UK: Private Companies Could Get Access to Millions of NHS Medical Records
Laura Donnelly writes in the Telegraph.co.uk:
The Government is considering giving firms access to a massive computer database which will contain the records of almost every man, woman and child in England.
The information is a goldmine for private companies, who could use it for medical research or for helping them to sell products to the NHS.
But privacy campaigners say they are "horrified" by the proposals which could see patients' postcodes, medical conditions and treatments - and in some circumstances, their names - passed on to third parties without their consent.
The database, part of a long-delayed scheme to give NHS staff access to computerised medical records, will hold details of almost all visits by patients to hospitals and GPs.
More
here.
Hat-tip: Personal Health Information Privacy
Senior CIA Officers Were Target of Islamabad Blast
Via Thaindian News.
Several senior officers of Central Intelligence Agency (CIA) who are reported to be currently visiting Islamabad were the target of the blast at the Marriott Hotel which took place here tonight.
Well placed sources said that Marriott Hotel is usual hotel choice of the US officials and it seems that militants tipped off that certain high level US intelligence officers were currently staying at the hotel.
While no confirmation was available but Pakistan sources said it was clear that the explosion was aimed at specific targets based on a tip off.
At least twenty people were killed, and scores others seriously injured, when an explosives laden truck rammed into Marriott Hotel here today.
More
here.
Hat-tip: ThreatsWatch.org
BBC Customers Deluged By Spam After Hackers Break Into Mailing List
David Barrett writes on the Telegraph.co.uk:
Names and e-mail addresses on a BBC mailing list were exploited by hackers to send "spam", or unwanted e-mail, offering the anti-impotence drugs Viagra and Cialis. Anyone who replied to the sender could have been targeted with scams or computer viruses.
The failing drags the Corporation into the on-going row over how large organisations store private information about individuals. Last night a senior MP called the incident "very serious" and demanded that the BBC take action to tighten its security.
A spokesman for the Corporation confirmed that members of the public had been affected after their details were hijacked from a list of people who had signed up to receive information about next month's BBC Electric Proms music festival.
More
here.
Hat-tip: Pogo Was Right
Chinese Hacker 'Milk Rebellion'
Via The Dark Visitor.
As the scandal over melamine laced food products widens, Chinese hackers seem to be taking up the cause to punish guilty corporations. When we first reported the defacement of the Sanlu Milk Company website, 50 children had suffered kidney stones due to the additive melamine.
Melamine is not meant for human consumption but if added to food stocks, will make it appear to be higher in protein. This is the same additive responsible for the death of many pets last year. The newest reports indicate that there are now over 6,000 children effected and three deaths.
Chinese hackers have also stepped up their efforts to protest against the blatant disregard for public safety. The latest corporation to suffer the wrath of the hacker community was the Mongolian Milk Corporation.
More
here.
Charges Dropped Against Journalists Arrested at RNC
Via Democracy Now!
The St. Paul City Attorney’s office announced Friday it will not prosecute Democracy Now! journalists Amy Goodman, Sharif Abdel Kouddous and Nicole Salazar. St. Paul Mayor Chris Coleman also issued a statement Friday that “the city will decline to prosecute misdemeanor charges for presence at an unlawful assembly for journalists arrested during the Republican National Convention.”
Both announcements come two weeks after the conclusion of the Republican National Convention where over 40 journalists were arrested while reporting on protests taking place outside the convention center.
Upon learning of the news, Democracy Now! Host, Amy Goodman said, “It’s good that these false charges have finally been dropped, but we never should have been arrested to begin with. These violent and unlawful arrests disrupted our work and had a chilling effect on the reporting of dissent. Freedom of the press is also about the public’s right to know what is happening on their streets. There needs to be a full investigation of law enforcement activities during the convention.”
Goodman was arrested while asking police to release Kouddous and Salazar who had been violently arrested while reporting on street demonstrations. After being handcuffed and pushed to the ground, Goodman reiterated that she was was a credentialed reporter. Secret Service then ripped the credential from around her neck.
More
here.
Mukasey Denies 'Dragnet' Surveillance While Demanding Telecom Spying Immunity
David Kravetz writes on Threat Level:
U.S. Attorney General Michael Mukasey on Saturday denied that the Bush administration -- in conjunction with the nation's telecommunication companies -- devised a "dragnet" electronic surveillance program that funneled Americans' communications to the National Security Agency without court warrants.
It was the first time Mukasey, as the nation's top law enforcement official, or the government provided an emphatic and wholesale denial of allegations contained in lawsuits accusing the Bush administration of secretly siphoning Americans' telecommunications to the NSA spy bureau without warrants following the 2001 terror attacks.
Despite the denial, which was contained in a federal court filing [.pdf] publicly available Saturday, Mukasey asked a federal judge to grant immunity to the nation's telecommunications companies accused of assisting the NSA's alleged dragnet surveillance.
More
here.
This American Life: 419 Baiters

I was listening to an recent episode (which originally aired 12 Sept. 2008) (this afternoon while running some errands) of the always entertaining This American Life -- on my local NPR station -- about some "419 Baiters".
As described on the This American Life website, in this episode contains "...stories about people who take the law into their own hands, even when the line between enforcing the rules and breaking them gets kind of hazy."
Also mentioned: 419 Eater
This was a really interesting episode, and given my line of work, especially entertaining.
You can find the entire episode online here at the This American Life website.
Bonus: Uzodinma Okpechi - "I Go Chop Your Dollar", via YouTube.
Enjoy!
- ferg
Image source: BBC - Radio 2 - The Jeremy Vine Show
U.S. Toll in Iraq, Afghanistan

Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Friday, Sept. 19, 2008, at least 4,168 members of the U.S. military have died in the Iraq war since it began in March 2003, according to an Associated Press count.
The figure includes eight military civilians killed in action. At least 3,377 military personnel died as a result of hostile action, according to the military's numbers.
The AP count is four more than the Defense Department's tally, last updated Friday at 10 a.m. EDT.
As of Friday, Sept. 19, 2008, at least 524 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures Friday at 10 a.m. EDT.
Of those, the military reports 375 were killed by hostile action.
More
here and
here.
And as always, the
Iraq Coalition Casualty Count keeps the grim watch on their website
here.
Honor the Fallen.
Toon of The Day: Super Duper Collider

Image source: Glen McCoy / Slate.com
Australian Spy Warns Of Rising Corporate Espionage
Thomas Claburn writes on InformationWeek:
The deputy-director general of the Australian Security Intelligence Organization, who cannot be named under Australian law, warned attendees of Australia's Security in Government Conference 2008 earlier this week that commercial and national espionage are becoming more intertwined.
The deputy-director general, Australia's No. 2 spy, said that geopolitical tensions and ongoing globalization will fuel espionage activity in the years ahead and that spying will affect both the public and private sectors.
"The pressures and opportunities to gain an edge across the public and private sectors -- a distinction, by the way, that not every country recognizes -- will continue to fuel a trade in sensitive information," he said. "The scope of espionage is likely to embrace, but go well beyond, traditional targets such as highly sensitive government information and defense capabilities."
Espionage operations, in other words, will be increasingly directed at businesses.
More
here.
Bill O'Reilly Website Hacked

Via Wikileaks.org.
Wikileaks has been informed the hack was a response to the pundit's recent scurrilous attacks over the Sarah Palin's email story--including on Wikileaks and other members of the press. Hacktivists, thumbing their noses at the pundit, took control of O'Reilly's main site, BillOReilly.com. According to our source, the security protecting O'Reilly's site and subscribers was "non-existent".
[...] image[s], submitted to Wikileaks and confirmed by Wikileaks staff, offers proof of the hack. The image, clearly obtained from BillOreilly.com's administrative interface, shows a detailled list -- including passwords -- of BillOreilly.com subscribers. Although Wikileaks has only released one page, it must be assumed that Bill O'Reilly's entire subscriber list is, as of now, in the public domain.
More
here.
FISMA 2.0 Bill Will Strengthen Cybersecurity, Experts Say
Mary Mosquera writes on FCW.com:
A bill under consideration in the Senate Homeland Security and Governmental Affairs Committee would elevate information security governmentwide by requiring agencies to continuously monitor and measure critical criteria.
The Federal Information Security Management Act of 2008, S. 3474, which builds on the original 2002 FISMA legislation, promises to raise the bar for agencies to prove that they are adequately protecting sensitive information as foreign countries and global cyber villains become more sophisticated at attacking government networks.
The committee plans to vote on the legislation Sept. 23, a committee spokesman said.
More
here.
GraphJam: Since I Began Responding To All Spam

Via GraphJam.com.
- ferg
Cisco Buys Jabber
Marguerite Reardon writes on C|Net News:
Cisco Systems is bolstering its unified communications and collaboration portfolio with the purchase of a corporate instant-messaging company.
On Friday, the networking giant announced it will purchase Jabber, which uses an open-source IM and presence protocol used by Google Talk and Gizmo. The company didn't disclose financial details.
In essence, Jabber's technology allows multiple IM platforms to "talk" to each other. This means that it allows people using tools such as Microsoft Office Communications Server, IBM Sametime, AOL AIM, and Google to send messages to each and get presence information about one another.
Jabber's technology is already used by some large companies including AT&T, BT, EarthLink, FedEx, and JP Morgan.
More
here.
Dear Riyadh Botnet Hunter: Nothing To See Here, Please Move Along
 Click for larger image.
Click for larger image.I like to frequently review my blog referrer logs, sometimes for sheer entertainment (lots of losers looking for
Fergie pr0n) but mostly for open source intelligence -- blogs can sometimes be just like great big honeypots.
I was reviewing my logs a little earlier and ran across this referrer (above) from Riyadh, Saudi Arabia, looking for a "botnet download".
At the moment, I haven't determined whether this falls into the "humorous" category, or the "scary" category. Maybe both.
- ferg
Hackers Shut Down Iranian Clerics' Websites
An AP newswire article, via The Mercury News, reports that:
Iranian media reports say hackers have shut down the Web sites of several hundred Shiite clerics and seminary schools.
Iran's state TV says the hackers were Sunni Muslims based outside Shiite Iran, suggesting a sectarian motive, though it did not say how it knew that.
The semiofficial Fars news agency said the hackers were based in the United Arab Emirates and blocked access to 300 sites. The Emirates is home to a large Iranian community, some of whom oppose Iran's clerical rule.
Thursday's Fars report called it the most serious cyber attack of its kind in the past few years.
Link.
Cyber Attack Data Sharing Is Lacking, Congress Told
Ellen Nakashima writes in The Washington Post:
U.S. intelligence agencies are unable to share information about foreign cyber attacks against companies for fear of jeopardizing intelligence-gathering sources and methods, cybersecurity expert Paul B. Kurtz told lawmakers yesterday.
Kurtz, who served on the National Security Council in the Clinton and Bush administrations, spoke at the first open hearing on cybersecurity held by the House Permanent Select Committee on Intelligence. He and other experts discussed the limitations of President Bush's Comprehensive National Cybersecurity Initiative, announced in January, for safeguarding companies from hackers.
There is no coordinated strategy or mechanism for sharing intelligence about intrusions with companies, nor is there a systematic way for companies to share information with the government, said panelists, who are also members of the Center for Strategic and International Studies commission on cybersecurity, set up last year to advise the next administration.
More
here.
Retail Security: 'Knee-jerk' Standards Compliance Isn't Enough
Tim Greene writes on NetworkWorld:
Businesses certified to be compliant with the Payment Card Industry Data Security Standards (PCI DSS) keep suffering data breaches, but the problem may be more with the way businesses address the requirements than with the PCI standard, experts told an Interop gathering.
Retail chain Forever 21, which last week revealed that nearly 99,000 customer payment cards may have been compromised, claimed it was PCI compliant, said John Pironti, the chief information risk strategist for Getronics.
“They claim to be PCI compliant, Hannaford’s [the supermarket chain that suffered a data breach] claimed to be PCI compliant,” said Pironti, who moderated an Interop panel on the subject of compliance.
But those firms may have restricted compliance auditors’ access to areas where they thought they would meet standards, said Jennifer Mack, vice president of Master Card Worldwide and a member of the PCI Security Council.
More
here.
Cyber Attacks Cripple Opposition Myanmar Media

An AP newswire article by Doug Mellgren, via The Boston Globe, reports that:
The Internet sites of three Myanmar opposition media groups in exile suffered widespread cyber attacks on Thursday, the anniversary of last year's failed uprising against the Southeast Asia country's military dictatorship.
"We think it has something to do with the Saffron Revolution," the anti-government protests by thousands of Buddhist monks in Myanmar on Sept. 18, 2007, said Aye Chan Naing. The chief editor of the Oslo-based radio and TV network Democratic Voice of Burma told The Associated Press that computers began flooding the station's servers with so many requests for information on Wednesday that the systems could not cope.
Similar attacks on Thursday also periodically shut down the servers of the Irrawaddy Magazine and the New Era Journal, Myanmar opposition media groups based in Thailand, he said. At its Web address, Irrawaddy confirmed that its service was not available due to a cyber attack.
More
here.
Bavarian Police Seeking Skype Trojan Informant
Via /.
Bavarian police searched the home of the spokesman for the German Pirate Party (Piratenpartei Deutschland) looking for an informant who leaked information about a government Trojan used to eavesdrop on Skype conversations.
There is a high probability that the Trojan is used illegally. A criminal law specialist said, "The Bavarian authorities worked on the Trojan without a legitimate basis and now try to silence critics." The informant need not worry since "every information that could be used to identify him" is protected against unauthorized access by strong encryption.
The Trojan is supposedly capable of eavesdropping on Skype conversations and obtaining technical details of the Skype client being used. It is deployed by e-mail or in place by the police.
A Pirate Party spokesman said, "Some of our officials seem to want to install the Big Brother state without the knowledge of the public."
Link.
EFF Sues NSA, President Bush, and Vice President Cheney to Stop Illegal Surveillance
Via The EFF.
The Electronic Frontier Foundation (EFF) filed a lawsuit against the National Security Agency (NSA) and other government agencies today on behalf of AT&T customers to stop the illegal, unconstitutional, and ongoing dragnet surveillance of their communications and communications records. The five individual plaintiffs are also suing President George W. Bush, Vice President Dick Cheney, Cheney's chief of staff David Addington, former Attorney General and White House Counsel Alberto Gonzales and other individuals who ordered or participated in the warrantless domestic surveillance.
The lawsuit, Jewel v. NSA, is aimed at ending the NSA's dragnet surveillance of millions of ordinary Americans and holding accountable the government officials who illegally authorized it. Evidence in the case includes undisputed documents provided by former AT&T telecommunications technician Mark Klein showing AT&T has routed copies of Internet traffic to a secret room in San Francisco controlled by the NSA.
That same evidence is central to Hepting v. AT&T, a class-action lawsuit filed by EFF in 2006 to stop the telecom giant's participation in the illegal surveillance program. Earlier this year, Congress passed a law attempting to derail that case by unconstitutionally granting immunity to AT&T and other companies that took part in the dragnet. Hepting v. AT&T is now stalled in federal court while EFF argues with the government over whether the immunity is constitutional and applies in that case -- litigation that is likely to continue well into 2009.
More
here.
ATF Lost Guns, Computers
Holly Watt writes in The Washington Post:
Over a five-year period, the Bureau of Alcohol, Tobacco, Firearms and Explosives lost dozens of weapons and hundreds of laptops that contained sensitive information, according to a scathing report issued yesterday by the Justice Department.
Inspector General Glenn A. Fine identified "serious deficiencies" in ATF's response to lost or stolen items and called the agency's control of classified data "inadequate."
From 2002 to 2007, ATF lost 418 laptop computers and 76 weapons, according to the report. Two weapons were subsequently used to commit crimes. In one incident, a gun stolen from the home of a special agent was fired through the window of another home.
Ten firearms were "left in a public place." One of them was left on an airplane, three in bathrooms, one in a shopping cart and two on the top of cars as ATF employees drove away. A laptop also fell off the top of a car as an agent drove off.
Another weapon "fell into the water while an agent was fishing," according to the report.
More
here.
AP Refuses Secret Service Request for Palin's 'Hacked' e-Mails

An AP newswire article, via Editor & Publisher, reports that:
Hackers broke into the Yahoo! e-mail account that Republican vice presidential candidate Sarah Palin used for official business as Alaska's governor, revealing as evidence a few inconsequential personal messages she has received since John McCain selected her as his running mate.
"This is a shocking invasion of the governor's privacy and a violation of law. The matter has been turned over to the appropriate authorities and we hope that anyone in possession of these e-mails will destroy them," the McCain campaign said in a statement.
The Secret Service contacted The Associated Press on Wednesday and asked for copies of the leaked e-mails, which circulated widely on the Internet. The AP did not comply.
The disclosure Wednesday raises new questions about the propriety of the Palin administration's use of non-government e-mail accounts to conduct state business. The practice was revealed months ago - prior to Palin's selection as a vice presidential candidate - after political critics obtained internal e-mails documenting the practice by some aides.
More
here.
Mark Fiore: Fundamentals

More Mark Fiore brilliance.
Via The San Francisco Chronicle.
Enjoy!
- ferg
Pentagon OKs Spy Satellite Purchases
An AP newswire article by Pamela Hess, via MSNBC.com, reports that:
The Pentagon has approved plans to buy and launch two commercial-class imagery satellites to complement its classified constellation of spy satellites.
The Pentagon will also increase the amount of imagery purchased from private companies operating similar satellites already in the sky.
The decision last week caps months of wrangling between the Air Force, the National Reconnaissance Office, and the National Intelligence Directors Office and the Office of the Secretary of Defense over which agency would buy the satellites for about $1.7 billion. The satellites are to be launched around 2012. The NRO will head satellite acquisition, according to Pentagon documents obtained by The Associated Press.
But critics of the program say the Pentagon is spending billions to re-create existing capabilities and compete with private companies such as GeoEye of Dulles, Va., and DigitalGlobe of Longmont, Colo., which are expected to put four new satellites into orbit by 2013.
More
here.
Proxy Service Could Make It Trivial Tracking Down Palin e-Mail Hackers
Dan Goodin writes on The Register:
Memo to law enforcement investigators tracking down who broke into Sarah Palin's Yahoo email account: Gabriel Ramuglia might be a good place to start.
The 25-year-old webmaster and entrepreneur is the operator of Ctunnel.com, the browsing proxy service used by the group that hacked into the vice presidential candidate's personal email account and exposed its contents to the world. While he has yet to examine his logs, he says there's a good chance they will lead to those responsible, thanks to some carelessness on their part.
More
here.
Notorious Crime Forum 'DarkMarket' Goes Dark
Kevin Poulsen writes on Threat Level:
A wave of bittersweet melancholy has descended on the thousands of phishers, hackers and credit card swindlers inhabiting the computer crime supersite DarkMarket.ws. On Tuesday the site's operator, known as Master Splyntr, announced that he was shuttering the forum, which has hummed along for nearly three years as a premier vehicle of criminal commerce.
"[R]ecent events have proven that even in our best efforts to expel and deactivate the accounts of suspected LE [law enforcement], reporters, and security agents, it is obvious that we haven't been entirely successful," Splyntr wrote in a message on the site.
Chief among those recent events is last week's arrest of Cha0, a Turkish hacker -- and alleged kidnapper -- who served as one of DarkMarket's administrators. Cha0 was known for selling high-quality ATM-skimming hardware that crooks could affix to cash machines to grab debit card swipes and PINs. Turkish police arrested Cha0 on Friday, identifying him as one Cagatay Evyapan.
More
here.
Hacker Posts QuickTime Zero-Day Attack Code
Gregg Keizer writes on ComputerWorld:
A hacker has released attack code that exploits an unpatched vulnerability in Apple Inc.'s QuickTime, just a week after the company updated the media player to plug nine other serious vulnerabilities, a security researcher said today.
The exploit, which was published on the milw0rm.com site Tuesday, takes advantage of a flaw in the "< ? quicktime type= ? >" parameter in QuickTime, which is not prepared to handle excessively-long strings, said Aaron Adams, a researcher with Symantec Corp.'s DeepSight threat notification network.
"Symantec is currently investigating this flaw further to determine the underlying technical details," said Adams in a research note today.
In its present form, the exploit triggers a QuickTime crash, but it may be more serious. "The exploit suggests that code execution may be possible," Adams added, "[and] if this flaw were to allow arbitrary code to run, it may pose a significant risk, because attackers may be able to exploit the issue by embedding a malicious file into a site."
More
here.
Australia: Sydney Spies On Its Citizens
Via Stuff.co.nz.
Tim Rahr was sitting in his backyard in Paddington "re-reading my tattered copy of Franz Kafka" when the phone rang.
It was an officer from the City of Sydney council calling about his application for a resident parking permit.
"She wanted to know why was I applying for a parking permit when she could clearly see on her computer satellite image of my backyard that I had off-street parking," Mr Rahr recalled.
It turned out the "apparatchik from central office" was looking at the wrong backyard but Mr Rahr was outraged that his council could monitor anyone's home: "It gave me a nasty feeling. It was just like Big Brother, like something out of 1984."
The council does not use Google Street View or Google Maps, but rather its own in-house aerial mapping program, E-view.
Mr Rahr said "that makes me feel even more creepy. It's a bit weird they have their own program just to look at us."
More
here.
Image of The Day: McCain Monster

Image source: Jill Greenberg / Today @ PC World
Merged Banks' Names Cybersquatted
Via The BBC.
Domain names for the merged Bank of America/Merrill Lynch as well as for Lloyds TSB/HBOS have been snapped up.
In one case, the domain name has already been listed on eBay, with the site directing visitors to the auction.
As reports of Lehman Brothers' intent to sell itself first surfaced last Friday, cybersquatters had already spotted Barclay's, HSBC and Bank of America as potential buyers.
Accordingly, barclayslehman.com, hsbclehman.com, hsbclehmanbrothers.com and bofalehman.com had been acquired.
With the acquisition of Merrill Lynch by Bank of America this week, cybersquatters registered bankofamericamerrilllynch.com and bofaml.com.
More
here.
Group Posts e-Mail Hacked From Palin Account
Kim Zetter writes on Threat Level:
Vice presidential candidate Sarah Palin's private Yahoo e-mail account was hacked, and some of its contents posted on the internet Wednesday.
The internet griefers known as Anonymous took credit for the intrusion, and screen shots of e-mail messages and photos belonging to the Alaska governor have been published by WikiLeaks. Threat Level has confirmed the authenticity of at least one of the e-mails.
Palin has come under fire for using private e-mail accounts to conduct state business. Critics allege that she uses the account to get around public records laws, as the Bush administration has also been charged with doing.
More
here.
GAO: U.S. Cyber Security Is Weak
A BusinessWeek article by Keith Epstein, via MSNBC.com, reports that:
The federal government cybersecurity team with primary responsibility for protecting the computer networks of government and private enterprise isn't up to the job, according to a draft Government Accountability Office report obtained by BusinessWeek.
The U.S. Computer Emergency Readiness Team, known as US-CERT, mans the front line in any cyber-attack. The group monitors computer networks for hacker threats, investigates suspicious activity online, and is supposed to issue timely alerts to information technology security professionals from the White House to corporations and electric utilities. But the GAO draft report describes US-CERT as bedeviled by frequent management turnover, bureaucratic challenges that prevent timely sounding of alarms, a lack of access to networks across wide swaths of critical terrain, and an inability to fill large numbers of positions with qualified workers.
Five years after the Homeland Security Dept. took charge of the team as a critical safeguard against threats to national security, US-CERT "still does not exhibit aspects of the attributes essential to having a truly national capability," according to the draft report.
More
here.
UAE Banks Home In On Security Breach
Hugh Naylor and H Michael Jalili writes in TheNational.ae:
An investigation by financial institutions into a recent security breach of private ATM card data points to the problem originating with one UAE-based bank, according to people familiar with the investigation into the problem.
Sensitive information including personal identification numbers (PINs) and data from the black magnetic strip on the back of cards was stolen from the bank and then used to make large numbers of fraudulent transactions, mainly from other countries.
“We’re quite close to having completed the case for the prosecution,” said one banker, who spoke only on the condition he neither he or his bank be identified. “And we have a fairly clear idea of how this has occurred.”
Bankers believe that thieves breached a network that banks use to share ATM data. That exposed most, if not all, banks in the UAE to the fraud.
More
here.
Hat-tip: Pogo Was Right
At Adobe's Request, Hackers Nix 'Clickjacking' Talk
Robert McMillan writes on InfoWorld:
After Adobe Systems asked them to keep quiet about their findings, two security researchers have pulled out of a technical talk where they were going to demonstrate how they could seize control of a victim's browser using an online attack called "clickjacking."
Robert Hansen and Jeremiah Grossman had been set to deliver their talk next week at the OWASP (Open Web Application Security Project) conference in New York. But the proof-of-concept code they'd developed to show how their clickjacking attack worked divulged a bug in one of Adobe's products. After a week of discussions with Adobe, the researchers decided last Friday to pull the talk.
Although Hansen and Grossman believe that the clickjacking flaw ultimately lies in the way that Internet browsers are designed, Adobe convinced them to hold off on their discussion until the company could release a patch. "Adobe thinks they can do something to make the hack harder," said Grossman, CTO with White Hat Security, in an interview.
More
here.
UK Government Responds on Phorm
Via The BBC.
In response to EU questions about its legality, it said that it was happy Phorm conformed to EU data laws.
But any future deployments of the system must be done with consent and make it easy for people to opt out.
The European Union had demanded clarification about the system which tracks web habits in order to provide better targeted ads.
The controversy over the Phorm ad-serving system blew up following revelations that the system had been trialled by telecoms firm BT without the consent of users.
Clarifying how the system will be used in response to the EU request, the UK government said future trials must be done with consent from those being targeted.
More
here.
Group: US DHS Should Lose Its Cybersecurity Authority
Grant Gross writes on PC World:
The U.S. Department of Homeland Security has been ineffective in coordinating government cybersecurity efforts and should be stripped of its authority in the area, members of a private cybersecurity task force told members of the U.S. Congress.
The authority for coordinating government cybersecurity efforts and enforcing mandates should be moved to the White House, members of the Center for Strategic and International Studies' (CSIS) cybersecurity commission told lawmakers Tuesday. DHS doesn't have the authority to force other government agencies to strengthen their cybersecurity efforts, said James Lewis, director of the Technology and Public Policy Program.
"We are under attack, and we are taking damage," Lewis told the House of Representatives' Homeland Security Subcommittee on Emerging Threats, Cyber Security and Science and Technology. "The U.S is disorganized and lacks a coherent national [cybersecurity] strategy."
More
here.
Programming Note: Light Posting Today

Well, it looks like I picked up some sort of bug in my travels -- I've come down with a rather nasty chest cold, and I'm not feeling very well at all today.
I'll try to post when I start feeling a bit better...
Thanks,
- ferg
Forever 21 Clarifies Data Breach Details

Evan Schuman writes on StorefrontBacktalk:
On Sept. 12, Forever 21 issued a statement that the chain had been wirelessly breached repeatedly between March 25, 2004, and Aug. 14, 2007, and that thieves "accessed older credit and debit card transaction data for approximately 98,930 credit and debit card numbers," including about 20,500 card numbers taken from one particular store in Fresno, Ca.. "The data included credit and debit card numbers and, in some instances, expiration dates and other card data, but did not include customer name and address. More than half of the affected payment card numbers are no longer active or have expired expiration dates."
It's not clear what the "other card data" was but expiration date retention was likely not in compliance with PCI rules, but it's possible that data could have been grabbed during authorization verification. Forever 21's statement said that "our systems have been certified to be in compliance with the PCI standards, including the data encryption standards," but it didn't say specifically when they were certified, other than "since 2007."
The Forever 21 statement was also vague on information about how and when it learned of the breach. Similar to a statement issued by fellow TJX Breach victim Barnes & Noble, Forever 21 now says that it was contacted by the U.S. Secret Service on the morning of Aug. 5, 2008, "and was advised that our company was identified in the indictment as one of the retail victims."
More
here.
Chinese Hackers Take Down Entire City Network
Via The Dark Visitor.
The Weifang Public Security Bureau has successfully closed a case involving a hacker attack that caused a city-wide network paralysis.
In July of 2008, the Weifang Public Security Bureau Cyber Police received a report from the China Network Communications Corporation stating that the Weifang metropolitan network was under continuous hacker attack and this had caused a two day network outage for the entire city. Since over 90% of the users in Weifang subscribe to China Network Communications, the network outage effected over 400,000 users to include businesses, local government, schools, and hospitals.
Police pursued three suspects over a 3,000 kilometer chase passing through Tianjin, Beijing, Qingdao, Jinan and Shouguang. When the suspects were arrested, the police recovered laptops and eight other pieces of equipment. Two of the suspects charged with the crime worked as supervisors for a competing company and they confessed to hiring a third individual to hack the Weifang Corporation. The hacker used a botnet of over 8,000 computers to attach the company.
More
here.
'Broken: e-Crime Policing in The UK'
Nick Heath writes on Silicon.com:
E-crime policing in the UK is broken, according to one MP spearheading a new cyber crime fighting taskforce.
Former deputy home secretary, MP Alun Michael, told silicon.com that insights from industry as well as his own experience of reporting cyber crime, has left him convinced the system is fatally flawed.
Currently, low-level internet fraud, hacking and spamming attacks must be reported to local police forces. These forces often lack the expertise or resources to deal with the reports or to piece together information on larger attacks happening nationwide.
When Michael reported a number of such low-level cyber crimes, he found no evidence his complaint had been dealt with - a failing repeatedly highlighted by business.
More
here.
DHS Report Says 'Leave Laptops At Home'
Thomas Claburn writes on InformationWeek:
The U.S. Department of Homeland Security appears to be of two minds about the security of information on portable devices.
On the one hand, it defends border searches of laptops as necessary to limit the movements of terrorists, to deter child pornography, and to enforce U.S. laws.
"One of our most important enforcement tools in this regard is our ability to search information contained in electronic devices, including laptops and other digital devices, for violations of U.S. law, including potential threats," said Jayson Ahern, deputy commissioner, U.S. Customs and Border Protection, in an online post in June.
On the other hand, it has warned business and government travelers not to carry laptops or other electronic devices when traveling abroad, as a way to prevent "unauthorized access and theft of data by criminal and foreign government elements."
In a document titled "Foreign Travel Threat Assessment: Electronic Communications Vulnerabilities," [.pdf] published June 10 by the DHS's critical infrastructure threat analysis division and recently posted to Wikileaks, DHS urges business leaders and U.S. officials to "leave [electronic devices] at home" when traveling.
More
here.
U.S. Officials Talk Cyber Initiative With Industry
Ben Bain writes on FCW.com:
Senior government officials today discussed details of the Bush administration’s largely classified, multibillion-dollar national cybersecurity initiative, emphasizing the private sector’s role in those efforts.
Officials from the Homeland Security Department, the Office of the Director of National Intelligence (ODNI), the White House and other agencies involved in the governmentwide effort to secure cyberspace told an industry group today about counterintelligence, supply chain security and research and development portions of the plan.
Disclosures thus far about the National Cyber Security Initiative have largely been limited to information regarding the government’s effort to improve the security of the .gov network.
More
here.
Wiretap Suits Press On in Wake of FISA Amendments
Julian Sanchez writes on ARS Technica:
The class-action lawsuits against telecoms accused of unlawfully participating in NSA surveillance without a court order were back before a federal judge Friday, for the first time since Congress voted to offer retroactive amnesty to the complicit firms.
Long stalled before the Court of Appeals for the Ninth Circuit, the consolidated suits against the telecoms were finally punted back to district judge Vaughn Walker last month, following passage of the FISA Amendments Act. The legislation requires that any civil action against a telecom be thrown out if the Attorney General certifies that the firm received a written directive authorizing their cooperation with the National Security Agency's secretive surveillance program.
That would appear to put an end to the long legal battle, but as Friday's hearing before Walker made clear, attorneys for both sides have a few moves left to play.
More
here.
One Man Pleads Guilty in TJX Breach Case
Ross Kerber writes in The Boston Globe:
Federal prosecutors won a guilty plea yesterday from one of 11 men who made up a ring that was charged last month with the largest data theft case in history, involving tens of millions of customers of retailers, including TJX Cos. of Framingham and BJ's Wholesale Club of Natick.
Separately the government also said it has evidence the group breached the security of many more businesses than previously disclosed.
At a hearing in federal District Court in Boston yesterday afternoon, Damon Patrick Toey, 23, of Miami, pleaded guilty to multiple charges, including wire fraud, credit card fraud, and aggravated identity theft. Prosecutors alleged he helped the accused ringleader, Albert Gonzalez, to break through the computer security of a number of retail stores in the Miami area.
Gonzalez himself appeared at a second hearing later in the day and pleaded not guilty to a set of similar charges.
Prosecutors said both men were key players in a loose-knit ring spanning countries from China to Ukraine that stole or trafficked in more than 40 million payment cards in all, causing more than $400 million in damages. The ring initially accessed customer data by using laptops to penetrate wireless networks of retail stores, from which they were able to access the companies' servers.
More
here.
UK: Fears Over Privacy as Police Expand Surveillance Project
Paul Lewis writes in The Guardian:
The police are to expand a car surveillance operation that will allow them to record and store details of millions of daily journeys for up to five years, the Guardian has learned.
A national network of roadside cameras will be able to "read" 50m licence plates a day, enabling officers to reconstruct the journeys of motorists.
Police have been encouraged to "fully and strategically exploit" the database, which is already recording the whereabouts of 10 million drivers a day, during investigations ranging from counter-terrorism to low-level crime.
But it has raised concerns from civil rights campaigners, who question whether the details should be kept for so long, and want clearer guidance on who might have access to the material.
More
here.
'Cyber Security' Worries Spur Congress to Rethink Electrical Grid
Stephanie Condon writes on C|Net News:
The potential for "cybersecurity" attacks on the United State's electric power grids has spurred politicians to consider legislation to broaden federal authority over electric companies.
Congress already has been consulting with federal agencies and industry associations over how to craft such legislation. On Thursday, legislators sought further input at a hearing before the House Energy and Commerce's subcommittee on energy and air quality.
Industry representatives endorsed the idea of strengthening federal authority in the event of an imminent cybersecurity threat but cautioned against expanding the government's powers too broadly.
"We understand the seriousness of the issue and the need to deal with it," said Susan Kelly, a vice president for the American Public Power Association. "At the same time, we believe that such legislation must be carefully drawn."
The draft legislation under consideration would expand the authority of the Federal Energy Regulatory Commission, which already regulates the nation's bulk power system as allowed by the Federal Power Act. A final draft of the bill will likely be considered by the committee next week, following a classified briefing with intelligence agencies, said Rep. Rick Boucher, chairman of the subcommittee.
More
here.
Clandestine Intelligence-Gathering Turns To Open-Source Data
Bob Brewin writes on GovExec.com:
The global explosion in Internet-based new media has made open source information invaluable to intelligence agencies, CIA Director Michael Hayden said on Friday at the ODNI Open Source Conference in Washington.
Sections of the president's daily intelligence brief are "derived exclusively from open source intelligence" Hayden told the conference, which attracted more than 3,000 attendees from intelligence agencies, academia and industry. Those sections bear the stamp of the Office of the Director of National Intelligence's Open Source Center.
Development of an open source intelligence organization was one of three key objectives for the ODNI when it was created in 2005, Hayden said, just behind the establishment of a central clandestine service branch and a security branch within the FBI. The Open Source Center, which is managed by the CIA and serves the entire intelligence community, has paid rich dividends since it went into operation in November 2005, he noted.
ODNI built the center around the CIA's Foreign Broadcast Intelligence Service which monitors overseas radio and television programs, and today uses that core capability to pump more than 300 foreign TV broadcasts into intelligence operations centers, Hayden said.
More
here.
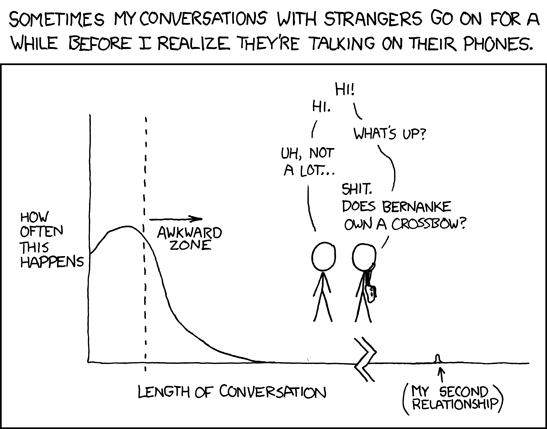
xkcd: One-Sided
Click for larger image.
Yes, we love
xkcd.
Enjoy!
- ferg
India's Controversial Use of Brain Scans in Courts Is Debated
Anand Giridharadas writes in The New York Times:
The new technology is, to its critics, Orwellian. Others view it as a silver bullet against terrorism that could render waterboarding and other harsh interrogation methods obsolete. Some scientists predict the end of lying as we know it.
Now, well before any consensus on the technology’s readiness, India has become the first country to convict someone of a crime relying on evidence from this controversial machine: a brain scanner that produces images of the human mind in action and is said to reveal signs that a suspect remembers details of the crime in question.
For years, scientists have peered into the brain and sought to identify deception. They have shot infrared beams through liars’ heads, placed them in giant magnetic resonance imaging machines and used scanners to track their eyeballs. Since the Sept. 11 attacks, the United States has plowed money into brain-based lie detection in the hope of producing more fruitful counterterrorism investigations.
The technologies, generally regarded as promising but unproved, have yet to be widely accepted as evidence — except in India, where in recent years judges have begun to admit brain scans. But it was only in June, in a murder case in Pune, in Maharashtra State, that a judge explicitly cited a scan as proof that the suspect’s brain held “experiential knowledge” about the crime that only the killer could possess, sentencing her to life in prison.
More
here.
Mark Fiore: De-Elitification

More Mark Fiore brilliance.
Via The San Francisco Chronicle.
Enjoy!
- ferg
Taliban Using Skype Phones to Dodge MI6
Glen Owen writes in The Daily Mail:
Taliban fighters targeting British troops in Afghanistan are using the latest ‘internet phones’ to evade detection by MI6, security sources said last night.
Skype, a popular piece of consumer software that allows free calls to be made over the web, has been adopted by insurgents to communicate with cells strung out across the country.
Unlike traditional mobile calls, which can be monitored by RAF Nimrod spy planes, Skype calls – the commercial application of a technology called Voice Over Internet Protocol (VoIP) – are heavily encrypted.
The British and American governments are investing considerable resources to crack the codes, and in the UK the Government is introducing legislation to force internet service providers to log all web activity by subscribers, which could then be turned over to the security services on demand.
More
here.
.ie Internet Registry Scam
Via DomainNews.com.
It has once again come to the attention of the IEDR that a company operating under the name "Internet Register Ireland" is contacting businesses with registered .ie domain names by post and by fax, soliciting domain holders to register their domain name with the "Internet Register Ireland".
The "Internet Register Ireland" will request you to fill out their form and return it to them signed. It should be noted that they charge an excessive fee of approx €958 for the registration of your domain name in their database. The “Internet Register Ireland” previously operated the same practice in Ireland in September 2007 and November 2006 and have been operating similar schemes throughout Europe and Canada throughout the past year.
More
here.
e-Mail Notice Sent Prior to Delhi Explosions
Agam Shah writes on CIO.com:
An e-mail claiming responsibility for the bomb blasts in India's capital Delhi on Saturday was sent five minutes prior to the actual explosions, media organizations said.
The e-mail, sent by a poster claiming to be from the Indian Mujahideen, said that Delhi was about to be hit with blasts, and the militant organization would strike other locations in India. The e-mail, which was sent to news organizations in India including Zee Enterprise, was sent from a Yahoo e-mail account that was traced back to a Mumbai address.
On further investigation, it was determined the e-mail was sent around the time of the first blast, Parambir Singh, additional commissioner of Mumbai police's antiterror unit told the Press Trust of India on Sunday.
A coordinated stream of five bombs exploded in different areas in Delhi on Saturday evening, including densely populated areas, killing close to 30 people. More bombs were being defused, according to media reports.
More
here.
Hackers Block Release of Al Qaeda's 9/11 Terror Tape
Via The Hindustan Times.
Hackers prevented Al Qaeda from releasing a videotape to mark the seventh anniversary of 9/11. Al Qaeda has traditionally issued a video or audiotape by either Osama bin Laden or Ayman al Zawahiri, the terror network’s two leaders, to mark their massive terrorist attack on the US.
As-Sahab, Al Qaeda’s media unit, had indicated earlier this week that it would post such a videotape on September 11. As-Sahab had banner images on the internet showing a silhouetted head with a question mark and the words, “Wait 11 September”.
The US-based intelligence group IntelCenter had speculated the video would be a message from Osama or Zawahiri with a recording of the last will and testament of Mohammed Atta, one of the leaders of the 9/11 attackers.
Sources close to US intelligence said, “Hackers knocked out Al Qaeda’s online means of communication, thus preventing them from posting anything to commemorate the anniversary.”
Western intelligence suspects two hackers who have targeted Islamicist sites before were responsible: Aaron Weisburd from Internet Haganah and Rusty Shackleford from the web group My Pet Jawa.
Both have been active in ongoing Internet battle between Islamicist hackers and their opponents.
More
here.
FBI Seeks New Surveillance Guidelines
An AP newswire article, via USA Today, reports that:
The Bush administration unveiled proposed guidelines Friday that would give the FBI more tools to assess national security and foreign intelligence threats.
Agents would be permitted to use tactics only allowed in criminal cases: physical surveillance, recruitment of sources and "pretext interviews" — where the real purpose would not be revealed.
Justice Department and FBI senior officials briefed reporters on the draft guidelines, but would not be quoted by name because they were discussing proposals that are still likely to be changed.
Some Democratic senators and civil liberties groups have said the proposals would allow Americans to be targeted in part by their race, ethnicity or religion — and be spied on without any other basis for suspicion.
The officials acknowledged that those factors could play a role in national security and foreign intelligence cases. But they said these factors already can be considered under 2003 rules that are not changing.
According to the officials, the surveillance, recruitment and interview rules are too restrictive in allowing the FBI to become a post-Sept. 11 intelligence agency that can stop terrorists before they strike.
More
here.
Directi, KnujOn, HostExploit to Work Together
Maxim Weinstein writes on StopBadware.org:
I recently blogged about two reports related to business practices of web-related companies. One of those companies, Directi, was the direct target of the KnujOn report and was mentioned in Jart Armin’s report, as well. I blogged about Directi’s response to the KnujOn report last week.
This week, Directi, KnujOn, and HostExploit (Jart’s company) released a joint statement:
In light of recent developments, Jart Armin of HostExploit.com, Bhavin Turakhia, CEO of Directi and Garth Bruen of Knujon have had an open dialogue and mutually agreed to release this joint statement as an accurate representation of facts, clearing any previous misconceptions and reaffirming their common goal to combat abuse on the Internet.
You can read the statement for the specifics, but I want to applaud the public commitment by all three parties to working together to fight badware. So far, Jart tells us that they have removed thousands of badware and spam domains. It will be interesting to see how this plays out and, in particular, how Garth, Jart, and other members of the security community evaluate Directi’s follow-through.
More
here.
Virginia 'De-Convicts' AOL Junk Mailer Jeremy Jaynes
Austin Modine writes on The Register:
Notorious American AOL spammer Jeremy Jaynes had his nine year federal prison sentence overturned today, when Virginia's high court ruled the state's tough "anti-spam" law violates the First Amendment right to free speech.
The court unanimously agreed Virginia's anti-spam law is "unconstitutionally overbroad" because it bans all unsolicited bulk email with false or misleading originating addresses, both commercial and noncommercial.
The law considers unsolicited bulk email a felony if more than 10,000 recipients are mailed in a 24-hour period.
Justice Steven Agee wrote in today's ruling that the state law violates "the right to engage in anonymous speech, particularly anonymous political or religious speech" protected by the First Amendment.
More
here.
San Francisco Hunts for Mystery Device on City Network
Robert McMillan writes on NetworkWorld:
With costs related to a rogue network administrator's hijacking of the city's network now estimated at $1 million, city officials say they are searching for a mysterious networking device hidden somewhere on the network.
The device, referred to as a "terminal server" in court documents, appears to be a router that was installed to provide remote access to the city's Fiber WAN network, which connects municipal computer and telecommunication systems throughout the city. City officials haven't been able to log in to the device, however, because they do not have the username and password.
In fact, the city's Department of Telecommunications and Information Services (DTIS) isn't even certain where the device is located, court filings state.
The router was discovered on Aug. 28. When investigators attempted to log in to the device, they were greeted with what appears to be a router login prompt and a warning message saying "This system is the personal property of Terry S. Childs," according to a screenshot of the prompt filed by the prosecution.
More
here.
Hackers Hit Large Hadron Collider Website
Ellen Messmer writes on Computerworld UK:
Hackers have broken into the network of the Swiss particle-physics laboratory operating the Large Hadron Collider that began smashing atoms this week.
The hackers, calling themselves the "Greek Security Team," defaced the CERN Web site with comments made in Greek, according to the Daily Telegraph, which reported the incident today. CERN has now taken down this public-facing Web site, and according to the Telegraph, CERN spokesman James Gillies said, "There seems to be no harm done."
It's not believed that the Greek Security Team hackers -- thought to be targeting the Compact Muon Solenoid Experiment (CMS) that is using the Large Hadron Collider to make new discoveries about particle physics -- were able to penetrate further into the CERN network of control systems for the giant collider.
More
here.
UAE Banks Step Up Security After Credit Card Thefts
Via Arabian Business.
Banks in the United Arab Emirates have introduced new security measures and warned customers to change debit and credit card codes after fraudsters used counterfeit cards to withdraw money from accounts.
"Following a countrywide increase in card fraud, Lloyds TSB Middle East, as part of a coordinated approach with other banks in the UAE, strongly recommends that all of our customers urgently change the pin numbers of their debit cards," the bank said in a statement on Thursday.
Lloyds TSB, HSBC, Citibank, National Bank of Abu Dhabi and Dubai Bank are among lenders that have sent statements warning customers of the threat in recent days after a spree of fraudulent withdrawals both inside and outside of the UAE.
Some of the banks have promised to reimburse customers who have lost money while others have resorted to blocking customer transactions in some overseas locations to limit the problem.
It was not clear how much money had been stolen from UAE account-holders, but Dubai Bank said it had temporarily blocked international use of its automated teller machines after 42 of its customers were affected.
More
here.