Russia Celebrates Secret Police Day

Via Georgian Daily.
Today, 91 years ago Felix Dzerzhinsky founded national secret police organization - Cheka, later renamed to NKVD and then to KGB. During the late 1980s, as the Soviet government and economy were disintegrating, the KGB survived better than most state institutions, suffering far fewer cuts in its personnel and budget.
Following the attempted coup of 1991 (in which some KGB units participated) against Soviet leader Mikhail Gorbachev, the KGB was dismantled and formally ceased to exist from November 1991.
In late 1991 the domestic security functions of the KGB were reconstituted as the Federal Counterintelligence Service (FSK), which was placed under the control of the president. The FSK had been known initially for some time as the Ministry of Security. In 1995, the FSK was renamed and reorganized into the FSB by the Federal Law of April 3, 1995, "On the Organs of the Federal Security Service in the Russian Federation", granting it additional powers, enabling it to enter private homes and to conduct intelligence activities in Russia as well as abroad in cooperation with the Russian Foreign Intelligence Service (SVR).
More
here.
Time's Person of The Year 2008: Barack Obama
U.S. Toll in Iraq, Afghanistan

Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Friday, Dec. 20, 2008, at least 4,209 members of the U.S. military had died in the Iraq war since it began in March 2003, according to an Associated Press count.
The figure includes eight military civilians killed in action. At least 3,397 military personnel died as a result of hostile action, according to the military's numbers.
The AP count is two fewer than the Defense Department's tally, last updated Friday at 10 a.m. EST.
As of Friday, Dec. 19, 2008, at least 558 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures Friday at 10 a.m. EST.
Of those, the military reports 405 were killed by hostile action.
More
here and
here.
And as always, the
Iraq Coalition Casualty Count keeps the grim watch on their website
here.
Honor the Fallen.
Ye Olde Christmas Party 2008

It's that time of year again -- the annual company Christmas Party.
Luckily, this year my company (Trend Micro) held our Christmas Party at the Computer History Museum in Mountain View. Pretty cool, huh?
Of course, I showed up with my "better half" for some free drinks, free grub, and some great Big Band music. And of course, we also brought a toy for Toys for Tots.
The picture above (admittedly not the best) is of Yours Truly, standing in front of one the few original Charles Babbage' Difference Engines (Charles Babbage poster hanging in the background).
That -- in and of itself -- was worth the trip.
Happy Holidays to you, and yours.
- ferg
In Passing: Dock Ellis

U.S. Commerce Dept. Adds Concerns About New TLDs
Chloe Albanesius writes on PC Magazine:
The Commerce Department on Thursday expressed concern [.pdf] with a plan from the Internet's governing body to expand the number of top-level domain names (TLDs).
In June, the Internet Corporation for Assigned Names and Numbers (ICANN) approved a plan that would broadly expand the number of TLDs that, for now, have been restricted to a few choice designations.
The plan it two-fold and would allow the use of non-Latin characters, such as Mandarin, to be used as TLDs, as well as any combination up to 64 characters. As a result, Web site owners could create an endless number of domain name combinations like pcmag.zd or intel.inside, instead of the usual ".com,", ".org,", or ".gov" endings.
In October, ICANN opened up the plan for public comment, and Commerce's National Telecommunications and Information Administration on Thursday questioned whether ICANN would be able to adequately execute the plan.
More
here.
Friday Monkey Blogging: Flatulent Gorillas Force Brussels Sprouts Off Zoo's Christmas Menu

As I mentioned last month, I have started a regularly recurring blog entry meme every Friday afternoon, inspired by Bruce Schneier's regular series of "Friday Squid Blogging" posts, and my very own maddening Monkey Theory.
Here is this week's installment.
Via The London Paper.
Zoo managers have taken Brussels sprouts off the Christmas menu after the vegetable caused an attack of flatulence in their gorillas.
The staff at Chessington Zoo fed the giant apes on the seasonal favourite as they are filled with nutritional goodness. However, they hadn't reckoned with the gassy qualities of the tiny veggies.
Now the zoo has issued an apology after guests at the zoo expressed their horror at the potent smell that started emanating from the gorillas' enclosure.
Gorilla keeper Michael Rozzi said: "We feed the gorillas brussel sprouts during the winter because they are packed with vitamin C and have great nutritional benefits."
"Unfortunately, an embarrassing side effect is that it can cause bouts of flatulence in humans and animals alike."
"However, I don't think any of us were prepared for a smell that strong."
More
here.
Hat-tip: Monkeys in The News
The Other Side of 'Deep Throat': Domestic Spying
Greg Mitchell writes on Editor & Publisher:
Journalists and many others (rightly) lionizing the late W. Mark Felt, the former FBI official, for his contribution as "Deep Throat" in helping to bring down Richard Nixon, should not overlook the fact that Felt was one of the architects of the bureau's notorious COINTELPRO domestic spying-and-burglary campaign.
He was convicted in 1980 of authorizing nine illegal entries in New Jersey in 1972 and 1973 -- the very period during which he was famously meeting Bob Woodward in a parking garage. Only a pardon, courtesy of Ronald Reagan, kept him out of jail for a long term.
So the man knew a thing or two about illegal break-ins. COINTELPRO was George W. Bush's domestic spying programs on steroids.
More
here.
Undersea Cable Cuts Disrupt Internet Access
Robert McMillan writes on PC World:
Internet and telephone traffic between Europe and the Middle East and Asia was hampered Friday after three major underwater data lines were cut, according to France Telecom.
The cut occurred on lines between 07:28 and 08:06 Coordinated Universal Time (UTC) on lines in the Mediterranean sea that connect Sicily to Tunisia and Egypt, the telecommunications company said.
The cuts were to the Sea Me We 4 and Sea Me We 3 lines, which connect countries between Singapore and France as well as the Flag cable route, which stretches from the U.K. to Japan, a France Telecom spokeswoman who asked not to be named said.
France Telecom isn't sure what caused the cut, she said. "We have two assumptions. The first is that it could be an underwater earthquake," she said. "Or it could be simply a ship in the area which has cut the cable."
More
here.
U.S. Not Ready for Cyber Attack
A Reuters newswire article, via The New York Times, reports that:
The United States is unprepared for a major hostile attack against vital computer networks, government and industry officials said on Thursday after participating in a two-day "cyberwar" simulation.
The game involved 230 representatives of government defense and security agencies, private companies and civil groups. It revealed flaws in leadership, planning, communications and other issues, participants said.
The exercise comes almost a year after President George W. Bush launched a cybersecurity initiative which officials said has helped shore up U.S. computer defenses but still falls short.
"There isn't a response or a game plan," said senior vice president Mark Gerencser of the Booz Allen Hamilton consulting service, which ran the simulation. "There isn't really anybody in charge," he told reporters afterward.
Democratic U.S. Rep. James Langevin of Rhode Island, who chairs the homeland security subcommittee on cybersecurity, said: "We're way behind where we need to be now."
More
here.
Hacking The Hill
Shane Harris writes in The National Journal:
On October 26, 2006, computer security personnel from across the legislative branch were informed that the Congressional Budget Office had been hit with a computer virus. The news might not have seemed extraordinary. Hackers had been trying for years to break into government computers in Congress and the executive branch, and some had succeeded, making off with loads of sensitive information ranging from codes for military aircraft schedules to design specifications for the space shuttle.
Employees in the House of Representatives' Information Systems Security Office, which monitors the computers of all members, staffers, and committee offices, had learned to keep their guard up. Every year of late, they have fended off more than a million hacking attempts against the House and removed any computer viruses that made it through their safeguards. House computers relay sensitive information about members and constituents, and committee office machines are especially loaded with files pertaining to foreign policy, national security, and intelligence. The security office took the information from the CBO attack and scanned the House network to determine whether any machines had been compromised in a similar fashion.
They found one. A computer in one member's office matched the profile of the CBO incident. The virus seemed to be contacting Internet addresses outside the House, probably other infected computers or servers, to download malicious files into the House system. According to a confidential briefing on the investigation prepared by the security office and obtained by National Journal, security employees contacted the member's office and directed staffers to disconnect the computer from the network. The briefing does not identify the member of Congress.
More
here.
Toon of The Day: You Can't Dodge This One

Image source: Mike Keefe / PoliticalCartoons.com
In Passing: W. Mark Felt

Researchers Hone In On 'Dropzones' For Stolen Credentials
Kelly Jackson Higgins writes on Dark Reading:
German researchers have discovered more than 300 cybercrime servers full of stolen credentials on more than 170,000 people -- and it is only the tip of the iceberg, they say.
Researchers at the University of Mannheim's Laboratory for Dependable Distributed Systems were able to access nearly 100 so-called "dropzone" machines, and say the actual number of these servers is much more.
"With our limited amount of machines, we found more than 300 dropzones, and we covered only two families of banking Trojans. In total, there are presumably many more," says Thorsten Holz, one of the researchers and a founder of the German Honeypot Project. The researchers were studying what they call "impersonation attacks," where victims' credentials are stolen so that the attacker can impersonate them.
The researchers basically traced the steps [.pdf] of specific keyloggers and banking Trojans between April and October 2008. One-third of the machines infected by this data-stealing malware are in Russia or the U.S., according to the researchers. Overall, the 170,000 victims whose data they discovered in the dropzones were from 175 different countries.
They discovered a total of 10,775 bank account credentials, including passwords and bank account details that the victims would enter during a regular transaction. They also found more than 5,600 credit card accounts and tens of thousands of passwords for various sites.
More
here.
Classic xkcd: 11th Grade Activities
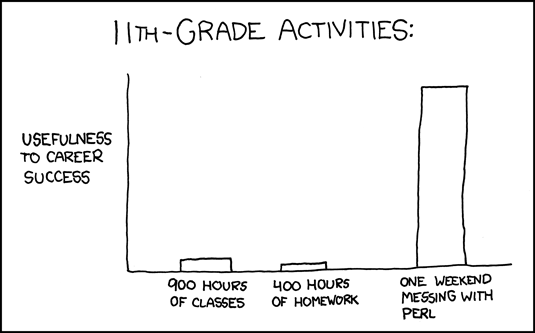 Click for larger image.
Click for larger image.We
love xkcd.
Enjoy!
- ferg
In Passing: Sam Bottoms

Online Jihadists Plan for 'Invading Facebook'
Noah Shachtman writes on Danger Room:
Online jihadists have already used YouTube, blogs and other social media to spread their propaganda. Now, a group of internet Islamic extremists is putting together a plan for "invading Facebook."
"We can use Facebook to fight the media," notes a recent posting on the extremist al-Faloja forum, translated by Jihadica.com. "We can post media on Facebook that shows the Crusader losses."
"We have already had great success in raiding YouTube," the poster adds. "American politicians have used Facebook to get votes, like the house slave Obama."
Groups like al-Qaida were pioneering users of the internet — to train, share ideas and organize. But some observers, like George Washington University professor Marc Lynch, see a reluctance to embrace Web 2.0 tools like Facebook. "One of the biggest problems for a virtual network like AQ today is that it needs to build connections between its members while protecting itself from its enemies. That's a filtering problem: How do you get your people in, and keep intelligence agents out?" he asks.
More
here.
Hackers Exploit IE Bug With 'Insidious' Word Docs
Gregg Keizer writes on ComputerWorld:
Attackers are exploiting the just-patched vulnerability in Internet Explorer (IE) by hiding malicious ActiveX controls in Microsoft Word documents, a security company said today.
"Inside the document is an ActiveX control, and in that control is a line that makes it call out to the site that's hosting the malware," said David Marcus, director of security research and communications for McAfee Inc.'s Avert Labs. "This is a pretty insidious way to attack people, because it's invisible to the eye, the communication with the site."
Embedding malicious ActiveX controls in Word documents isn't new -- Marcus said he had seen it "a time or two" -- but using an ActiveX control to ping a hacker's server for attack code is "definitely an innovation," he added. "They're stepping it up."
The rogue documents can be delivered as attachments to spam e-mail or offered up by hacked sites.
More
here.
Quote of The Day: Anonymous Coward
"In other news: HMS Vigilant's captain, Commander Bob Anstey allegedly accidentally fired a nuclear missile at Redmond, Washington in an attempt to complete the Windows Activation of the newly installed 'Submarine Command System Next Generation' customized Windows XP system. 'It was a bug, yes, that's it. Some kind of unfortunate bug triggered the 19-step launch sequence,' said Commander Anstey. Nobody at or near Microsoft could be reached for a comment."
- Seen in a Slashdot comment thread, regarding the news that British Royal Navy Submarines Now Run Windows. Enjoy. -ferg
Mark Fiore: Christmas Corruption

More Mark Fiore brilliance.
Via The San Francisco Chronicle.
Ho, ho, ho.
- ferg
In Passing: Sammy Baugh

Australian Legislator: 'Huawei Is A Security Risk'

An AAP newswire article, via ZDNet Australia, reports that:
The Federal Opposition is demanding the Government explain whether a company involved with the new frontrunner's bid for Australia's National Broadband Network has links with the Chinese military.
Security agencies will closely examine the bid placed by Singtel Optus, which is believed to have asked Chinese firm Huawei Technologies to help build its network, The Australian newspaper has reported.
Huawei has operated in Australia for several years and supplies technology to Optus and a number of other Australian firms relating to their network roll-outs, in addition to some consumer hardware like 3G mobile cards.
Huawei was the subject of a US congressional investigation on national security, after concerns were raised about the company's links to the Chinese military and intelligence apparatus, the report said.
"These are potentially very concerning revelations," opposition communications spokesman Nick Minchin told AAP. The Federal Government had kicked out Telstra — the only Australian publicly-listed company bidding for the NBN — leaving just three national bidders.
The respected global think tank Rand Corporation, which specialises in national security research, says Huawei maintains deep ties with the Chinese military, Senator Minchin said. Cyber espionage was a problem that Australia had to constantly guard against and the new broadband network needed to be "secure or seen to be secure".
More
here.
Analysis: FISMA Not Real Security Measure
A UPI article by Shawn Waterman , via The Middle East Times, reports that:
The Federal Information Security Management Act of 2002 says all federal departments and agencies must conduct yearly assessments to measure their compliance with information security standards in the act.
In May the Justice Department's compliance was rated A-plus by the U.S. House Committee on Oversight and Government Reform.
But FISMA mandates, as the inspector general's report noted, are primarily concerned with ensuring that all agencies "have policies and procedures to enhance the security of information in their IT systems."
The Justice Department's A-plus grade, therefore, "did not assess whether the Department has actually implemented these processes, nor did it assess the actual security of the Department's IT systems."
"Unfortunately, FISMA has become a compliance exercise," said Shannon Kellogg, director of information security policy for EMC Corp. As a result, he said, "even if an agency receives a good grade, it does not mean that that agency has significantly reduced risks to information security or reduced the number of serious cyber incidents."
More
here.
Toon of The Day: Trickle Down Security

Via Tom Toles / Slate.com
Firefox 3.0.5 Update Available
Get it here.
MFSA 2008-69 XSS vulnerabilities in SessionStore
MFSA 2008-68 XSS and JavaScript privilege escalation
MFSA 2008-67 Escaped null characters ignored by CSS parser
MFSA 2008-66 Errors parsing URLs with leading whitespace and control characters
MFSA 2008-65 Cross-domain data theft via script redirect error message
MFSA 2008-64 XMLHttpRequest 302 response disclosure
MFSA 2008-63 User tracking via XUL persist attribute
MFSA 2008-60 Crashes with evidence of memory corruption (rv:1.9.0.5/1.8.1.19)
- ferg
ICANN: Revisions in Proposed Changes to Registrar Accreditation Agreement
Via ICANN.org.
ICANN today posted a revised set of proposed amendments to the Registrar Accreditation Agreement. The amendments are intended to provide additional protections for registrants and improved enforcement tools. These most recent changes include two additional amendments and are a result of public comments received and subsequent community dialogue.
In accordance with RAA defined process for amending the agreement, ICANN has provided a written report describing the broad-based process undertaken to arrive at this set of amendments. This report is designed to inform the GNSO and community discussion of the amendments. There will be another public comment period before the ICANN Board would consider this set of proposed contract changes.
The two new proposed amendments are intended to enhance public availability of Whois data and registrar contact information:
- Licensee Contact Information Disclosure – Requires a Registered Name Holder that licenses use of a domain name to disclose the contact information provided by the licensee under certain circumstances. (Presently, only the identity of the licensee need be disclosed.)
- Registrar Contact Information – Requires registrars to provide their accurate contact details on their websites including valid email and mailing addresses.
An updated redline of the current RAA showing all of the proposed changes is posted at: Updated Redline 2001 RAA [.pdf].
More
here.
As Attacks Escalate, MS Readies Emergency IE Patch
Ryan Naraine writes on the ZDNet "Zero Day" Blog:
Microsoft is planning to ship an emergency Internet Explorer update tomorrow (December 17) to counter an escalating wave of malware attacks targeting a zero-day browser vulnerability.
The out-of-band update, which will be rated critical, follows the public discovery of password-stealing Trojans exploiting the bug on Chinese-language Web sites. Over the past week, the attacks have expanded with hackers using SQL injection techniques to seed exploits on legitimate Web sites.
This will be the second out-of-band update from the MSRC (Microsoft Security Response Center) in the last two months. Back in October, the company shipped MS08-067 to plug an extremely critical worm hole that affected Windows 2000, Windows XP and Windows Server 2003.
The IE patch will be available for all supported versions of the browser. According to this pre-patch advisory from Microsoft, the in-the-wild attacks have targeted IE 7 on Windows XP SP2 and SP3, Windows Server 2003 SP1 and SP2, Windows Vista (including SP1) and Windows Server 2008.
More
here.
AusCERT: Avoid Using IE If Possible
Liam Tung writes on ZDNet Australia:
Australia's Computer Emergency Response Team (AusCERT) has recommended organisations "consider using a web browser other than Internet Explorer until a patch becomes available" — an option that many large firms cannot seriously consider.
The zero-day flaw first reported last Thursday, which Microsoft later admitted affected all versions of Internet Explorer has prompted AusCERT to advise Australian organisations to "consider" using an alternative browser, which could include Opera, Mozilla Firefox, Google Chrome or Safari.
"What we've said is quite specific in our advisory — we've said that users should consider using an alternative browser — if that is possible," AusCERT's general manager Graham Ingram told ZDNet.com.au today.
More
here.
Cyber Crime: The 2009 Mega Threat
Dr. Larry Ponemon writes on CSO Online:
The 2009 Security Mega Trends Survey was conducted by Ponemon Institute and sponsored by Lumension to better understand if certain publicized IT risks to personal and confidential data are, or should be, more or less of a concern for companies. We asked 577 IT security practitioners to consider how 10 Security Mega Trends affect companies today and to predict their impact during the next 12 to 24 months. The opinions of these experts, we believe, will be helpful to companies that are struggling to understand how they should allocate resources to the protection of data during these difficult economic times.
We selected the following mega trends for this study based on input from a panel of experts in IT security. They are: cloud computing, virtualization, mobility and mobile devices, cyber crime, outsourcing to third parties, data breaches and the risk of identity theft, peer-to-peer file sharing and Web 2.0.
The study examined the risks posed by mega trends that exist today and how the risk will change over the next 12 to 24 months. According to an overwhelming 77 percent of individuals in IT security responding to our survey, cyber crime will become a high or very high risk over the next 12 to 24 months.
The selection of cyber crime as the mega trend most likely to be a high or very high risk in the next 12 to 24 months can be partly based on the fact that 92 percent of respondents in our study reported that their companies have had a cyber attack. The biggest security risk associated with cyber crime is that such an attack will cause a business interruption followed by the theft of customer and employee data.
More
here.
Indian Infotech Sector is Main Focus of Chinese Cyber Spying
Via DNA India.
A few months ago, a major Bangalore-based infotech company lost out on a $8 million contract. The company was expecting a business delegation to visit India before signing the contract, but 15 days before the date set for the deal, the meeting was abruptly called off.
The same team went to China instead. When the Indian firm investigated the matter, it discovered a gaping hole in its security. The computers of several of its top executives had been compromised by Chinese hackers and privileged information leaked to a Chinese competitor, who walked away with the deal by quoting a lesser price.
Welcome to war of another kind - corporate espionage. Chinese companies are increasingly spying on the Indian IT industry, the only major business area where India leads the Chinese by several years. With many companies reportedly becoming victims of Chinese espionage, Indian intelligence officers are beginning to take a close, hard look at the influx of Chinese nationals into Bangalore, India’s IT hub.
More
here.
Props: Cyber Crime Updates, via The Dark Visitor
Pellicano Gets 15 Years for Wiretapping Scheme
An AP newswire article, via Law.com, reports that:
Hollywood private eye Anthony Pellicano was sentenced Monday to 15 years in prison for running a wiretapping scheme that spied on the rich and famous.
U.S. District Judge Dale Fischer also ordered the 64-year-old Pellicano and two other defendants to forfeit a total of $2 million.
Pellicano showed no emotion when the sentence was read.
"I have taken full and complete responsibility," he said, dressed in a prison-issued green jacket and pants.
The private eye was convicted of a combined 78 counts, including wiretapping, racketeering and wire fraud, in two separate trials earlier this year.
More
here.
Court Narrows National Security Secrecy, Limits Oversight
David Kravets writes on Threat Level:
A unanimous federal appeals court on Monday narrowed the scope of when telecommunications companies must keep the self-issued FBI search-warrant requests secret.
But the court limited when it was necessary for judges to review a secrecy order.
The appeal concerned various counter-terrorism statutes and the 2006 USA Patriot Act, which allows the FBI to demand information concerning telephone and e-mail communications (among other things) without a warrant under a national security letter, or NSL. The law forbids companies to let a customer know that the bureau has sought information concerning their telephone and e-mail traffic.
Ruling on an American Civil Liberties Union challenge to the gag order provision, the 2nd U.S. Circuit Court of Appeals concluded 3-0 that a carrier must keep the order secret if the FBI certifies that disclosure of the NSL "may result in an enumerated harm that is related to an authorized investigation to protect against international terrorism or clandestine intelligence activities."
More
here.
U.S. National Bill of Rights Day

Today, we take solemn notice National Bill of Rights Day - marking the 217th anniversary of the ratification of the first ten amendments to the Constitution. In 1941, President Franklin D. Roosevelt declared December 15 to be Bill of Rights Day, commemorating the 150th anniversary of the ratification of the Bill of Rights.
After eight years of George W. Bush doctrine, we should all really have hope that President-Elect Barack Obama's administration will restore some of the despicable infringements made by the Bush administration on the rights guaranteed to us by our forefathers.
As Abdus-Sattar Ghazali wrote on OpEdNews.com last year:
The Bill of Rights limits the power of the government and protects the rights of the people. It was so important that several of the original 13 states would not ratify the Constitution without it.
Nearly everything that makes an American proud to be one comes from the Bill of Rights.
Freedoms to speak, print, read, assemble, pray, petition the government, keep and bear arms. Protection from unreasonable arrests and searches, excessive bail, double jeopardy, coerced confessions, cruel and unusual punishment. Rights to due process, jury trials, counsel, and to present defense witnesses. These are the freedoms and rights that define America.
The Bill of Rights was meant to ensure basic rights during times of war and times of peace, regardless of who is in power. In order to ensure its future, we must keep using the First Amendment and speaking out when our rights and the rights of non-citizens are threatened.
Seven years of President Bush have probably done more harm to the freedoms in the Bill of Rights than this country has seen in thirty, maybe even fifty years. Nearly everything the government does today is unconstitutional under the system they instituted. Under the Bill of Rights, governmental powers were expressly limited; individual liberties were not. Now it seems it is the other way around.
More detailed background on Bush Administration's abuses to the fundamental rights & liberties guaranteed to U.S. citizens by the Bill of Rights can be found
here.
- ferg
Microsoft Sees 'Huge Increase' in IE Attacks
Gregg Keizer writes on ComputerWorld:
Microsoft warned Saturday of a "huge increase" in attacks exploiting a critical unpatched vulnerability in Internet Explorer (IE), and said some originated from hacked pornography sites.
Other researchers confirmed that attacks were increasingly coming from compromised Web sites.
Microsoft noted the upswing in attacks on the company's Malware Protection Center blog late Saturday. "The trend for now is going upwards," said researchers Ziv Mador and Tareq Saadecom on the blog. "We saw a huge increase in the number of reports today compared to yesterday."
More
here.
14 December 2008: International Monkey Day
























