-Washington street scene: As tourists line up for their picture-perfect scene in front of the White House, a protester adds a little reminder that it was four years ago today that President Bush stood under a banner proclaiming "Mission Accomplished" to announce the end of key military actions in Iraq.
Link.
Bonus link: In the closing monologue from last week’s "Real Time," Bill Maher took aim at the president and his followers. Via TruthDig.
Image source: U.S. News & World Report
House Committee Grills DHS on Information Security
Jaikumar Vijayan writes on ComputerWorld:
Bennie Thompson, (D-Miss.), the chairman of the House Committee on Homeland Security, joined other committee members in sending a letter to Scott Charbo, the CIO at the Department of Homeland Security (DHS) seeking answers to 13 questions pertaining to information security at the agency.
In the letter, Thompson and other members cited a subcommittee hearing held last month into hacking incidents at the Departments of State and Commerce last year and said they are concerned that similar incidents might be occurring within DHS networks. "These incidents jeopardize the integrity of our government's information," they said in the letter, which was publicly released today.
In their letter, committee members are seeking information on the number of security incidents reported by the DHS to the U.S. Computer Emergency Readiness Team (US-CERT) and the number of cyberattacks that it had suffered between 2004 and 2007. The DHS was also asked to classify the attacks based on their severity, together with a listing of all incidents not reported to the CERT.
More
here.
JetBlue Employees Accused in Credit Card Scam
Via Newsday.com.
Four JetBlue employees and a city corrections officer have been charged with stealing credit card numbers from several unsuspecting airline passengers.
Prosecutors said the five used the cards to go on a spending spree at restaurants, liquor stores, and shops including Bloomingdale's and Victoria's Secret.
Investigators began looking at the group after one traveler rushing to catch a flight accidentally left his credit card behind at a JetBlue counter at John F. Kennedy International Airport. Later, someone used the card to run up $508 in charges, the Manhattan district attorney's office said.
Three of the suspects are JetBlue customer service customer service agents. One was a flight attendant.
All five were to be arraigned in Manhattan Tuesday on identity theft charges.
JetBlue said it has suspended the four workers.
More
here.
(
Props, Consumerist.)
Websense: Malcode Found on Mexican .Gov Website
 Image source: Websense
Image source: Websense.
Websense® Security Labs™ has discovered malicious code hosted on a government body's official Web site. The victim is Comisión Federal de Telecomunicaciones, a division of Mexico's government (equivalent of the FCC in the United States).
The main page of this Mexican government Web site does not contain anything malicious. However, when a user visits http://prospectiva.cft.gob.mx/, an .scr file is downloaded. After execution, the .scr file drops a suspiciously named executable into the Windows startup directory for all users.
The executable downloaded from this government site is malicious. The newly-installed malware collects user information and sends it back to the original source of the executable.
More
here.
Note: Yet another example on the threat landscape of a method for compromising end-systems which is growing at an alarming rate.
- ferg
In Passing: Tom Poston

Image source: www.starpulse.com
Mobile Payment Systems May Enable Terrorist Financial Transactions
Rachel Ehrenfeld and John Wood write for UPI Outside View:
Advanced mobile technology, cooperation between international mobile communications providers and international financial institutions and the lack of regulations make for a swift, cheap, mostly untraceable money transfer -- known as "m-payments" -- anywhere, anytime, by anyone with a mobile telephone.
Members of the GSM Association and MasterCard are developing an m-payment service to enable 200 million international migrant workers and the poor who lack bank accounts to transfer money domestically and internationally. According to the World Bank, 175 million migrants transferred at least $230 billion in international remittances in 2005. A recent U.N.-sponsored South African study found that m-banking can be up to one-third cheaper for customers than the current banking alternatives.
However, the spread of m-payments in less developed countries, which often lack functioning anti-money laundering and anti-terrorist financing regulatory frameworks, and where corruption is rife, will likely increase money laundering and terrorist financing.
More
here.
NBA Star Bruce Bowen Claims Hard Drive Foul
Via The Smoking Gun.
An NBA star claims that a Texas company hired to repair his computer instead removed the machine's hard drive and sold the item--which contained confidential personal and financial information--to another customer.
In a Bexar County District Court lawsuit, San Antonio Spurs forward Bruce Bowen seeks more than $2 million in damages from Computer Nerdz, the San Antonio company he and his wife hired last year to repair his Gateway computer.
More
here.
JP Morgan Chase Client Data Loss
Via Financial News Online.
JP Morgan Chase has alerted thousands of its Chicago-area millionaire clients, as well as some of its own employees, that it cannot locate a computer tape containing their account information and Social Security numbers.
The tape, which was in a locked container, was being transported from a bank location to an off-site facility last month when it went astray, a JP Morgan spokesman said. It is not clear if the tape arrived at its destination or was lost along the way.
The tape contained data from JP Morgan's private-client services business, which provides financial services to clients who have a net worth of between $1m (€733,135) and $25m, the spokesman said. The tape also included data belonging to JP Morgan employees. Some 47,000 accounts were affected.
More
here.
(
Props, Attrition.org.)
Eavesdropping Tech: U.S. Wiretaps Up Slightly in 2006
Via USCourts.gov.
A total of 1,839 orders were issued by federal and state courts in 2006 authorizing or approving the interception of wire, oral or electronic communications, also known as wiretaps. This is a 4 percent increase over the 1,773 orders issued in 2005, according to The 2006 Wiretap Report.
The complete report contains information on interceptions concluded between January 1, 2006 and December 31, 2006. A summary of the authorized intercepts [.pdf] reported for calendar years 1996-2006 is availabe in Table 7.
No applications for wiretap authorizations were denied by either state or federal courts in 2006.
More
here.
(
Props, Pogo Was Right.)
Off Beat: America's War on Tourists
Peter Huck writes in The New Zealand Herald:
Welcome to America, where officials who work for the Department of Homeland Security, which was set up after the 2001 terrorist attacks, have a major image problem.
In a recent poll of international travellers, commissioned by Discover America Partnership, a coalition of US tourist organisations, 70 per cent of respondents said they feared US officials more than terrorists or criminals. Another 66 per cent worried they would be detained for some minor blunder, such as wrongly filling out an official form or being mistaken for a terrorist, while 55 per cent say officials are "rude."
More
here.
(
Props, Boing Boing.)
Corporate Spambots and... Nationwide Insurance
Support Intelligence rolls on in their effort to expose troubling spambot activity in major corporations' networks.
We have been watching the Nationwide Insurance Network for a few months now, and have been impressed with the spam/ham ratio. Its spammyness something like 100:1 in spam to ham. We have collected some 1,857 SPAM from 6 IP addresses on Nationwide's Network.
The kinds of spam we got from Nationwide varied from Pharmacy spam advocating various Erectile Dysfunctions drugs, Rolex watches, graphic pornography, mortgage loans, weight loss and stock pump-n-dump.
The main question is if any of Nationwide's consumer data was compromised.
More
here.
Debate Revived Over Private Use Of Terror Watch Lists
Kelley Beaucar Vlahos writes for Fox News:
A debate over whether federal terror lists are wrongly singling out innocent Americans has been revived in a recent report suggesting that landlords, employers and even health insurers are vetting people against a Treasury Department terror list and not always getting it right.
The Lawyers Committee for Civil Rights of the San Francisco Bay Area alleges that more Americans than ever are being mistakenly connected to the Treasury Department's Office of Foreign Assets Control (OFAC) list of persons and companies engaging in or affiliated with terrorism.
More
here.
(
Props, Flying Hamster.)
UK: Vodafone Faces Legal Action Over VoIP Blocking
Peter Judge writes on TechWorld (UK):
Mobile operator Vodafone could face legal action over its efforts to cripple VoIP on mobile phones.
"We believe Vodafone's stance is not lawful, and we are considering our position," said James Tagg chief executive of Truphone. Vodafone is failing to meet interconnection obligations, and blocking competing websites, he said, as well as disabling Internet telephony on handsets.
Vodafone is refusing to connect calls to Truphone's range of mobile numbers, Tagg says, in breach of telecoms regulation. Truphone has a range of numbers (beginning 07978 8XXXXX) with which it can function as an actual mobile operator - so that Truphone numbers appear in a phone's call log, and can receive SMS messages. Unfortunately, Vodafone customers will simply find that calls to those numbers are blocked, whether they are made over WiFi or the Vodafone network, says Tagg.
The operator is also blocking VoIP websites including Skype, to users of its mobile Internet service, says Tagg - a move which would be against EU competition regulations, he says: "European telecoms legislation, gives operators an obligation to interconnect, and to offer unfettered access to services."
More
here.
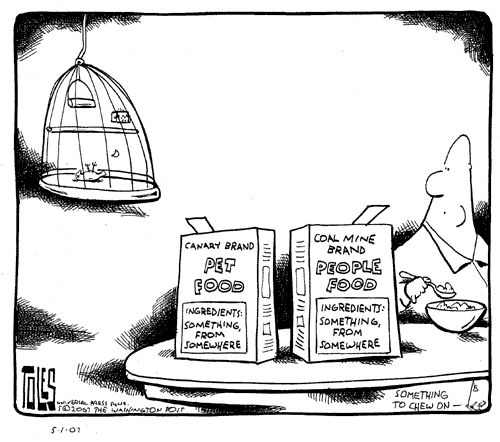
Toon of the Day: Canary in a Coal Mine
Click for larger image.
Soylent Green Alert: FDA Downplays the Ever Expanding Food Safety Issues

David Goldstein:
The U.S. Department of Agriculture (USDA) and the U.S. Food and Drug Administration (FDA) continue their investigation of Soylent Green, which has been found to contain people and people-related compounds.
Based on information currently available, FDA and USDA believe the likelihood of illness after eating Soylent Green would be very low. The agencies are taking certain actions out of an abundance of caution. As announced on April 26, Soylent Green known to have been adulterated (ie, contaminated with adults) will not be approved to enter the food supply.
As reported on April 22 by FDA, the Agency determined that plankton protein concentrate imported from China was contaminated with people and people-related compounds. As part of the ongoing investigation, FDA has determined the plankton protein was used in the production of Soylent Green.
More
here.
The really ridiculous reality
here.
Terror Risk: Crash Shows Cities Vulnerable if Tankers Used as Weapons

Anna Badkhen writes in The San Francisco Chronicle:
The day after a fiery gasoline truck accident destroyed key ramps in the MacArthur Maze interchange, security analysts and truck drivers weighed the scope of damage a deliberate terrorist attack using tankers could cause U.S. metropolises and highways.
Security experts said the crash -- and the costly repairs -- demonstrated how easy it would be for terrorists to disrupt normal life in major U.S. cities.
"It's very difficult now to purchase explosives ... but it's not that hard to steal a truck full of gasoline, and you can do quite a bit of damage," said Christopher Falkenberg, a former Secret Service agent who is now the president of Insite Security, a consulting firm in New York. "You don't need access to sophisticated explosives to have a big impact."
Mayor Gavin Newsom has called the accident a giant wake-up call, saying it highlighted how vulnerable San Francisco is to a potential terrorist attack.
More
here.
Image source: The San Francisco Chronicle
VeriSign to Offer One-Time Passwords on Bank Cards
An AP newswire article by Anick Jesdanun, via ABC News, reports that:
A leading provider of digital-security services wants to make disposable passwords easier for consumers to accept by squeezing the technology into the corner of a regular credit or ATM card.
Fran Rosch, vice president for authentication services at VeriSign Inc., said the one-time passwords haven't taken off in the United States partly because consumers need to carry a small device that generates passwords on the fly. That barrier is removed, he said, by having the technology built into cards consumers already carry.
VeriSign was expected to announce a deal Tuesday with Innovative Card Technologies Inc. to outfit banks and e-commerce sites with cards that work with VeriSign's password system.
With the card, consumers logging on to an online bank account, for instance, would type in their regular username and password, along with a six-digit code that appears on the card's display window. That code constantly changes, meaning the customer needs to have possession of the card to access the account.
More
here.