U.S. Toll in Iraq

Via The Boston Globe (AP).
As of Saturday, Dec. 1, 2007, at least 3,882 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,161 died as a result of hostile action, according to the military's numbers as of Friday.
The AP count is three higher than the Defense Department's tally, last updated Friday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Security Firm Cracks Encryption for Microsoft's Wireless Keyboards
Via heise Security News.
Dreamlab Technologies AG says it has found a way to sniff the data traffic between Microsoft's wireless keyboards and their base stations, which communicate with each other on the 27 MHz band. In the method they discovered, unauthorized parties are reportedly able to record and decrypt all keystrokes from such keyboards. The decoding was demonstrated using data traffic from the Wireless Optical Desktop 1000 and 2000. The security firm says that other keyboards that Microsoft sells, such as the Wireless Optical Desktop 3000 and 4000, encrypt and transmit data using the same procedure, so that they are also probably unsafe. Keyboards that use Bluetooth for communication are not vulnerable.
Max Moser and Philipp Schrödel say that decryption was very easy because the devices use a simple XOR mechanism for encryption and the keys are only one byte long. They claim that even a PDA with a slow ARM-CPU would have derived the combination quickly. Aside from not using such keyboards, there is no workaround. Microsoft has yet to react to the Swiss firm's announcement.
More
here.
Facebook's Beacon More Intrusive Than Previously Thought
Juan Carlos Perez writes on ComputerWorld:
A CA security researcher is sounding the alarm that Facebook's controversial Beacon online ad system goes much further than anyone has imagined in tracking people's Web activities outside the popular social networking site.
Beacon will report back to Facebook on members' activities on third-party sites that participate in Beacon -- even if the users are logged off Facebook and have declined having their activities broadcast to their Facebook friends.
That's the finding published on Friday by Stefan Berteau, senior research engineer at CA's Threat Research Group in a note summarizing tests he conducted.
More
here.
Bloggers See Red Over Target's 'Little Secret'

Jackie Crosby writes in The Minneapolis-St.Paul Star Tribune:
Target Corp. is learning the hard way that life in the blogosphere can put you right in the bullseye.
The Minneapolis-based discount retailer is being outted in online blogs and discussed in college ethics classes after students allied with the company were told to "keep it like a secret" while singing the company's praises on the social network site, Facebook.com.
More
here.
U.S. Toll in Iraq, Afghanistan

Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Friday, Nov. 30, 2007, at least 3,881 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,161 died as a result of hostile action, according to the military's numbers.
The AP count is two higher than the Defense Department's tally, last updated Friday at 10 a.m. EST.
As of Friday, Nov. 30, 2007, at least 401 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures Nov. 24, 2007, at 10 a.m. EST.
Of those, the military reports 271 were killed by hostile action.
More
here and
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
UK: MI5 Warns of Chinese Cyber Espionage

Gemma Simpson writes on Silicon.com:
MI5 has issued a warning to UK businesses that spies in China are conducting a campaign of cyber espionage against them.
Martin Jordan, principal advisor of IT advisory services at KPMG, told silicon.com, that MI5 - through its branch the Centre for the Protection of National Infrastructure - has been monitoring activity emanating from China and it has noticed an upsurge in electronic espionage attempts made or launched against a lot of UK companies.
More than 1,000 letters were subsequently sent by the director general of MI5 to the heads of UK business yesterday, according to Jordan, warning them spies are targeting financial information relating to deals which may occur and involve Chinese companies.
More
here.
U.S. Plans New Spy Satellite Program
An AP newswire article by Anne Flaherty and Pamela Hess, via SFGate.com, reports that:
The U.S. is pursuing a multibillion-dollar program to develop the next generation of spy satellites, the first major effort of its kind since the Pentagon canceled the ambitious and costly Future Imagery Architecture system two years ago, The Associated Press has learned.
The new system, known as BASIC, would be launched by 2011 and is expected to cost $2 billion to $4 billion, according to U.S. officials familiar with the program. They discussed details on condition of anonymity because the information is classified.
Photo reconnaissance satellites are used to gather visual information from space about adversarial governments and terror groups, such as construction at suspected nuclear sites or militant training camps. Satellites also can be used to survey damage from hurricanes, fires and other natural disasters.
The new start comes as many U.S. officials, lawmakers and defense experts question the high costs of satellite programs, particularly after the demise of the previous program that wasted time and money.
More
here.
Battle Over VA's Data Breach Heads to Mediation
Andrew Noyes writes on GovExec:
Lawyers for people who sued the Veterans Affairs Department over last year's data breach will begin mediation with government attorneys in the weeks ahead and will update the federal judge overseeing the case in early 2008.
Earlier this month, U.S. District Judge James Robertson dismissed several aspects of the case but said the handful of plaintiffs sufficiently made the claim that the department failed to safeguard their personal information, as required by the Privacy Act.
The action was brought to the U.S. District Court for the District of Columbia as a potential class-action representing each of the estimated 26.5 million veterans whose data could have been jeopardized in the incident. The FBI eventually recovered the stolen equipment and said the files were not accessed.
More
here.
Ruling Helps TJX Reduce Liability in Data Breach Case
Evan Schuman writes on eWeek:
In a pair of crucial decisions, TJX has moved closer to completely clearing itself of the lawsuits from the world's worst credit card data breach.
Those two rulings came from the federal judge overseeing the case—who refused to approve making the case a class action—and from Visa, which said it would reduce its fining of The TJX Companies in exchange for certain payments from the retailer to banks.
On the afternoon of Nov. 29, U.S. District Court Judge William Young denied the request to grant the bank class action certification, ruling that the many of the banks' situations were too different from each other. Some of the banks had the expense of reissuing the cards while others didn't, for example.
That decision is quite likely to stand, but there are two chances for it to change. The U.S. Court of Appeals could overrule Young, and attorneys for the banks have 10 days from Nov. 29 to file an appeal.
More
here.
e-Mail Analysis Snooping in Your In-Box
Esther Schindler writes on CIO.com:
A researcher working at the Air Force Institute of Technology (AFIT) in Ohio has found a new use for an open-source algorithm, reports New Scientist in its December 1 issue. While the software was originally used to analyze the topics people talk about, researcher Gilbert Peterson and his colleagues have found a new use: snooping through company e-mail.
Author-Topic, developed by researchers at the University of California, Irvine, is essentially a data mining tool that chews on textual information. If it's fed academic journal articles, New Scientist suggests, Author-Topic "examines the frequency with which words appear in each and uses that to infer which topic that document is about. It then identifies topics that each person writes on most.
More
here.
Mozilla Swats Firefox Bug With a Patch
Brian Prince writes on eWeek:
Officials at Mozilla said they have released an update to fix a flaw in the recently released 2.0.0.10 version of their Firefox browser.
It is the first time ever Mozilla has released two versions of the open-source browser in the same week. When Mozilla released Firefox 2.0.0.10 Monday, it included a bug in its rendering canvas HTML elements. Canvas elements allow for dynamic, scriptable rendering of bitmap images in HTML.
More
here.
White House Seeks to Slash Anti-Terror Funds
An AP newswire article, via MSNBC, reports that:
The Bush administration intends to slash counterterrorism funding for police, firefighters and rescue departments across the country by more than half next year, according to budget documents obtained by The Associated Press.
The Homeland Security Department has given $23 billion to states and local communities to fight terrorism since the Sept. 11 attacks, but the administration is not convinced that the money has been well spent and thinks the nation’s highest-risk cities have largely satisfied their security needs.
The department wanted to provide $3.2 billion to help states and cities protect against terrorist attacks in 2009, but the White House said it would ask Congress for less than half — $1.4 billion, according to a Nov. 26 document.
More
here.
Data Theft Touches 150,000 Massachusetts Seniors
Robert McMillan writes on InfoWorld:
The state of Massachusetts is warning 150,000 members of its Prescription Advantage insurance program that their personal information may have been snatched by an identity thief.
Local authorities arrested a lone identity thief in August who had been using information taken from the program in an attempted identity theft scheme, said Alison Goodwin, a spokeswoman for the state's Executive Office of Health and Human Services.
Goodwin could not add many details on the nature of the breach, citing an ongoing criminal investigation, but she said Prescription Advantage is conducting an internal review of the incident to determine if additional security measures might be required.
More
here.
USAID Server Hacked To Serve Pornography
Thomas Claburn writes on InformationWeek:
The U.S. Agency for International Development (USAID) provides economic, developmental and humanitarian assistance around the world in conjunction with the foreign policy goals of the United States. It also provides porn, or so it appeared as of 2:00 pm PST on Friday.
A call to USAID for comment found the agency unaware that one of its servers had been compromised. A few minutes later, a USAID spokesperson called back to say that the agency's IT staff was in the process of dealing with the issue. The hacked server was associated with USAID's Tanzania subdomain: Tanzania.usaid.gov.
This rather unorthodox offering was discovered by Sunbelt Software. As security researcher Patrick Jordan noted in a blog post on Friday, searching for porn using Google's "site:" operator (to restrict the search to the USAID domain) returned a list of apparent porn links.
More
here.
Top U.S. Spy Pushed Congress For Wider Powers, Citing High Summer Threat Level
 U.S. Director of National Intelligence Michael McConnell
U.S. Director of National Intelligence Michael McConnellRyan Singel
writes on
Threat Level:
The Director of National Intelligence urged powerful members of Congress to rush through legislation this summer that gave the NSA wide powers to install phone and internet wiretaps inside the United States, according to government sunshine documents released Friday.
The 242 pages of documents include letters to DNI Michael McConnell from members of Congress dated after the August 5 passage of the Protect America Act that question whether McConnell negotiated in good faith or followed political orders from the White House.
The documents are the first to be released to the Electronic Frontier Foundation after a federal court judge on Wednesday ordered their prompt release.
More
here.
Malware Targets E-Banking Security Technology
Brian Krebs writes on Security Fix:
A new class of malicious software contains a feature specifically designed to thwart online security technology implemented by Bank of America and many other financial institutions that allow their customers to monitor and make changes to their accounts via the Internet.
The feature was found in a recent version of "Pinch," a widely distributed Trojan horse program that gives bad guys the ability to steal usernames and passwords from a victim's computer. Turns out, the newly detected version of Pinch also looks for and steals a special token that gets planted on the machine of anyone who banks online with a financial institution that is using Adaptive Authentication, a Web site security technology owned by RSA Security.
More
here.
In Passing: Evel Kneivel

U.S. Toll in Iraq

Via The Boston Globe (AP).
As of Thursday, Nov. 29, 2007, at least 3,880 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,161 died as a result of hostile action, according to the military's numbers.
The AP count is three higher than the Defense Department's tally, last updated Thursday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
U.S. Special Counsel Bloch Says He Won't Provide Files
Elizabeth Williamson writes in The Washington Post:
A U.S. official overseeing a probe of potential White House misconduct declared through a spokesman yesterday that he will not give federal investigators copies of personal files that he deleted from his office computer.
The decision by Special Counsel Scott J. Bloch escalates the confrontation between the Bush appointee and the White House, each of which is investigating the other.
Bloch's office is tasked with upholding laws against whistle-blower retaliation and partisan politicking in federal agencies. Earlier this year, Bloch directed lawyers in his office to look into charges that former Bush adviser Karl Rove inappropriately deployed government employees in Republican political campaigns.
More
here.
Note: This is also the guy who allegedly used Geeks-on-Call
to erase Gov't computer evidence.
Fed Tells States to 'Name One Fusion Center'
Via UPI.
The departments of Justice and Homeland Security have asked every state to designate a single "fusion center" for terrorism and law enforcement intelligence.
"Sharing information -- whether it is from one government agency to another, or from all of us to our citizens -- is a vital part of being prepared against all threats," Attorney General Michael Mukasey told a conference of state attorneys general Thursday.
To maximize the efficiency of that effort, Mukasey said, he and Homeland Security Secretary Michael Chertoff had sent every governor a request that the state "designate a primary fusion center to coordinate the gathering, processing, analysis, and dissemination of terrorism, law enforcement and homeland security information."
More
here.
Note: On the heels of
reports that the scope of the DHS Fusion Centers has slipped to local crime enforcement, this is not a good development.
-ferg
ACLU Charges FBI Improperly Using Patriot Act Surveillance Powers
Via ACLU.org.
As a result of newly released Department of Defense (DoD) documents revealing the potential abuse of the government’s surveillance powers, the American Civil Liberties Union today filed a Freedom of Information Act (FOIA) request to force the FBI to turn over documents concerning its use of National Security Letters (NSLs) that demand private data about individuals within the United States without court approval.
In today’s request, the ACLU seeks records pertaining to the FBI’s issuing of NSLs at the behest of other agencies that are not authorized to access this sensitive information on their own. In addition, the ACLU is requesting all documents indicating how the FBI has interpreted and used its power to silence NSL recipients since the Patriot Act’s gag provision was amended in 2006.
More
here.
The Art of Surveillance

Amazingly interesting images and commentary.
Via Wired.
Yikes! Beer Burglar Steals 450 Kegs From Guinness Brewery

Via USA Today's "On Deadline" Blog.
In a daring and apparently unprecedented bit of crime, someone broke into the Guinness brewery in Dublin yesterday and stole 450 kegs of beer and stout. And the manhunt is on.
Ireland's national police force, the Garda Siochana, announced the nationwide manhunt earlier today. A lone man drove into the brewery Wednesday and hitched a fully loaded beer trailer to his truck, driving away with 180 kegs of Guinness stout, 180 kegs of Budweiser and 90 kegs of Danish beer Carlsberg. Guinness brews the latter two under license.
The kegs held the equivalent of 39,600 British pints and they had a value of about $235,000, the police estimated.
More
here.
Millions Of Personal Computers Can Be Unknowing Accomplices In Major Cyber Crimes
Via CBS News.
Serry Winkler was startled by a knock on her Denver apartment door last year. Three uniformed police officers with a warrant - for her computer.
Unbeknownst to Winkler, she had become both an unwitting accomplice and a victim to a crime, CBS News science and technology correspondent Daniel Sieberg reports.
“Your house has been broken into and you didn't even know it,” Winkler said.
A hacker, based in Russia, used the Internet to infiltrate Winkler’s computer and steal a credit card to make fraudulent purchases in her name.
More
here.
Cyber Crime Glimpse: Making $1M a Month
Kelly Jackson Higgins writes on Dark Reading's "I, Shadow":
If software vulnerabilities are costing the U.S. $180 billion per year as David Price says in his new book, "Geekconomics: The Real Cost of Insecure Software," just how much are the bad guys making?
Price, director of the Monterey Group and a SANS course instructor, says we really don't know. But there are some shocking examples of just how lucrative cybercrime can be, Price says.
Take the infamous 76service.com, which was run by two enterprising criminals who call themselves 76 and Exoric. The two (who are now apparently on the lam) cleared a cool one million dollars per month in a scheme modeled after portfolio investments, Price says.
They sold access to infected PCs (think bots), but apparently didn't do any of the data-stealing themselves, he says. "The 76service sold all these 'owned' machines in what they called a 'project,'" Rice explains. The buyer would harvest any valuable data off the machine, and sell that information to the black market.
More
here.
Online Casinos Serving Up Malware

My esteemed colleague, Dancho Danchev, explains that when you decide to venture into some neighborhoods in the Internet, you may get more that you bargained for.
In this case, Danchev explains that "...three online casinos are currently serving embedded malware in the form of IFRAMES and the average javascript obfuscation."
Details here.
SCADA Watch: Insider Charged With Hacking California Canal System
Robert McMillan writes on ComputerWorld:
A former employee of a small California canal system has been charged with installing unauthorized software and damaging the computer used to divert water from the Sacramento River.
Michael Keehn, 61, former electrical supervisor at the Tehama Colusa Canal Authority (TCAA) in Willows, Calif., faces 10 years in prison on charges that he "intentionally caused damage without authorization to a protected computer," according to Keehn's Nov. 15 indictment. He did this by installing unauthorized software on the TCAA's Supervisory Control and Data Acquisition (SCADA) system, the indictment states.
Keehn accessed the system on or about Aug. 15, according to the indictment. He is set to appear in federal court on Dec. 4 to face charges of computer fraud.
As an electrical supervisor with the authority, he was responsible for computer systems and is still listed as the contact for the organization's Web site.
More
here.
JPL Scientists Stand Up To Government For Right To Privacy

Loretta Hidalgo Whitesides writes on The Wired Blog Network:
Next week 28 NASA Jet Propulsion Lab scientists (including William Banerdt, a project scientist on the Mars rover program) will fight for their right to privacy in the U.S. Ninth Circuit Court of Appeals in Pasadena, California.
They are fighting against Homeland Security Presidential Directive-12 (HSPD-12) that President Bush issued in August 2004. Policies resulting from the directive requires all federal employees and contractors to "voluntarily" (JPL employees would be terminated immediately for non-compliance) sign a form allowing the government the right to investigate them "without limit" for two years- even if they leave government work during that time.
The directive is meant to confirm the identity of all government employees and give them new high-tech badges, the JPL scientists say they have gone too far.
More
here.
Hat-tip: /.
Quote of the Day [2]: Daniel Terdiman
"But they would never do that, because giving their fans what they want is somehow not a desirable thing for the league."
- Daniel Terdiman, writing on the C|Net "Geek Gestalt" Blog, and also capturing my sentiment on the topic of putting Prime Time NFL games behind a pay channel.
TSA Plan to Gather More Traveler Data Protested

Thomas Frank writes on USA Today:
A government proposal to start collecting birth dates and genders of people reserving airline flights is drawing protests from major airlines and travel agencies that say it would be invasive, confusing and "useless."
The Transportation Security Administration (TSA) wants passengers to give the additional personal information — as well as their full names — so it can do more precise background checks that it says will result in fewer travelers being mistaken for terrorists. Travelers currently must provide only a last name and a first initial.
Airlines say passengers will resist providing more details and that the process will be time-consuming.
More
here.
Domestic Spying, Inc.
Tim Shorrock writes on CorpWatch:
A new intelligence institution to be inaugurated soon by the Bush administration will allow government spying agencies to conduct broad surveillance and reconnaissance inside the United States for the first time. Under a proposal being reviewed by Congress, a National Applications Office (NAO) will be established to coordinate how the Department of Homeland Security (DHS) and domestic law enforcement and rescue agencies use imagery and communications intelligence picked up by U.S. spy satellites.
If the plan goes forward, the NAO will create the legal mechanism for an unprecedented degree of domestic intelligence gathering that would make the U.S. one of the world's most closely monitored nations. Until now, domestic use of electronic intelligence from spy satellites was limited to scientific agencies with no responsibility for national security or law enforcement.
More
here.
(Props, Pogo Was Right.)
News Websites Seek More Search Control
An AP newswire article, via The New York Times, reports that:
Leading news organizations and other publishers have proposed changing the rules that tell search engines what they can and can't collect when scouring the Web, saying the revisions would give site owners greater control over their content.
Google Inc., Yahoo Inc. and other top search companies now voluntarily respect a Web site's wishes as stated in a document known as ''robots.txt,'' which a search engine's indexing software, called a crawler, knows to look for on a site.
Under the existing 13-year-old technology, a site can block indexing of individual Web pages, specific directories or the entire site. Some search engines have added their own commands to the rules, but they're not universally observed.
The Automated Content Access Protocol proposal, unveiled Thursday by a consortium of publishers at the global headquarters of The Associated Press, seeks to have those extra commands -- and more -- apply across the board.
More
here.
Quote of the Day: The International Herald Tribune
"When the government is allowed to show up unannounced without a warrant and search people's homes, it is bad news for all of us."
- An OpEd Commentary in The International Herald Tribune, on "San Diego County's district attorney has a program called Project 100 Percent that is intended to reduce welfare fraud. Applicants for welfare benefits are visited by law enforcement agents, who show up unannounced and examine the family's home - including the insides of cabinets and closets. Applicants who refuse to let the agents in are generally denied benefits."
UK Headed for Cyber 'Cold War'
Rhys Blakely and Jonathan Richards write in The Times Online:
Government and military computer systems in the UK are coming under sustained attack from China and other countries, a major new study gives warning today.
The closely-read annual Virtual Criminology Report, which draws on interviews with senior staff at organisations including the Serious Organised Crime Agency, NATO and the FBI, says that the UK has entered a “cyber cold war” in which web-based espionage poses the biggest threat to national security.
It envisages a future where rogue governments and criminal gangs regularly target the computer systems that run electricity, air traffic control, financial markets and Government computer networks.
Dr Ian Brown of Oxford University, one of the report’s authors, said: “We know that UK computer networks have been probed by China. The means to carry out ‘cyber-warfare’ have been under development for years. Now is the first time that we are seeing states flex their muscles.”
More
here.
McAfee: World Faces 'Cyber Cold War' Threat
Peter Griffiths writes for Reuters:
A "cyber cold war" waged over the world's computers threatens to become one of the biggest threats to security in the next decade, according to a report [.pdf] published on Thursday.
About 120 countries are developing ways to use the Internet as a weapon to target financial markets, government computer systems and utilities, Internet security company McAfee said in an annual report.
Intelligence agencies already routinely test other states' networks looking for weaknesses and their techniques are growing more sophisticated every year, it said.
More
here.
FBI: 'Bot Roast II' Nets 8 Individuals
Via FBI.gov.
The FBI today announced the results of the second phase of its continuing investigation into a growing and serious problem involving criminal use of botnets. Since Operation 'Bot Roast' was announced last June, eight individuals have been indicted, pled guilty, or been sentenced for crimes related to botnet activity. Additionally, 13 search warrants were served in the U.S. and by overseas law enforcement partners in connection with this operation.
This ongoing investigative effort has thus far uncovered more than $20 million in economic loss and more than one million victim computers.
More
here.
Quote of the Day [2]: Walter Shapiro
"Rarely has a debate left me so troubled about the future of the nation."
- Walter Shapiro, writing on Salon.com, regarding the lackluster GOP CNN/YouTube debate debacle.
A Hacker Dream Come True: Adobe and Yahoo! Tests Ads Inside PDF Documents
Eric Auchard writes for Reuters:
Software maker Adobe Systems Inc and Internet company Yahoo Inc said on Wednesday they will offer a service to let publishers run advertisements in Adobe's popular document-reading format.
The new service, Ads for Adobe PDF Powered by Yahoo, presents publishers with an alternative to conventional subscriptions, which, if widely adopted, could open up a new model based on free, ad-supported publishing, analysts said.
More
here.
How Does Bruce Schneier Protect His Laptop Data? With His Fists — and PGP
 "Bruce Schneier's passphrase is used to etch diamonds."
"Bruce Schneier's passphrase is used to etch diamonds."Bruce Schneier
writes on
Wired's Security Matters:
Computer security is hard. Software, computer and network security are all ongoing battles between attacker and defender. And in many cases the attacker has an inherent advantage: He only has to find one network flaw, while the defender has to find and fix every flaw.
Cryptography is an exception. As long as you don't write your own algorithm, secure encryption is easy. And the defender has an inherent mathematical advantage: Longer keys increase the amount of work the defender has to do linearly, while geometrically increasing the amount of work the attacker has to do.
Unfortunately, cryptography can't solve most computer-security problems. The one problem cryptography can solve is the security of data when it's not in use. Encrypting files, archives -- even entire disks -- is easy.
More
here.
Image source: Bruce Schneier Facts
Internet Advertiser Settles With FTC
Roy Mark writes on eWeek:
An online advertiser touting free electronics products agreed Nov. 28 to pay a $650,000 civil fine for misleading consumers. A Federal Trade Commission complaint charged that Adteractive failed to disclose that consumers have to spend money to receive the so-called "free" gifts it offers.
According to the FTC, Adteractive—doing business as FreeGiftWorld.com and SamplePromotionsGroup.com—used deceptive spam and online advertising to lure consumers to its sites. The settlement, filed by the Department of Justice on behalf of the FTC, also requires Adteractive, of San Francisco, to disclose the costs and obligations to qualify for the advertised gifts and bars it from sending e-mail that violates the CAN-SPAM Act.
More
here.
Quote of the Day: Ron Paul
"The Department of Homeland Security is the biggest bureaucracy we ever created."
- Rebublican Presidential Candidate Ron Paul, during the CNN/YouTube debate tonight.
RBN: Google Search Exploits

Via RBN Exploit.
The Russian Business Network (RBN) has been busy again with a significant amount of loaded web search results which lead to malware sites as reported by Sunbelt.
The good news first is being able to precisely pin point the exploiters back to newer RBN core retail centers as previously exposed in this blog on Nov 8th 07 – i.e. iFramecash, myrdns, hostfresh, and AS 27595 i.e. Atrivo, Intercage, Inhoster. Also as reported this is the same end route as the Bank of India hack, fake anti-spywares and fake codecs.
The bad news is, as predicted and one of the probable reasons for dropping their RBnetwork IP ranges , the RBN is increasingly using botnet based fast-flux techniques (see Wikipedia) to hide the initial delivery sites behind an ever-changing network of compromised hosts i.e. "double-flux" nodes within the network registering and de-registering their addresses as part of the DNS SOA (start of authority) record list for the DNS (domain name server). This provides an additional layer of redundancy and survivability within the malware network as seen in the case of the fake codecs.
More
here.
Image source: RBN Exploit
Google's Storage Plans Raise Plenty of Concerns
Frederick Lane writes on CIO Today:
In the wake of this week's buzz about Google's plans for a new online service for file storage, Internet privacy specialists are raising concerns about the potential vulnerability of such data to government investigations.
Such fears have been heightened by a variety of high-profile attempts by federal investigators to retrieve user information from online companies, including Amazon, Yahoo, MSN, and Google itself.
More
here.
Congress' 'Anti-Extremist' Bill Targets Online Thought-Crime
Declan McCullagh writes on the C|Net 'Iconoclast' Blog:
Congress is about to approve the Violent Radicalization and Homegrown Terrorism Prevention Act [VRAHTPA] of 2007. This is not necessarily a good thing for Internet users.
I say that because VRAHTPA establishes a new federal commission tasked with investigating Americans with "extremist belief systems" and those who may engage in "ideologically based violence." This effort is expected to cost $22 million.
It's possible, of course, that nothing will come of VRAHTPA. Technically no new laws are being proposed except those creating the so-called National Commission on the Prevention of Violent Radicalization and Homegrown Terrorism.
But creating a homeland security commission staffed primarily by Washington types with security clearances, which will be run by Washington antiterror types, which meets mostly in secret, and which will present a classified report to the president about "extremist belief systems"--well, that has the potential to turn ugly.
More
here.
Verizon’s 'Open' Network Will Really Be Two-Tiered
Erick Schonfeld writes on TechCrunch:
Verizon’s newfound openness when it comes to its wireless network is not all that open after all. As I reported yesterday, Verizon Wireless announced that it would allow “any device” and “any app” to operate on its existing network.
But that is not exactly so.
More
here.
Reported Malfunction in PayPal Security Key

Dan Goodin writes on Channel Register:
When eBay rolled out the PayPal Security Key earlier this year, its executives hailed it as an important measure that would make users more secure. And it was. By generating a random, six-digit number every 30 seconds that users needed to authenticate themselves online, the small electronic token provided an additional layer of protection against phishers and other online criminals.
But according to Chris Romero, an IT administrator who has used the Security Key for several months now, a bug could allow phishers and others with bad intent to work around the measure. When accessing his PayPal account from merchant sites and other third-party destinations, he says, his account is validated when he types in any six-digit number, as long as he provides a valid user id and password and answers an accompanying security question.
More
here.
Image source: mmidona
No Surprise Here: 'Fusion' Centers Losing Anti-Terror Focus

An AP newswire article by Eileen Sullivan, via Google News, reports that:
Local intelligence-sharing centers set up after the Sept. 11, 2001, attacks have had their anti-terrorism mission diluted by a focus on run-of-the-mill street crime and hazards such as hurricanes, a government report concludes.
Of the 43 "fusion centers" already established, only two focus exclusively on preventing terrorism, the Government Accountability Office found in a national survey obtained by The Associated Press. Center directors complain that they were hampered by lack of guidance from Washington and they were flooded by often redundant information from multiple computer systems.
More
here.
Image source: Robert A. Reeder / The Washington Post
EFF Wins Fast-Track Release of Telecom Lobbying Records
Via The EFF.
Late Tuesday, the Electronic Frontier Foundation (EFF) won the speedy release of telecom lobbying records from the Office of the Director of National Intelligence (ODNI).
The agency was ordered to comply with a new December 10 deadline -- in time for the documents to play a role in the congressional debate over granting amnesty for telecommunications companies taking part in illegal electronic surveillance. The ruling by U.S. District Judge Susan Illston vacates a hearing on the matter previously scheduled for Friday.
More
here.
Did Fed Lawyer Use Geeks-on-Call to Erase Gov't Computer Evidence?
Kim Zetter writes on Threat Level:
Scott Bloch, head of the Office of Special Counsel who has been under investigation for retaliation against employees and failure to investigate whistleblower cases, is under suspicion for using Geeks-on-Call to erase all the files on his office computer last year as well as laptops belonging to two of his former deputies.
Block claims that he had Geeks-on-Call delete all of his computer files and erase his hard drive because his computer had been seized by a virus. But he apparently bypassed his own agency's IT department when he brought in the outside geeks to do the clean-up. And, as the Wall Street Journal reports, the receipt for the work makes no mention of a virus.
Furthermore, the kind of erase Geeks-on-Call conducted on his computer -- a seven-level wipe -- is considered excessive for treating a virus. As the head of Geeks-on-Call's Washington office told the WSJ, "We don't do a seven-level wipe for a virus."
More
here.
'Crackstation' Uses Game Console for Hacking

A ComputerWorld Australia article by Ulrika Hedquist, via PC World, reports that:
Nick Breese, a senior security consultant at Auckland, Australia-based Security-assessment.com, has come up with a way to drastically increase the processing capability of cracking passwords.
By implementing common ciphers and hash functions using vector computing, Breese has pushed the current upper limit of 10--15 million cycles per second -- in Intel-based architecture -- up to 1.4 billion cycles per second.
Breese, who has been working on the project, called "Crackstation", for the past six months, used the Sony PlayStation 3 gaming console for his break-through research. PS3's Cell Broadband Engine technology was created by IBM, Toshiba and Sony.
More
here.
U.S. Toll in Iraq

Via The Boston Globe (AP).
As of Tuesday, Nov. 27, 2007, at least 3,878 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,159 died as a result of hostile action, according to the military's numbers.
The AP count is three higher than the Defense Department's tally, last updated Tuesday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
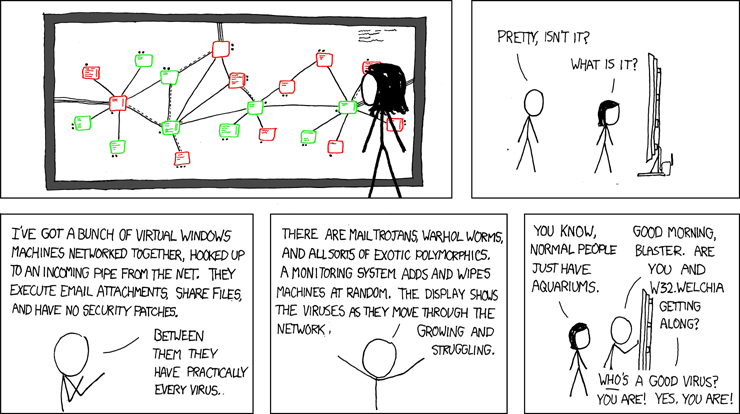
Best. xkcd. Ever.
Click for larger image.
We
simply love xkcd.
And this is just
marvelous!
-ferg
Bizarre Story of the Day: Internet User Sentenced for Killing Romantic Rival

An AP newswire article by Carolyn Thompson, via The Boston Globe, reports that:
A 48-year-old man entangled in an Internet love triangle built largely on lies was sentenced Tuesday to 20 years in prison for killing his rival for the affection of a woman he had never met.
Thomas Montgomery, who posed as an 18-year-old Marine in online chats, pleaded guilty in August to gunning down Brian Barrett, 22, in a parking lot at the suburban Buffalo factory where they worked.
The motive was jealousy, investigators said. Both were involved online with a middle-aged West Virginia mother -- who herself was posing as an 18-year-old student.
More
here.
Friendly Rootkits? Please Tell Me This is a Joke...
Liam Tung writes on ZDNet Australia:
Secure Socket Layer (SSL) certificates have made e-commerce more secure, according to VeriSign, but a US security researcher reckons benevolent rootkits served by the retailer might do a better job.
SSL certificates are issued to merchants by Certificate Authorities to indicate to the consumer it is a legitimate business. The rootkit which Dan Geer, VP and chief scientist at security company Verdasys, has proposed would take over the security function of a customer during a transaction by placing it within the merchant's trusted environment.
Geer proposes that merchants ask their customers whether they would like an "extra special secure connection" prior to making a transaction. If a user says "Yes", the merchant could install the rootkit on a customer's PC to make the transaction safe.
More
here.
Note: "Extra special?" Yeah, well
Sony tried that (without asking) and I can assure you that any effort along these lines will end up the same way -- making consumers more vulnerable.
That is a very, very bad idea.
-ferg
Quote of the Day [2]: Mike Masnick
"Can someone please explain how Morris keeps his job?"
- Mike Masnick, over on techdirt.com, commenting on Universal Music CEO Doug Morris' completely misplaced priorities, which "...appear[s] to be focused on squeezing every immediate dime out of anyone he can, even if it means destroying the company's long-term prospects."
NSA Licenses Mikoh RFID Technology
Via UPI.
The U.S. National Security Agency announced plans to license reusable closure mechanism intellectual property to Washington-based Mikoh Corp.
Mikoh is a security and digital marking products provider that specializes in the physical security of radio frequency identification [RFID] tags. Officials say the finalized deal with the NSA is an initiative to expand Mikoh's Smart & Secure tamper-evident RFID tags and seals applications.
More
here.
Judge: Gov't Can't ID Online Book Buyers

An AP newswire article, via CBS News, reports that:
U.S. prosecutors have withdrawn a subpoena seeking the identities of thousands of people who bought used books through online retailer Amazon.com Inc., newly unsealed court records show.
The withdrawal came after a judge ruled the customers have a right to keep their reading habits from the government.
"The (subpoena's) chilling effect on expressive e-commerce would frost keyboards across America," U.S. Magistrate Judge Stephen Crocker wrote in a June ruling.
"Well-founded or not, rumors of an Orwellian federal criminal investigation into the reading habits of Amazon's customers could frighten countless potential customers into canceling planned online book purchases," the judge wrote in a ruling he unsealed last week.
More
here.
SCADA Watch: House Committee on Homeland Security Urges FERC Chairman to Investigate Grid Security

John M. Powers writes on Utilities Online:
Concerned about the results of a secret experiment conducted for the Department of Homeland Security (DHS) in which a generator was destroyed by a cyber attack, the House Committee on Homeland Security urged Federal Energy Regulatory Commission (FERC) chairman Joseph Kelliher to investigate the implementation of certain measures to mitigate security vulnerabilities across the electricity sector.
The request came in the form of a letter to Kelliher from committee members James Langevin (D-RI), Michael McCaul (R-TX), and Shelia Jackson-Lee (D-TX).
More
here.
Image source: Encarta
Phrase (and Image) of the Day: SEOwN3d

Props to Jeremiah Grossman (Whitehat Security).
Nice touch. Watch the 133t spelling, though. :-)
Background here.
-ferg
Canada: Reckless Data Handling Could Violate ID Theft Law
Kathleen Lau writes on ComputerWorld Canada:
The recently proposed amendment to the Criminal Code that would make "reckless" handling of personal information a crime can be troubling given the broad definition of the word, said one lawyer.
If Bill C-27 is passed, it will be an offense to make available or sell personal information (such as names, addresses bank account information and social insurance numbers) knowing it will be used to commit fraud – or if the person or company selling the information is reckless as to whether the data will be used for fraud by a third party.
More
here.
UK: Data Protection Minister Did Not Know About HMRC Breach
Tash Shifrin writes on ComputerWorld UK:
The government’s data protection minister did not know about the huge data breach at HM Revenue and Customs until he heard the chancellor’s statement in the Commons on 20 November, he has admitted.
Chancellor Alistair Darling said he had been told of the data breach – in which CDs containing the details of 25 million people were lost in transit between HMRC and the National Audit Office – on 10 November.
But data protection minister Michael Wills was forced to admit to parliament’s joint committee on human rights that Darling’s Commons speech was the first he had heard of Britain’s biggest ever data breach.
More
here.
Database Admin to Plead Guilty in Theft of 8.5M Consumer Records
Jaikumar Vijayan writes on ComputerWorld:
A senior database administrator at a subsidiary of Fidelity National Information Services Inc. (FIS) who was accused of stealing about 8.5 million customer records and selling them to data brokers is expected to plead guilty tomorrow to felony fraud charges in U.S. District Court in Tampa, according to court documents.
William G. Sullivan has also agreed to pay court-ordered restitution to victims, cooperate with ongoing investigations and forfeit the more than $105,000 he still has remaining from selling the stolen data. In exchange, according to a plea agreement also filed with the court, federal prosecutors are expected to recommend a reduction from the maximum five-year sentence that Sullivan could have gotten.
More
here.
U.S. Working To Respond To Growing Cyber Attacks
A Reuters newswire article, via InformationWeek, reports that:
The United States is working to prevent attacks on military, government and private computer networks, but any aggressive response raises legal, civil rights and policy questions that should be addressed, a U.S. military adviser said Tuesday.
At the moment, "there are no rules" about what government or private entities can do if their networks are attacked, said Andrew Palowitch, chief technology officer for Science Applications International Corp's intelligence and security group and senior adviser to the Pentagon.
Given more than 37,000 attempted breaches of government and private programs and 80,000 attacks on military networks in fiscal 2007 alone, some would argue the United States was already in a "cyber war," he said in a speech at Georgetown University in Washington. He said he was not speaking for the Pentagon.
More
here.
Quote of the Day: Anonymous

"The only things left after a nuclear war are you and cockroaches."
- Anonymous comment on a "vulgar greeting card" left in the Palm Beach, Florida, mailbox of Ann Coulter. According to The Smoking Gun, "The pink and white card, which had 'Go fuck yourself' printed on its face, included several denigrating handwritten statements..."
Image source: www.whitehouse.org
e- Books, Credit Card Theft, and Equifax
Bob Sullivan writes on The Red Tape Chronicles:
Chris Jupin never thought he'd create a firestorm when he wrote on his personal blog in September about a bogus $4.95 charge that appeared on his debit card. But traffic to his blog increased sharply, and hundreds of Web users chimed in saying, "me too." About half of them had something in common: They had recently purchased credit services from credit bureau Equifax.
Jupin's short post complained about a company named Digismarket.com, which says on its Web site that it sells electronic books. The company lists a New York State phone number. Jupin, a 25-year-old from Atlanta, had never heard of Digismarket, and had never ordered electronic books. He immediately canceled his credit card and e-mailed the company asking for a refund of the $4.95 charge, which it granted quickly.
More
here.
Windows XP Significantly Outperforms Vista, Tests Show
Paul McDougall writes on InformationWeek:
In the latest Mac versus PC ad, that put-upon Windows guy quietly concedes he's "downgrading" from Vista to XP. He may have good reason: new tests show that the older XP runs common productivity tasks significantly faster than Microsoft's newest operating system.
Researchers at Devil Mountain Software, a Florida-based developer of performance management tools, have posted data from their most recent Windows performance tests -- and Vista, even after it's been upgraded to the new Service Pack 1 beta package, is shown to be a laggard.
"The hoped for performance fixes [from Vista SP1] that Microsoft has been hinting at never materialized," said Devil Mountain researchers, in a blog post summarizing their results.
More
here.
Numbers: Telcos Plan for Converged Voice/Data/Video Networks--But Not Security
Katherine Walsh writes on CSO Online:
A recent survey of global telecom carriers conducted by IBM found that 85 percent of carriers plan to roll out IP-based next-generation networks (NGNs) within the next five years. NGNs represent the convergence of voice, data and video onto one network. But according to the survey, the 2007 State of Security in Carrier Service Delivery, NGNs pose inherent security risks that carriers are not equipped to deal with. Only 46 percent of those surveyed said they have a strategy in place for addressing security risks posed by NGNs.
Because NGNs are based on IP, a highly exploited protocol, they will likely be prone to the same security issues affecting the Internet. Nearly 36 percent of those surveyed said that security issues are impeding their rollout of service bundles that include television, Internet and telephony. However, that number is down from 55 percent in 2006.
More numbers
here.
ENISA Calls for Stronger Prosecution of Cyber Criminals
Via The European Network and Information Security Agency (ENISA).
ENISA is launching its latest Position Paper [.pdf] on 'botnets', i.e. silent, 'hijacked' computers. The paper identifies roles and structures of criminal organizations for creating and controlling botnets, and trends in this type of cyber crime.
In particular, it is often overlooked that browser exploits account already for more than 60% of all infections. Clicking on a malicious link may be enough to get infected. The main problem is uninformed users. Consequently, ENISA calls for an agreement to address this security threat in a more consistent way. The paper also identifies online tools to identify and counter malicious code.
More
here.
(Hat-tip: FIRST.org Global Security News)