For Sale: West's Deadly Nuclear Secrets

Via The Sunday Times Online.
A whistleblower has made a series of extraordinary claims about how corrupt government officials allowed Pakistan and other states to steal nuclear weapons secrets.
Sibel Edmonds, a 37-year-old former Turkish language translator for the FBI, listened into hundreds of sensitive intercepted conversations while based at the agency’s Washington field office.
She approached The Sunday Times last month after reading about an Al-Qaeda terrorist who had revealed his role in training some of the 9/11 hijackers while he was in Turkey.
Edmonds described how foreign intelligence agents had enlisted the support of US officials to acquire a network of moles in sensitive military and nuclear institutions.
More
here.
Taiwan High Speed Rail Website Hit By DDoS Attack
Shelley Shan writes in The Taipei Times:
Travelers planning to go home during the Lunar New Year holidays had trouble booking a high speed rail ticket online yesterday morning, as hackers tried to prevent buyers from logging onto the system.
The online ticketing system of the Taiwan High Speed Rail Co. (THSRC) was activated at 12am yesterday for those scheduled to travel between Feb. 1 and Feb. 12.
The Lunar New Year holidays begin on Feb. 6, or Lunar New Year's Eve, and ends on Feb. 11.
However, interested buyers said they could not access the rail company's Web site.
THSRC spokesperson Ted Chia (賈先德) said yesterday that the firm's technical specialists later identified the problem as hackers attempting to block other requests, as some of the requests were sent simultaneously from the same Internet Protocol (IP) addresses.
More
here.
Hat-tip: FIRST.org Global Security News
Huawei Sets Its Sights on U.S. Market

Ariana Eunjung Cha writes in The Washington Post:
From a fortress-like corporate campus in this southern city [Shenzhen, China], retired army officer Ren Zhengfei is building one of China's most successful experiments in capitalism. A mammoth operation with 70,000 employees and strong backing from the state, Huawei Technologies brags that its goal is to dominate telecommunications equipment markets all over the world.
Its current focus: America.
Fueling [U.S.] lawmakers' unease about the Huawei deal is that no one knows exactly who owns it. Technically, Huawei is a private venture, not state-owned. But the company won't reveal information about its shareholders except to say it's "100 percent employee-owned," with its chief executive owning 1 percent.
Research organization Rand Corp. said that Huawei has "deep ties" with the Chinese military. It is not only a customer of Huawei's, Rand said in an analysis prepared for the U.S. government, but also was a "political patron and research and development partner."
More
here.
U.S. Toll in Iraq

Via The Boston Globe (AP).
As of Saturday, Jan. 5, 2008, at least 3,909 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,178 died as a result of hostile action, according to the military's numbers.
The AP count is five higher than the Defense Department's tally, last updated Friday at 10 a.m. EST.
More
here.
And as always,
the
Iraq Coalition Casualty Count keeps the grim watch on their website
here.
FAA: Boeing's New 787 May Be Vulnerable to Hacker Attack

Kim Zetter writes on Wired:
Boeing's new 787 Dreamliner passenger jet may have a serious security vulnerability in its onboard computer networks that could allow passengers to access the plane's control systems, according to the U.S. Federal Aviation Administration.
The computer network in the Dreamliner's passenger compartment, designed to give passengers in-flight internet access, is connected to the plane's control, navigation and communication systems, an FAA report reveals.
The revelation is causing concern in security circles because the physical connection of the networks makes the plane's control systems vulnerable to hackers. A more secure design would physically separate the two computer networks. Boeing said it's aware of the issue and has designed a solution it will test shortly.
More
here.
Class Action Suit Alleges Sears Privacy Failures
Brian Krebs writes on Security Fix:
Class-action lawyers are circling around retailer Sears, Roebuck & Co., just days after privacy activists revealed that the company's Web site exposed the details of customer purchases going back more than a decade.
In a complaint filed Friday in Cook County, Illinois -- where Sears is headquartered -- the plaintiffs allege that the lack of privacy protections at Sears's managemyhome.com site violated its own privacy promises to consumers, and in so doing ran afoul of the Illinois Consumer Fraud Act, which prohibits "unfair and deceptive practices."
The complaint seeks class-action status, and more than $5 million in damages, including attorneys' fees.
More
here.
'Ragtag' Russian Army: The New Face of DDoS Attacks
Dan Goodin writes on Channel Register:
In late April, a Russian-speaking blogger upset with recent events in Estonia posted a series of dispatches calling on like-minded people to attack government servers in that country.
"They're really fascists," the user, who went by the name of VolchenoK, wrote of Estonian government officials, according to this translation. "Let us help those who are there and really fought for the memory of our grandfather and grandmother. Yet they are fighting against fascism!"
More
here.
Hackers Deface Canadian Police Website
Charlene Close writes on 680News.com:
The Durham Regional Police service website was taken off-line late Thursday night after a hacker attacked the homepage.
Technicians spent much of Friday trying to correct the problem and trace the source.
Around 10 p.m. Thursday, someone broke into the website administration site and posted a message that read "defaced by King Hack Team."
Police said the culprit was not able to access any sensitive information.
More
here.
Hat-tip: FIRST.org Global Security News
U.S. Toll in Iraq, Afghanistan

Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Friday, Jan. 4, 2008, at least 3,908 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,178 died as a result of hostile action, according to the military's numbers.
The AP count is four higher than the Defense Department's tally, last updated Friday at 10 a.m. EST.
As of Friday, Jan. 4, 2008, at least 406 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures Dec. 29, 2007, at 10 a.m. EST.
Of those, the military reports 274 were killed by hostile action.
More
here and
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
There's an ATM Crime Wave? Who Knew

Bob Sullivan writes on The Red Tape Chronicles:
Citibank is using the rather blunt instrument of lowering some customers’ daily ATM cash withdrawal limits to fight a recent spate of cash machine fraud. The company said Thursday that the change impacts "a small population of customers" in New York City, but would not provide additional details.
It's not clear how much daily withdrawal limits were lowered, but the New York Daily News spoke with one consumer who said her limit had been cut in half.
"Though we can't provide details of ongoing security investigations, we are working closely with law enforcement on this matter," Citibank said in a statement to msnbc.com. "We continue to monitor our customer accounts for suspicious transactions and encourage customers who notice suspicious activity to call our customer service unit at the number on the back of their ATM cards."
More
here.
Lloyds TSB Tells Customers They Have Been Hacked
Karl Flinders writes on ComputerWeekly.com:
Lloyds TSB has sent a letter to customers warning them that their computers may have been exposed to a Trojan horse, but a customer has complained of a lack of detail from the bank.
The bank's Fraud Response Team sent letters to some customers in December after it received a tip-off from payments association APACs, acting on intelligence from a law enforcement agency.
"Lloyds TSB has been recently advised that your computer may have been infected with a virus. This virus is specifically designed to steal personal information including credit card and your internet login details," warned the letter. "This virus can be difficult to detect and you may have downloaded this unknowingly. It can compromise your use of the internet banking service on your PC including your Lloyds TSB passwords and memorable information."
The letter left one IT director, who banks with Lloyds TSB, angry. He contacted the anti-fraud team but did not receive answers to his questions. He was told that his personal details had been available on a website, which the bank had now closed down, and was offered a security service but was not given details of the Trojan on his PC.
More
here.
Hat-tip: Pogo Was Right
Network Overload: Happy New Year, Your Text Message Has Failed
An AP newswire article by Deepti Hajela, via ABC News, reports that:
Millions and millions of messages did get through New Year's Eve, and a minor delay in a holiday wish is hardly the end of the world. But there have been multiple occasions in recent years when getting in touch with loved ones was more vital the Sept. 11 attacks, the 2003 blackout, Hurricane Katrina.
"What happens where there is an emergency?" asked Scott Midkiff, professor of electrical and computer engineering at Virginia Tech. "This has been a big problem with the voice cellular system. It will probably become more of a problem with text messaging."
More
here.
Chinese Hackers Force Pennsylvania To Shut Down State Website
Via NBC10.com.
Pennsylvania's state government Web site was almost completely shut down Friday after it was infiltrated by hackers from China, but officials said they found no evidence of damage.
Four departments had security problems with their Web pages, leading to a decision to take nearly all of the state's Internet site down on Friday morning.
By late afternoon, nearly all of the state's site had been put back online.
The problems arose at pages of the departments of Labor and Industry, Education, and Military and Veterans Affairs, as well as the Pennsylvania Lottery's page.
Investigators tracked the source to a domain registered in China, she said.
More
here.
U.S. Toll in Iraq

Via The Boston Globe (AP).
As of Thursday, Jan. 3, 2008, at least 3,907 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,178 died as a result of hostile action, according to the military's numbers.
The AP count is three higher than the Defense Department's tally, last updated Thursday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
JavaScript: A Tool, A Weapon
I am somewhat at a loss for words, having sung this same tune for almost 20 years.
Back when JavaScript was first introduced, many of us in the network security realm immediately realized how devastating it could be as an attack platform -- and here we are.
Malicious embedded JavaScript has become the flavor du Jour for web criminals.
Yet, criminals have latched on to it as a easy way to compromise users -- "low hanging fruit".
The corollary could be drawn to any number of technologies that provide functionality, but yet in the wrong hands, can wreak havoc, and be used for ill intentions.
Unfortunately, this is exactly what is happening today in the criminal underground with malicious JavaScript, and in a major, major way.
And again, unfortunately, there are more tools to develop malicious JavaScript than there are to detect them.
In my opinion, we are at a turning point -- how do we move forward?
It is my belief that a major effort needs to be undertaken to detect malicious JavaScript scripts, functional sandboxing methodologies, and ways to bring "NoScript" -style functionality to the masses.
I challenge Microsoft to step up the the plate here (and to include ActiveX).
This is going to be a major, major challenge for all of us in the coming year(s).
- ferg
11 Indicted In International Illegal Spamming And Stock Fraud Scheme
Via USDoJ.gov.
A federal grand jury indictment was unsealed today in Detroit charging 11 persons, including Alan M. Ralsky, his son-in-law Scott K. Bradley, and Judy M. Devenow, of Michigan, and eight others, including a dual national of Canada and Hong Kong and individuals from Russia, California, and Arizona, in a wide-ranging international fraud scheme involving the illegal use of bulk commercial e-mailing, or "spamming."
Charged in the 41-count indictment are:
- Alan M. Ralsky, 52, of West Bloomfield, Michigan
- Scott K. Bradley, 46, of West Bloomfield, Michigan
- Judy M. Devenow, 55, of Lansing, Michigan
- John S. Bown, 47, of Poway, California
- William C. Neil, 45, of Fresno, California
- Anki K. Neil, 36, of Fresno, California
- James E. Bragg, 39, of Queen Creek, Arizona
- James E. Fite, 34, of Whittier, California
- Peter Severa, age unknown, of Russia
- How Wai John Hui, 49, of Vancouver, Canada and Hong Kong
- Francis A. Tribble, of Los Angeles, California
Appearing in court for arraignment today were defendants Scott Bradley and Judy Devenow, who were arrested today. Defendant How Wai John Hui was arrested in the Eastern District of New York on Jan. 2, 2008. The remaining defendants are being sought.
Assistant Attorney General Alice S. Fisher of the Criminal Division said, "The flood of illegal spam continues to wreak havoc on the online marketplace and has become a global criminal enterprise. It clogs consumers' email boxes with scams and unwanted messages and imposes significant costs on our society. This indictment reflects the commitment of the Department of Justice to prosecuting these spamming organizations wherever they may operate. I would like to thank the many prosecutors and agents for their extraordinary efforts leading up to the indictment."
More
here.
A 2007 Year-End Growth of More Than 200% for The Storm Botnet

Thorsten Holz writes on the Honeyblog:
The picture illustrates the success rate of the botnet: The x-axis shows the date, starting a few days before Christmas and ending today. The y-axis represents the number of infected machines within Stormnet, the "encrypted" part of the botnet in which the actual communication is XORed with a 40 byte key.
As you can see, the first days before Christmas the size of the botnet was around 5-14 thousand infected machines. However, just around Christmas the size grows again due to successful infections and new victims which fell for the social engineering mails. For now, the botnet has peaked at about 40 thousand infected machines being online at a time.
Moreover, the picture also shows a clear diurnal pattern: many infected host are located in the US and these machines are turned off during the night, leading to fewer online machines within the botnet.
More
here.
Image source: Moritz Steiner, Honeyblog.org
Having Technical Difficulties: A Brief Treatise on Usability

I would consider this article a very good treatise -- and fatally humorous -- for software developers, designers, and usability "experts" on how to make their wares and products more usable by ordinary, non-technical consumers.
This piece was written by Thomas Sowell, and originally appeared in The Bismarck Tribune (reproduced here via RedOrbit.com) and sums up the situation rather well, but goes to illustrate the frustration a bit further in these paragraphs:
There must be some blind spot that computer engineers have which prevents them from seeing that (1) most people are not computer engineers, (2) there is no point making simple things complicated, and (3) not everyone is looking for a zillion features to have to wade through to do simple things.
Let's start at square one. What is the first thing you want to do with any computerized product? Turn it on.
Why should that be a problem when people were turning things off and on for generations before there were personal computers?
Yet computer engineers seem determined to avoid the very words "off" and "on."
Read the entire article
here.
Go ahead -- it's worth a few minutes of your time. While it is a syndicated newspaper column meant to be humorous, it really does strike a chord that needs to be struck occasionally -- especially in the world of technology development.
There are thousands of
software usability treatises out there, yet the lesson of
Occam's Razor seems lost to a majority of designers.
*sigh*
Enjoy!
- fergImage source: Savage Chickens
Robotic Industries Association Website Hacked - Credit Card Details Accessed
Via Pogo Was Right.
Robotics Industries Association reported that a hacker accessed their administration site for Robotics Online on or about December 10th, gaining access to individual orders that contained credit card information. Seven residents of NH were affected, but national totals were not indicated.
Following the intrusion, the company deleted all credit card information from their site, and temporarily ceased accepting credit card orders.
Robotics Industries Association Notification to New Hampshire DoJ
here [.pdf].
Computer Forensics Faces Private Eye Competition

Deb Radcliff writes on Baseline:
The Internet is boundless and cybercrime scenes stretch from personal desktops across the fiber networks that circle the globe. Digital forensic investigators like Harold Phipps, vice president of industry relations at Norcross Group in Norcross, Ga., routinely slip across conventional geographic jurisdictions in pursuit of digital evidence and wrongdoers.
Lawmakers across the Savannah River in Columbia, S.C., have different ideas, however. Under pending legislation in South Carolina, digital forensic evidence gathered for use in a court in that state must be collected by a person with a PI license or through a PI licensed agency.
If the law passes, the highly specialized task of probing deep into computer hard drives, network and server logs for telltale signs of hacking and data theft would land in the hands of the same people who advertise in the Yellow Pages for surveillance on cheating spouses, workers' compensation fraud and missing persons. Otherwise, digital evidence collected by unlicensed practitioners could be excluded from criminal and civil court cases. Worse yet, those caught practicing without a license could face criminal prosecution.
More
here.
Germans Protest Data Mining Law
Via UPI.
Protests coincided with the filing of a lawsuit supported by thousands in Germany in opposition to a new law allowing the retention of telecommunication data.
Protesters rallied in several German cities to support a lawsuit backed by more than 30,000 Germans filed to fight legislation that permits the storing of Internet data and telephone records for up to six months as part of wider counter-terrorism efforts, Deutsche Welle said Wednesday.
More
here.
The New U.S. Air Force Cyber General - UPDATE
Kevin Coleman writes on Defense Tech:
During a media conference on November 2, 2007, Secretary of the Air Force Michael W. Wynne said the 8th Air Force would become the new Air Force Cyber Command. Now this statement has become reality.
A three-star general, Lt. Gen. Robert Elder Jr. is the commander and will lead the Air Force's (AFCYBER) Cyber Command. AFCYBER will have over 20,000 personnel, and the Air Force is recruiting officers and airmen from all over for careers in Cyber War.
Thousands of existing air force electronic warfare specialists will be assigned, or offered, jobs in AFCYBER. This will include units operating in the full spectrum of electronics and the electromagnetic spectrum to store, modify, and exchange data via networked systems and associated physical infrastructures.
More
here.
UPDATE: 13:39 PST: See also
"The Dogs of Web War" in The Air Force Magazine Online.
-ferg
Myanmar: 'No Satellite TV For You!'
A Reuters newswire article by Aung Hla Tun, via The Boston Globe, reports that:
Without warning, Myanmar's military junta has ordered a massive 166-fold rise in the annual satellite television levy in an apparent attempt to stop people watching dissident and international news broadcasts.
With no word in state media of any license fee increases, the first satellite dish owners knew of the hike was when they went to pay the 6,000 kyat levy, only to be told it was now 1 million kyat ($780), three times the average citizen's yearly income.
An official at Myanma Post and Telecom confirmed the increase on Wednesday, but was at a loss to explain it.
"It's not our decision," the official, who asked not to be named, told Reuters. "We were just ordered by the higher authorities. Even I was shocked when I heard about it."
More
here.
U.S. Toll in Iraq

Via The Boston Globe (AP).
As of Tuesday, Jan. 1, 2007, at least 3,904 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,178 died as a result of hostile action, according to the military's numbers.
The AP count is three higher than the Defense Department's tally, last updated Tuesday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
South Korean Military Issues Warning on Chinese Hackers

Jung Sung-ki writes in The Korean Times:
The South Korean military has issued a warning that computer systems of soldiers and defense institutes have become the victims of presumed Chinese hacking activities, a military source said Tuesday.
The source said hackers, believed to be Chinese nationals, penetrated computers of soldiers by sending e-mail involving hacking programs falsely titled "the situation on North Korea's arms power."
"We are now investigating several cyber hacking cases believed to be conducted by Chinese nationals based on evidence that the hackers stole information stored in soldiers' computers," the source said, asking not to be named.
The hackers appeared to have penetrated Web sites of military units and retired soldiers to steal e-mail addresses of individuals registered to the sites, he said.
More
here.
Saudis Confirm Detention of Blogger
Katherine Zoepf writes in The New York Times:
An outspoken Saudi blogger is being held for “purposes of interrogation,” the Saudi Interior Ministry confirmed Tuesday.
Gen. Mansour al-Turki, an Interior Ministry spokesman reached by telephone, said that the blogger, Fouah al-Farhan, was “being questioned about specific violations of nonsecurity laws.” Mr. Farhan’s blog, which discusses social issues, had become one of the most widely read in Saudi Arabia.
Mr. Farhan, 32, of Jidda, was arrested Dec. 10 at his office, local news sources reported. Two weeks before his arrest, he wrote a letter to friends warning them that it was imminent.
More
here.
Google Artificially Promotes Recent Web Pages

As you can see from recent events, malware authors and other criminals have already found out that they can exploit this "feature".
As Ionut Alex Chitu writes on the Google Operating System Blog:
Google paid a big price when it started to index pages faster and show them in the search results minutes after they're published. The problem is that you can't rank a page that has just been created because it has no backlinks so Google artificially inflates the rankings of the recently-created pages based on historical data and the few backlinks that are detected.
In some cases, if Google sees a lot of searches for a query that wasn't popular before, it assumes something has happened recently and shows more recent results.
More
here.
As the first comment on this Google Operation System Blog post says, it just "...goes to show the biggest threat to Google Inc in 2008 remains, well, Google Inc."
- ferg
Israeli Arab Hacker Arrested for 'Internet Terror'
Via Red Orbit News.
[Text of report in English by Israeli newspaper The Jerusalem Post here.]
A 17-year-old from the Arab village of Kfar Karah, in Wadi Ara, was arrested overnight Monday on suspicion of hacking into and sabotaging thousands of Web sites, police said. The suspect allegedly wrecked sites belonging to the Likud Party, Maccabi Tel Aviv, shopping sites and sites used as servers by various other companies.
The Northern District Police Fraud Squad is set to request a five-day remand extension for the suspected hacker.
Police described the alleged offences as "Internet terror", accusing the teen of working with several associates from Turkey and Saudi Arabia to specifically ruin Israeli websites. As yet, it is unclear if government sites were affected.
More
here.
Hat-tip: FIRST.org Global Security News
My Personal 2008 Calendar

I've been waiting for 7 years to hang this calendar.
Tonight is the night.
And I'll be counting the days.
Let's hope this will really be a Happy New Year.
- ferg
Happy Hogmanay!
 Hogmanay Fireworks over Edinburgh Castle
Hogmanay Fireworks over Edinburgh CastleGiven my Scottish ancestry, we say
Happy Hogmanay!
Have a Happy and Prosperous New Year.
- ferg
2008: One More Year
Click for larger image.
Website at the End of the Universe's Free Downloadable 2008 Calendar

Via The Website at The End of The Universe.
Once again The Website at the End of the Universe is offering its annual science fiction calendar to you as a free PDF download and once again helpless females in metal bikinis continue to be threatened by bug-eyed aliens who just can't get enough of Earth women.
Each month of the 2008 calendar features a different pulp cover with a different space babe in peril as well as a list of famous science fiction birthdays. Download your copy for free.
Get it
here.
Image source: The Website at The End of The Universe
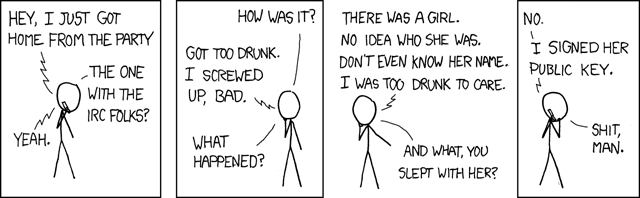
xkcd: Drunken Key Signing
Click for larger image.
We
love xkcd.
Quote of the Day: Clark Kent Ervin
"...I strongly question whether five days is enough to train anybody in the intrinsically difficult art-science of behavior detection. And with all due respect to T.S.A. screeners, they are not Mossad agents. Study after study has shown them to be incapable of spotting artfully concealed weapons, and sometimes, even, inartfully concealed ones."
"So, what makes us think that screeners who can’t tell a bomb component from a curling iron can all of sudden tell whether the guy with the big frown on his face is frowning because he’s determined to kill infidels today or because somebody just dropped a suitcase on his foot?"
- Clark Kent Ervin, commenting on the New York Times' Jet Lagged Blog, regarding the TSA SPOT (Screening Passengers by Observation Techniques) training program.
More background on SPOT here.
U.S. Toll in Iraq

Via The Boston Globe (AP).
As of Sunday, Dec. 30, 2007, at least 3,902 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes eight military civilians. At least 3,175 died as a result of hostile action, according to the military's numbers.
The AP count is four higher than the Defense Department's tally, last updated Friday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casualty Count website
here.
Four Horsemen Alert: Australia Moves to Mandatory ISP Content Filtering - Users Must 'Opt Out'
Lachlan Heywood writes on Australian IT:
Australians will be forced to contact their internet service provider to avoid having their access to the web restricted.
The restrictions are planned by the Federal Government to give greater protection to children from online pornography and "violent" websites.
Under the plan, all internet service providers will be required to provide a "clean" feed to households and schools, free of pornography and other inappropriate material.
Any internet users who want to "opt out" of the clean feed will have to contact their ISP.
Online civil libertarians yesterday warned the freedom of the internet was at stake, while internet providers are concerned the new measures could slow the internet in Australia down to a crawl.
But Communications Minister Stephen Conroy said everything possible had to be done to shield children from violent and pornographic online material.
More
here.
Note: Background on the
"Four Horsemen of the Information Apocalypse" can be found
here.
I'm also curious as to whether or not "opting out" of this nonsense would land you on some government watch list?
-ferg
Bill Maher's Picks for 2007's 'Dickheads of The Year'

Say no more.
Enjoy!
-ferg
U.S. Among The World's Worst for Protecting Citizen's Privacy
Via Privacy International.
Each year since 1997, the US-based Electronic Privacy Information Center and the UK-based Privacy International have undertaken what has now become the most comprehensive survey of global privacy ever published. The Privacy & Human Rights Report surveys developments in 70 countries, assessing the state of surveillance and privacy protection.
The most recent report published in 2007, is probably the most comprehensive single volume report published in the human rights field. The report runs over 1,100 pages and includes 6,000 footnotes. More than 200 experts from around the world have provided materials and commentary. The participants range from eminent privacy scholars to high-level officials charged with safeguarding constitutional freedoms in their countries.
Academics, human rights advocates, journalists and researchers provided reports, insight, documents and advice. In 2006 Privacy International took the decision to use this annual report as the basis for a ranking assessment of the state of privacy in all EU countries together with eleven non-EU benchmark countries. Funding for the project was provided by the Open Society Institute (OSI) and the Joseph Rowntree Reform Trust.
The new 2007 global rankings extend the survey to 47 countries (from the original 37) and, for the first time, provide an opportunity to assess trends.
The intention behind this project is two-fold. First, we hope to recognize countries in which privacy protection and respect for privacy is nurtured. This is done in the hope that others can learn from their example. Second we intend to identify countries in which governments and privacy regulators have failed to create a healthy privacy environment. The aim is not to humiliate the worst ranking nations, but to demonstrate that it is possible to maintain a healthy respect for privacy within a secure and fully functional democracy.
More
here.
Reports of Data Breaches Reached New Heights in 2007
An AP newswire article by Mark Jewell, via USA Today, reports that:
The loss or theft of personal data such as credit card and Social Security numbers soared to unprecedented levels in 2007, and the trend isn't expected to turn around anytime soon as hackers stay a step ahead of security and laptops disappear with sensitive information.
And while companies, government agencies, schools and other institutions are spending more to protect ever-increasing volumes of data with more sophisticated firewalls and encryption, the investment often is too little too late.
"More of them are experiencing data breaches, and they're responding to them in a reactive way, rather than proactively looking at the company's security and seeing where the holes might be," said Linda Foley, who founded the San Diego-based Identity Theft Resource Center after becoming an identity theft victim herself.
Foley's group lists more than 79 million records reported compromised in the United States through Dec. 18. That's a nearly fourfold increase from the nearly 20 million records reported in all of 2006.
Another group, Attrition.org, estimates more than 162 million records compromised through Dec. 21 — both in the U.S. and overseas, unlike the other group's U.S.-only list. Attrition reported 49 million last year.
More
here.