Chinese Red Cross Website Hacked to Steal Earthquake Relief Donations
Via The Dark Visitor.
Verified by the Ministry of Public Security [in China], a section of the official Red Cross website has been illegally hacked. According to the report, criminal elements gained access to the section of the website that held the special accounts for earthquake disaster relief donations.
An individual named Li Bujiu, had opened four fraudulent bank accounts to steal the funding.
The Ningbo Bank released a statement warning all citizens to be verify account numbers when making donations. The bank suggested using CCTV, TV, and newspapers as references to verify the accounts.
More
here.
IRS: Some Stimulus Checks Sent to Wrong Accounts
Carol Polsky writes on Newsday.com:
Through the wonders of modern technology, some of those federal economic stimulus checks are being deposited directly into recipients' bank accounts.
But some are not - and are instead winding up in the bank accounts of complete strangers.
"We do know of instances of problems; we've heard of situations where stimulus checks have gone to the wrong people's bank accounts," conceded Kevin McKeon, the Internal Revenue Service spokesman for the New York region. "We're getting a lot of calls to the toll-free number."
One local taxpayer, who asked not to be identified, reported that he had discovered an unexpected deposit of $1,800 in his bank account. He said a review of his bank records revealed that it was a deposit from the IRS bearing another taxpayer's Social Security number. He said he contacted the IRS and was told by an agent that the deposit was one of 15,000 misrouted checks sent out incorrectly as a result of a computer programming glitch.
More
here.
Hat-tip: The Consumerist
Spain Arrests 'Prolific' Hackers
Via The BBC.
Spanish police have arrested five hackers they describe as being among the most active on the internet.
The hackers, who include two 16-year-olds, are accused of disrupting government websites in the United States, Asia and Latin America.
Police say they co-ordinated attacks over the internet and hacked into 21,000 web pages over two years.
The inquiry began in March after a Spanish political party's site was disabled after the Spanish election.
More
here and
here (via
USA Today).
Conde Nast Buys Ars Technica
Stephen Shankland writes on the C|Net News Blog:
Ars Technica, a decade-old independent tech news and analysis site, is becoming a part of Conde Nast's Wired Digital group.
The acquisition will be announced Monday, sources familiar with the acquisition said, confirming a report Friday in TechCrunch. The price tag was near $25 million, TechCrunch said.
More
here.
Pellicano Guilty of Wiretapping
David M. Halbfinger writes in The New York Times:
Anthony Pellicano, the ripped-from-a-pulp-novel private eye who made himself an indispensable fixer for Hollywood stars and moguls, was found guilty in federal court Thursday of racketeering, wiretapping and other charges.
The jury of eight men and four women deliberated nine days before finding Mr. Pellicano, 64, guilty of 76 of the 77 counts against him, mostly in connection with his extensive wiretapping operation, which he used to dig up dirt on business enemies and former spouses of his powerful clients.
The jury also convicted his four co-defendants, among them a former police detective and a retired phone company technician, on a variety of charges.
The verdict, which took Judge Dale S. Fischer a full hour to read, was a resounding victory for the government after six years of investigation.
More
here.
EFF: Signs Are NBC Triggered Block of 'American Gladiator'
Greg Sandoval writes on the C|Net News Blog:
The Electronic Frontier Foundation has begun investigating why Microsoft Vista Media Centers were blocked from recording two NBC Universal shows Monday night.
The group, which advocates for Internet users, said indications are that NBC sent a "broadcast flag" that triggered the block. But Danny O'Brien, EFF's international outreach coordinator, said the block couldn't have occurred unless hardware and software makers honored the network's request to prevent users from recording the shows. It appears Microsoft may have obeyed NBC Universal's broadcast flag.
NBC Universal and Microsoft said they need time to look into the matter.
More
here.
PayPal XSS Vulnerability Undermines EV SSL Security
Via Netcraft.
A security researcher in Finland has discovered a cross-site scripting vulnerability on paypal.com that would allow hackers to carry out highly plausible attacks, adding their own content to the site and stealing credentials from users.
The vulnerability is made worse by the fact that the affected page uses an Extended Validation SSL certificate, which causes the browser's address bar to turn green, assuring visitors that the site – and its content – belongs to PayPal. Two years ago, a similar vulnerability was discovered on a different page of the PayPal site, which also used an SSL certificate.
More
here.
Australia: Hacker Shuts Down Government Computers
Phoebe Stewart writes on News.com.au:
An expert hacker allegedly shut down the Northern Territory Government computer system and deleted thousands of employees' identities, a Darwin court heard yesterday.
And the court heard the Government could still be at risk of another cyber attack.
David Anthony McIntosh, 27, allegedly hacked in and shut down several NT Government databases on May 5, including servers for the Health Department, Royal Darwin Hospital, Berrimah Prison and Supreme Court using his laptop at a Palmerston home.
Prosecutor Sergeant Erica Sims told the Darwin Magistrates Court yesterday the Sydney IT expert allegedly deleted the independent user accounts of 10,475 NT public servants.
She said many workers had to be "stood down", and experts had been working "24 hours, seven days a week" to repair the damage.
But Sgt Sims said it could take months to fix, with the repair cost estimated to run into the "hundreds of thousands of dollars".
More
here.
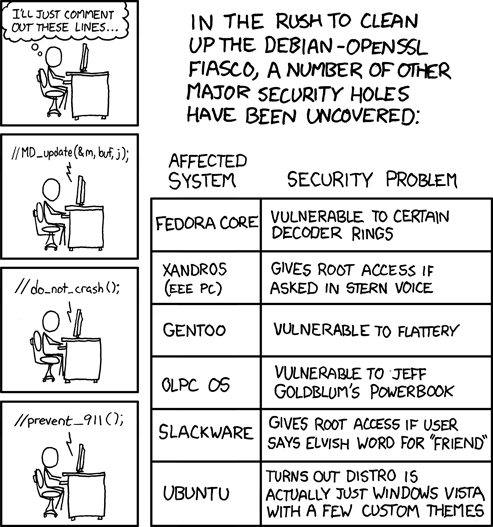
xkcd: Cleaning House, Security Style
Click for larger image.
We
love xkcd.
- ferg
Unfortunate Toon of The Day: Why We Must Change

We love Mr. Fish.
Via Truthdig.com.
- ferg
UK: SOCA Cyber Crimefighting Successes Revealed?
Nick Heath writes on Silicon.com:
The police body tasked with fighting e-crime in the UK has revealed some of its cyber crimefighting successes - but e-crime still appears a low priority.
The Serious Organised Crime Agency's (SOCA) 2007 to 2008 report details work by the agency over the past year.
But whereas the report details scores of successful operations to stop drug trafficking there is little other mention of the work of SOCA's e-crime unit and it does not specify how many of its 2,033 arrests were related to cyber crime.
More
here.
UK: Government Orders Data Retention by ISPs
Via OUT-LAW. com.
Phone and internet companies will soon be forced to keep logs of internet usage to be made available to the police under a new law announced by Prime Minister Gordon Brown this week.
The law, the Communications Data Bill, will implement the remainder of the European Union's Data Retention Directive.
Last October the Government enacted regulations which said that telcos must keep records of phone calls to and from land lines and mobile telephones. That requirement will be extended to records of customers' internet usage, email usage and voice over internet protocol (VoIP) records.
The Bill is likely to follow the lead of last year's Data Retention (EC Directive) Regulations in ordering providers to keep the data for 12 months.
More
here.
SQL Injection Attack In 'Third Wave'
Jon Brodkin writes on NetworkWorld:
A SQL injection attack that has affected at least a half-million Web sites has entered a "third wave" that's more resistant than previous versions to traditional security measures, according to IBM security researchers.
"I've been tracking SQL injections for the last five or six years. This is some of the most intricate obfuscation I've ever seen," says David Dewey, research manager for the X-Force technology at IBM's Internet Security Systems division.
A SQL injection is an attack against a database-driven Web site in which the hacker executes unauthorized SQL commands by taking advantage of insecure code on systems connected to the Internet.
When Dewey talks about obfuscation, he's referring to hackers hiding attacks behind seemingly valid functionality. The attacks evolve as hackers change the SQL commands used to accomplish their goals, but the result is the same.
More
here.
Note: Nothing against Mr. Dewey -- and in fact, he is right -- but I don't need IBM to tell me this -- we've been following these attacks and documenting them over on the
Trend Micro Blog.
-ferg
Tools Already Circulating to Crack Debian, Ubuntu SSH/SSL Keys
Gregg Keizer writes on ComputerWorld:
A recently disclosed vulnerability in widely used Linux distributions can be exploited by attackers to guess cryptographic keys, possibly leading to the forgery of digital signatures and theft of confidential information, a noted security researcher said today.
HD Moore, best known as the exploit researcher who created the Metasploit penetration testing framework, called the vulnerability in Debian and Ubuntu systems "ugly" and said it will be a big job for administrators to find every flawed key, then reissue them.
The bug, noted Tuesday by the Debian Project, is in the random number generator used to produce a variety of digital keys, including SSH (Secure Shell) keys and SSL (Secure Socket Layer) certificates. The latter are widely used to secure traffic between users and secure sites on the Internet.
According to Moore, the bug makes it relatively easy to "guess" keys. In a blog post yesterday, Moore claimed he was able to generate 1024- and 2048-bit keys in about two hours.
More
here.
Off Beat: Yeah, It's a Little Warm...
 Click for larger image.
Click for larger image.It's quite hot here today in Silicon Valley. Damned hot.
In fact, it's still 93F degrees at 18:52 PDT.
More of the same tomorrow. Yow.
- ferg
DNS Trouble Knocks NSA Off Internet
Robert McMillan writes on InfoWorld.com:
A server problem at the U.S. National Security Agency has knocked the secretive intelligence agency off the Internet.
The nsa.gov Web site was unresponsive at 7 a.m. Pacific time Thursday and continued to be unavailable throughout the morning for Internet users.
The problem was resolved at around 11 a.m. Pacific time, according to Web site measurement company Netcraft.
The Web site was unreachable because of a problem with the NSA's DNS servers, said Danny McPherson, chief research officer with Arbor Networks. DNS servers are used to translate things like the Web addresses typed into machine-readable Internet Protocol addresses that computers use to find each other on the Internet.
The agency's two authoritative DNS servers were unreachable Thursday morning, McPherson said.
More
here.
Report: Government's Cyber Security Plan Is Riddled With New Spying Programs
Ryan Singel writes on Threat Level:
Major elements of the Bush administration's proposed $17 billion "cyber security" initiative have little to do with protecting government networks, and a lot to do with spying, according to a budget report released by the Senate Armed Services Committee this week.
The so-called National Cyber Security Initiative is also wrapped in unnecessary secrecy, and would spend billions on unproven, embryonic technology, and possibly illegal or ill-advised projects, according to the analysis -- which is part of a broad look at the proposed 2009 defense budget.
"[S]ome of the projects support foreign intelligence collection and analysis generally rather than the cyber security mission particularly," the report concludes. "That is not to say that the proposed projects are not worthwhile, but rather that what will be achieved for the more than $17 billion planned by the administration to secure the government's networks is less than what might be expected."
More
here.
Government Secrecy and the Mysterious Cyber Initative
Brian Krebs writes on Security Fix:
The secrecy surrounding the Bush administration's updated National Cyber Security Initiative -- designed to improve the government's digital defenses and put forth an offensive information warfare doctrine -- is endangering the deterrent value of the project and appears to be aimed chiefly at supporting spying operations abroad, a key U.S. Senate committee concludes in a new report.
The Senate Armed Services Committee said a major thrust of the initiative was to inform our adversaries as to the range of potential consequences of a cyber attack on U.S. strategic or national assets. But so far only three of the 18 goals spelled out in the cyber initiative have been discussed publicly; the rest remain classified.
More
here.
Major International Cyber Terrorism Meeting Scheduled
William Jackson writes on GCN.com:
A meeting next week in Malaysia being billed as the largest minister-level summit ever held on cyberterrorism will kick off an international partnership of more than 30 countries to study and respond to high-level cybersecurity threats.
The International Multilateral Partnership Against Cyber-Terrorism (IMPACT) is the brainchild of the prime minister of Malaysia, who saw the need for such an organization during the World Congress of Information Technology in Texas in 2005. Funded by a $30 million startup grant from Malaysia, the organization will hold a World Cyber Security Summit next week in conjunction with the WCIT in Kuala Lumpur.
More than 40 countries have been invited to attend, including Australia, Canada, India, Japan, Malaysia, Mexico, Saudi Arabia, Singapore, South Korea, Thailand and the United States.
“We still have not received confirmation of which agency will represent the U.S. government,” IMPACT Chairman Mohd Noor Amin said in a conference call announcing the formation of the group.
More
here.
CBS to Buy C|Net Networks
Margaret Kane writes on the C|Net News Blog:
CBS has agreed to acquire CNET Networks in a deal valued at $1.8 billion, the companies said Thursday.
The purchase price comes to $11.50 per share, representing a 44 percent premium over Wednesday's closing price of $7.95.
The acquisition will make CBS one of the 10 most popular Internet companies in the United States, with a combined 54 million unique users per month, and about 200 million users worldwide, the companies said.
The deal is expected to close in the third quarter. CNET's board has unanimously approved the deal, the company said.
More
here.
Mark Fiore: Blackwater Business School

More Mark Fiore brilliance.
Via The San Francisco Chronicle.
Enjoy!
- ferg
Hackers Cash In On GTA IV Frenzy

Via WebUser.co.uk.
Grand Theft Auto IV, the hugely popular computer game, has been targeted by hackers to spread Trojans designed to steal personal information.
Hackers claim to offer free downloads for versions of the hit car chase game, which sold six million copies in its first week.
They use peer-to-peer networks (P2P) such as Limewire to spread Trojans via the fake links. Trojans are programs that gain backdoor access to PCs to steal personal data or sensitive information like bank details.
"The only thing that many gamers can think of at the moment is Grand Theft Auto IV and hackers are using that interest to try to generate chaos as quickly as they can," said John Safa of software security company DriveSentry.
Mr Safa, who is a former hacker, said he found evidence of Trojans on file-sharing network Limewire within two minutes of logging on. He advised surfers to treat links offering downloads and pug-ins with extreme caution.
More
here.
Air Force Aims for 'Full Control' of 'Any and All' Computers
Noah Shachtman writes on Danger Room:
The Air Force wants a suite of hacker tools, to give it "access" to -- and "full control" of -- any kind of computer there is. And once the info warriors are in, the Air Force wants them to keep tabs on their "adversaries' information infrastructure completely undetected."
The government is growing increasingly interested in waging war online. The Air Force recently put together a "Cyberspace Command," with a charter to rule networks the way its fighter jets rule the skies. The Department of Homeland Security, Darpa, and other agencies are teaming up for a five-year, $30 billion "national cybersecurity initiative." That includes an electronic test range, where federally-funded hackers can test out the latest electronic attacks. "You used to need an army to wage a war," a recent Air Force commercial notes. "Now, all you need is an Internet connection."
On Monday, the Air Force Research Laboratory introduced a two-year, $11 million effort to put together hardware and software tools for "Dominant Cyber Offensive Engagement." "Of interest are any and all techniques to enable user and/or root level access," a request for proposals notes, "to both fixed (PC) or mobile computing platforms... any and all operating systems, patch levels, applications and hardware." This isn't just some computer science study, mind you; "research efforts under this program are expected to result in complete functional capabilities."
Unlike an Air Force colonel's proposal, to knock down enemy websites with military botnets, the Research Lab is encouraging a sneaky, "low and slow" approach. The preferred attack consists of lying quiet, and then "stealthily exfiltrat[ing] information" from adversaries' networks.
More
here.
Off Beat: Ants Swarm Houston Area, Fouling Electronics

An AP newswire article by Linda Stewart Ball, via USA Today, reports that:
In what sounds like a really low-budget horror film, voracious swarming ants that apparently arrived in Texas aboard a cargo ship are invading homes and yards across the Houston area, shorting out electrical boxes and messing up computers.
The hairy, reddish-brown creatures are known as "crazy rasberry ants" — crazy, because they wander erratically instead of marching in regimented lines, and "rasberry" after Tom Rasberry, an exterminator who did battle against them early on.
"They're itty-bitty things about the size of fleas, and they're just running everywhere," said Patsy Morphew of Pearland, who is constantly sweeping them off her patio and scooping them out of her pool by the cupful. "There's just thousands and thousands of them. If you've seen a car racing, that's how they are. They're going fast, fast, fast. They're crazy."
The ants — formally known as "paratrenicha species near pubens" — have spread to five Houston-area counties since they were first spotted in Texas in 2002.
The newly recognized species is believed to have arrived in a cargo shipment through the port of Houston. Scientists are not sure exactly where the ants came from, but their cousins, commonly called crazy ants, are found in the Southeast and the Caribbean.
More
here.
Banks Agree to $24M TJX Breach Settlement With Mastercard
An AP newswire article, via The Boston Globe, reports that:
TJX Cos. has won support from Mastercard-issuing banks for a settlement that will pay them as much as $24 million to cover costs from a massive data breach.
more stories like this
The discount retailer said Wednesday it has won support from financial institutions representing more than 99 percent of MasterCard accounts affected in the breach worldwide. The settlement announced April 2 required at least 90 percent support to take effect.
A similar agreement reached in November with Visa-card issuing banks also was overwhelmingly approved. That agreement set aside as much as $40.9 million to help banks cover costs including replacing customers payment cards and covering fraudulent charges.
More
here.
U.S. OMB To Require Agencies to Secure DNS Servers
John Rendleman writes on GCN.com:
The Office of Management and Budget will soon require agencies to configure their Doman Name System (DNS) servers to the security specifications set by the National Institute of Standards and Technology.
OMB will issue a memo outlining the new policy shortly, according to Karen Evans, OMB’s administrator for electronic government and information technology.
The policy will roughly follow DNS security guidelines already published by the National Institute of Standards and Technology, according to Evans. The guidelines, published in NIST Special Publication 800-81 [.pdf] and titled "Secure Domain Name System (DNS) Deployment Guide"...
More
here.
Oklahoma State University Admits Computer Security Breach
Susan Simpson writes on NewsOK.com:
A breach in an Oklahoma State University computer server exposed names, addresses and Social Security numbers of about 70,000 students, staff and faculty who bought parking and transit services permits in the past six years.
OSU announced the breach and began notifying permit holders today, even though it was discovered in March. The server was shut down at that time and Social Security numbers removed from the site.
After a two-month investigation, OSU officials say they think an intruder's purpose was to use the server for storage and bandwidth capacity to distribute illegal content but they can't rule out that student information was accessed.
More here.
Hat-tip: Dataloss Mailing List
TJX Earnings Suggest that Data Security Doesn’t Worry Consumers
Ben Worthen writes in The Wall Street Journal:
TJX today reported increased sales for its fiscal 2009 first quarter, a sign that the public just doesn’t care about data breaches.
In January 2007, TJX revealed that its computer systems had been accessed by hackers and the credit- and debit-card numbers belonging to tens of millions of customers had been stolen. Over the course of the year, the number of stolen account numbers swelled to more than 90 million and the company became known in security circles as the iconic example of a data breach.
More
here.
Hat-tip: Pogo Was Right
Hacker Writes Rootkit for Cisco Routers
Robert McMillan writes on InfoWorld:
A security researcher has developed malicious rootkit software for Cisco Systems' routers, a development that has placed increasing scrutiny on the routers that carry the majority of the Internet's traffic.
Sebastian Muniz, a researcher with Core Security Technologies, developed the software, which he will unveil on May 22 at the EuSecWest conference in London.
A Cisco rootkit is particularly worrisome because, like Microsoft's Windows, Cisco's routers are very widely used. Cisco owned nearly two-thirds of the router market in the fourth quarter of 2007, according to research firm IDC.
In the past, researchers have built malicious software, known as "IOS patching shellcode," that could compromise a Cisco router, but those programs are custom-written to work with one specific version of IOS.
Muniz's rootkit will be different. "It could work on several different versions of IOS," he said.
More
here.
Identity Fraud Hits Internet Telephony
Via The BBC.
A new type of identity fraud, which sees hackers tapping into voice-over IP telephony accounts, has been highlighted by a VoIP equipment maker.
Usernames and passwords from voice-over IP (VoIP) phone accounts are selling online for more than stolen credit cards, Newport Networks has found.
The information allows someone to use the telephone service for free.
Net telephony fraud is still in its infancy, with eavesdropping on calls being the most common security flaw.
More
here.
Indictments Reveals $77M in Illegal Pill Sales
Julie Murphy writes on The Daytona Beach News:
They served up 44 million doses of prescription drugs over three years that, prosecutors say, brought in $77 million, and now the three current and former Volusia County ringleaders are named in a 73-count indictment filed by federal prosecutors Friday.
In addition to the drug sales done over the Internet, Jude LaCour, 35, formerly of Daytona Beach, and his father, Jeffrey LaCour, 60, of South Daytona are accused of money laundering. Hudsen Smith, 36, of DeLand also was indicted -- along with eight others, seven of them doctors, from across the country -- for drug-trafficking offenses, according to U. S. Attorney Robert O'Neill.
Controlled substances and other prescription drugs were distributed through Jive Network to customers throughout the United States who did not have valid prescriptions, according to the indictment.
Jude LaCour owned and operated Jive Network, the indictment states. Smith was the director of pharmacy and physician operations.
More
here.
Hat-tip: Gary Warner
Unfortunate Toon of The Day: Misplaced Priorities

Via Truthdig.com.
- ferg
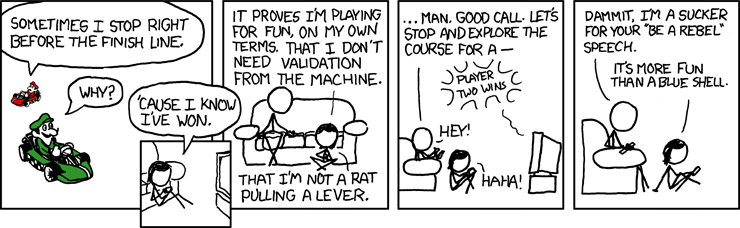
xkcd: The Psychological Finish Line
We
love xkcd!
Enjoy!
- ferg
U.S. Toll in Iraq

Via The Boston Globe (AP).
As of Tuesday, May 13, 2008, at least 4,077 members of the U.S. military have died in the Iraq war since it began in March 2003, according to an Associated Press count.
The figure includes eight military civilians. At least 3,325 died as a result of hostile action, according to the military's numbers.
The AP count is two lower than the Defense Department's tally, last updated Tuesday at 10 a.m. EDT.
More
here.
And as always, the
Iraq Coalition Casualty Count keeps the grim watch on their website
here.
Honor the Fallen.
Mars Lander Team Prepares for 'Seven Minutes of Terror'
 Artist's rendering of The Mars Phoenix Lander.
Artist's rendering of The Mars Phoenix Lander.Victoria Jaggard
writes on
National Geographic News:
After years of planning followed by a ten-month journey, the Mars Phoenix Lander is slated to touch down on the red planet's north pole on May 25.
If successful, the probe will be the first lander to reach a Martian pole and the first to actually touch the planet's water ice.
What's more, it could settle the debate over whether Mars was once a habitable world.
Now, as Phoenix closes in on the last 12 million miles (19 million kilometers) of its journey, NASA scientists are gearing up for the "seven minutes of terror" that could make or break the $420-million mission.
"Approximately 14 minutes before touchdown, the vehicle separates from its cruise stage," Barry Goldstein, Phoenix project manager at the Jet Propulsion Laboratory in California, said today at a press conference.
"At this point we lose communication from the vehicle."
More
here.
Image source: National Geographic / UA / NASA / JPL
FTC Tightens Up CAN-SPAM Rules
Kenneth Corbin writes on internetnews.com:
The Federal Trade Commission has updated its regulations under the CAN-SPAM Act of 2003, making it easier to identify the sender of messages containing brand placements from multiple companies.
The rules, which the FTC passed unanimously and announced yesterday, come after three years of considering public comments on its provisions under CAN-SPAM -- officially known as the Controlling the Assault of Non-Solicited Pornography and Marketing Act of 2003.
The tweaks are aimed at giving consumers a clearer sense of who is sending unwanted marketing messages.
More
here.
MySpace Tells AP It Has Won $234M Spam Judgment
An AP newswire article by Anick Jesdanun, via The Chicago Tribune, reports that:
The popular online hangout MySpace has won a $234 million judgment over junk messages sent to its members in what is believed to be the largest anti-spam award ever, The Associated Press has learned.
A federal judge ruled against two of the Internet's most prominent spam defendants, Sanford Wallace and Walter Rines, after the two failed to show up at a court hearing.
Wallace has earned the nicknames "Spamford" and "spam king" for his past role as head of a company that sent as many as 30 million junk e-mails a day in the 1990s.
"MySpace has zero tolerance for those who attempt to act illegally on our site," said MySpace's chief security officer, Hemanshu Nigam. "We remain committed to punishing those who violate the law and try to harm our members."
More
here.
Five IRS Employees Charged With Snooping on Tax Returns
Kevin Poulsen writes on Threat Level:
Five workers at the Internal Revenue Service's Fresno, California, return processing center were charged Monday with computer fraud and unauthorized access to tax return information for allegedly peeking into taxpayers' files for their own purposes.
"The IRS has a method for looking for unauthorized access, and it keeps audit trails, and occasionally it will pump out information about who's done what," says assistant U.S. attorney Mark McKoen, who's prosecuting the cases in federal court in Fresno. "In general terms, IRS employees are only authorized to access the accounts of taxpayers who write in. They're not allowed to access friends, relatives, neighbors, celebrities."
With tax return information just a few keystrokes away, IRS employees succumb to curiosity often enough that the agency has its own word for such browsing: UNAX, (pronounced you-nacks) , for "unauthorized access." In congressional testimony last month, a Treasury Department investigator said employee prying was on the rise, with 430 known cases in 1998, and 521 last year.
More
here.
Connecting The Dots: RBN - Partners Official Sponsors of ICANN?
Via RBN Exploit.
Russian Business Network (RBN); what if they were out to own the Internet by owning the DNS? The Internet totally relies on DNS (Domain Name System) so obviously this must be the stuff that Hollywood movies are made of, but this nightmare scenario is more real than any of us would like to believe.
This article draws a few of the ingredients together, it is important to stress this is not to discredit ICANN, but to show just how RBN and their associates are applying themselves to the weakness of DNS allocation and exploiting ICANN’s vulnerability via influence, commercial sponsorship and registrar development.
Read on for a fascinating
"follow the breadcrumbs" commentary.
Japanese Internet Satellite Hits 1.2Gbps
Martyn Williams writes on NetworkWorld:
Engineers testing a recently launched Japanese data communications satellite have succeeded in establishing a two-way Internet link running at 1.2G bps (bits per second) each way, they said Monday.
The speed represents a record for satellite communications, according to the Japan Aerospace Exploration Agency and the National Institute of Information and Communications Technology.
The tests were carried out on May 2 as part of verification of the Kizuna satellite. In the tests data was transmitted on two 622M-bps channels both up to the satellite and down to a receiving antenna. Together the combined data transmission speed was 1.2G bps.
More
here.
Estonia, NATO Allies to Sign Deal on Cyber Defense Center
Via The Age.
Estonia and six NATO allies sign a deal this week to provide staff and funds for a new research center designed to boost the alliance's defenses against cyber terrorism.
The agreement to be signed in Brussels on Wednesday comes a year after the small Baltic nation was exposed to an unprecedented wave of cyber attacks that crippled government and corporate computer networks.
The attacks lasted three weeks and followed deadly riots sparked by the relocation of a Soviet war memorial. Many Estonians suspect the Kremlin was behind the virtual strikes but Moscow has denied involvement.
The attacks showed how vulnerable individual countries are to cyber warfare and underscored the need for a joint NATO response, said Estonian Maj. Raul Rikk, who heads the center.
More
here.
Hat-tip: Flying Hamster
Whittling Spam Down to a Manageable Level?
William Jackson writes on GCN.com:
A recent report by security software maker Symantec reveals that spam accounted for an average of 80 percent of traffic hitting e-mail gateways in April, spiking as high as 87 percent at times. That is a daunting figure, but Garth Bruen of KnujOn looks at the problem in a different way.
According to a study being presented this week by KnujOn to the High Technology Crime Investigation Association, 90 percent of the illicit Web sites using spam to generate traffic are clustered on just 20 registrars — that is only 2.5 percent of the 800 registrars accredited by the Internet Corporation for Assigned Names and Numbers.
That can make the spam problem seem almost manageable.
“What is shocking is how concentrated this problem is,” said Bruen, founder of the anti-spam service. “Most providers are playing by the rules. The ones that are not adhering to policy are wreaking the most havoc across the Web.”
More
here.
UK: Home Office Admits Delays Over Criminalisation of DoS Attacks
Richard Thurston writes on SC Magazine Online:
The criminalisation of denial of service attacks is to be delayed by six months, the Home Office has revealed.
Measures to criminalise DoS attacks have been lying unused in existing laws since November 2006, and had been due to be activated this Spring. But that now won't happen until October, the Home Office said today in a statement.
"The Government intends to implement the changes to the Computer Misuse Act 1990, as set out in the Police and Justice Act 2006 and subsequently further amended in the Serious Crime Act 2007, in October 2008," read the statement. "The Government intends to bring all of the changes in together."
The changes will formally criminalise DoS attacks. Though they are technically already illegal, there have been recent cases where hackers have escaped punishment.
More
here.
IT Students Not Being Properly Educated On Security
Tom Young writes on Computing:
IT students are not being educated on how to "bake in" security when designing and developing new software applications, according to research.
The study for the Cyber Security Knowledge Transfer Network (KTN) found that just one in five UK computing undergraduates get no more than five hours education on software security – and many get none at all.
Insecure software applications have a knock-on effect on end users by making their systems vulnerable, according to Bill Whyte, who carried out the research.
“Today’s computing market is a complex value chain of software activities and is as vulnerable as its weakest link," he said.
More
here.
Note: This sort of educational deficiency is directly manifesting itself in the broad scope of web threats that we are seeing with the increasing number of website compromises.
-ferg
More UCLA Personnel Linked to Medical Records Snooping
Charles Ornstein writes in The Los Angeles Times:
California health regulators have connected 14 more people affiliated with UCLA Medical Center, including four physicians, to the improper viewing of celebrity medical records, bringing the number of current and former workers apparently implicated in the snooping scandal to 68.
The additional violations came to light in a report by the California Department of Public Health, which was sent to the hospital Friday. The findings are the latest to stem from reports in The Times about UCLA employees prying into records of celebrities and co-workers. The regulators faulted UCLA for failure to maintain patient confidentiality and report the breaches to regulators.
More
here.
Hackers Indicted for Stealing Credit and Debit Card Numbers From Dave & Buster's - UPDATE
Via PRNewswire.com.
Three defendants have been charged in a federal grand jury indictment and complaint with illegally accessing the computer systems of a national restaurant chain and stealing credit and debit card numbers from that system, Assistant Attorney General Alice S. Fisher of the Criminal Division and U.S. Attorney for the Eastern District of New York Benton J. Campbell announced today.
The 27-count indictment, returned on March 12, 2008, and unsealed today in Central Islip, N.Y., charges Maksym Yastremskiy, of Kharkov, Ukraine, and Aleksandr Suvorov, of Sillamae, Estonia, with wire fraud conspiracy, wire fraud, conspiracy to possess unauthorized access devices, access device fraud, aggravated identity theft, conspiracy to commit computer fraud, computer fraud and counts of interception of electronic communications. A one-count complaint unsealed today in Central Islip charges Albert Gonzalez of Miami with wire fraud conspiracy related to the scheme.
According to the indictment and complaint, Maksym Yastremskiy, a/k/a "Maksik," Aleksandr Suvorov, a/k/a "JonnyHell," and Albert Gonzales, a/k/a "Segvec," engaged in a scheme in which they hacked into cash register terminals at 11 Dave & Buster's Inc. (D&B) restaurants at various locations around the United States in order to acquire "track 2" credit and debit card information. The defendants then sold the stolen data to others who used it to make fraudulent purchases or re-sold it to make such purchases, causing losses to financial institutions that issued the credit and debit cards. Track 2 data includes the customer's account number and expiration date, but not the cardholder's name or other personally identifiable information.
More
here.
Hat-tip: Pogo Was Right
UPDATE: 15:15 PDT: Additional details via Threat Level here. -ferg
Hackers Shut Down Zimbabwe State Newspaper Website
Via Reuters.
Hackers attacked the website of Zimbabwe's state-owned Herald newspaper and shut it down for three days, the newspaper said on Monday.
The Herald is widely seen as the official mouthpiece of President Robert Mugabe's ruling ZANU-PF party and has been critical of the opposition Movement for Democratic Change (MDC) which won the country's disputed March 29 elections.
The website www.herald.co.za has been unavailable since Saturday after it was hacked by someone calling himself "r4b00f". Visitors were redirected to the website of a state-owned Sunday newspaper.
Headlines on the site were replaced by the word Gukurahundi, referring to a campaign of atrocities the government has been accused of committing after independence.
More
here.
Note: It appears to be back online at this time.
-ferg
British Gas Sues Accenture For £182M Over Botched Billing System
Leo King writes on Computerworld UK:
British Gas has served a writ on Accenture for £182 million, over a billing system which it said had “fundamental errors”.
The utility said the Jupiter system, which cost £300 million and which rolled out in 2006 to 2007, was problematic and resulted in issues that “severely impacted” on its customer service department.
In a statement, it said: “In 2001 British Gas employed Accenture to undertake the design and implementation of a new customer billing system. However, when this new system was rolled out during 2006 to 2007 it became apparent that there were problems with the system which severely impacted on British Gas’ customer service operations.”
More
here.
Defense Tech: A Military Botnet? Carpet Bombing in Cyber Space
Col. Charles W. Williamson III writes on Armed Forces Journal:
As much as some think the information age is revolutionary, local networks and the Internet are conceptually similar to the ancient model of roads and towns: Things are produced in one place and moved to another place where they have more value. The road-and-town model works well between cooperating states, but states also compete, and when they do, they sometimes have to defend themselves from attack. In today’s Internet, network “towns” are “fortified” with firewalls, gateways, passwords, port blocking, intrusion detection devices and law enforcement.
This approach uses the same strategy as the medieval castle with its walls, moat, drawbridge, guards, alarms and a sheriff. While castles worked more or less for hundreds of years, they are now abandoned as completely ineffective except against the most anemic attack.
The time for fortresses on the Internet also has passed, even though America has not recognized it. Now, the only consequence for an adversary who intrudes into or attacks our networks is to get kicked out — if we can find him and if he has not installed a hidden back door. That is not enough. America must have a powerful, flexible deterrent that can reach far outside our fortresses and strike the enemy while he is still on the move.
More
here.
Note: I love Kevin Poulsen's
commentary on this issue over at
Threat Level.
-ferg
Hong Kong: Classified 'Watch List' Leaked on Internet
Via TopNews.in.
A government investigation was underway Friday after it was revealed that confidential files from the Immigration Department had been mistakenly leaked on to the internet.
The list, which contained a list of the names of people for officers to watch, plus travel document information and travel records, has been available on the internet since Monday through a file-sharing programme called "Foxy."
The blunder occurred after a newly-recruited immigration officer working at the Lok Ma Chau border point took home some old classified files to study without authorisation.
His computer contained the "Foxy" programme and when he connected to the internet, the files were distributed without his knowledge.
The security blunder is the latest in a series in Hong Kong in the last week.
More
here.
Hat-tip: InfoSec News
U.S. Had Nelson Mandela on Terrorist Watch List

Not sure exactly how I missed this, but...
Mimi Hall writes on U.S. Today:
Nobel Peace Prize winner and international symbol of freedom Nelson Mandela is flagged on U.S. terrorist watch lists and needs special permission to visit the USA. Secretary of State Condoleezza Rice calls the situation "embarrassing," and some members of Congress vow to fix it.
The requirement applies to former South African leader Mandela and other members of South Africa's governing African National Congress (ANC), the once-banned anti-Apartheid organization. In the 1970s and '80s, the ANC was officially designated a terrorist group by the country's ruling white minority. Other countries, including the United States, followed suit.
Because of this, Rice told a Senate committee recently, her department has to issue waivers for ANC members to travel to the USA.
More
here.
U.S. Toll in Iraq, Afghanistan

Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Sunday, May 11, 2008, at least 4,075 members of the U.S. military have died in the Iraq war since it began in March 2003, according to an Associated Press count.
The figure includes eight military civilians. At least 3,322 died as a result of hostile action, according to the military's numbers.
The AP count is one higher than the Defense Department's tally, last updated Friday at 10 a.m. EDT.
As of Sunday, May 11, 2008, at least 427 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures May 3 at 10 a.m. EDT.
Of those, the military reports 294 were killed by hostile action.
More
here and
here.
And as always, the
Iraq Coalition Casualty Count keeps the grim watch on their website
here.
Honor the Fallen.
Newspaper: Hacker Gets Into Chilean Government files, Leaks Personal Data to Internet
An AP newswire article, via The International Herald Tribune, reports that:
A hacker who identified himself as "Anonymous Coward" stole personal data of 6 million Chileans — reportedly including a daughter of the president — and posted it briefly on the Internet, authorities said Sunday.
"This is a serious and delicate issue," said presidential spokesman Francisco Vidal.
Police Chief Jaime Jara confirmed that authorities were investigating the theft of the leaked data, which he said included identity card numbers, addresses, telephone numbers, e-mails and academic background.
The data was taken early Friday from servers at the Education Ministry, the electoral service and the military, Jara said. It was not clear when it appeared on the Internet, but it was first reported to police early Saturday by Leo Prieto, the administrator of a local technology-oriented Internet site who discovered links to the information online.
It did not immediately appear that any banking or financial data had been compromised, and the information had been removed by Saturday morning, Jara said.
More
here.
UK: Whistleblower Spies Left Out in The Cold by New Government Rules
Jason Lewis writes in The Daily Mail:
Britain's spies will not be covered by new rules that protect Government whistleblowers.
Officers from MI5, MI6 and the GCHQ listening station who raise the alarm over their roles must instead have the issue dealt with internally.
However, other Government departments will be covered by the new code of practice designed to ensure public service honesty, integrity and independence.
The rules – in the proposed Constitutional Renewal Bill – will ensure grievances are investigated by independent officials from other departments.
Justice Secretary Jack Straw's decision to exclude spies comes despite the huge growth in size and activities of the main agencies – plus continuing questions over their role in the Iraq war run-up.
More
here.