Best Western Hotels Compromise: 8 Million Victims in World's Biggest Cyber Heist - UPDATE
Iain S. Bruce writes on The Sunday Herald:
An international criminal gang has pulled off one of the most audacious cyber-crimes ever and stolen the identities of an estimated eight million people in a hacking raid that could ultimately net more than £2.8billion in illegal funds.
A Sunday Herald investigation has discovered that late on Thursday night, a previously unknown Indian hacker successfully breached the IT defences of the Best Western Hotel group's online booking system and sold details of how to access it through an underground network operated by the Russian mafia.
It is a move that has been dubbed the greatest cyber-heist in world history. The attack scooped up the personal details of every single customer that has booked into one of Best Western's 1312 continental hotels since 2007.
Amounting to a complete identity-theft kit, the stolen data includes a range of private information including home addresses, telephone numbers, credit card details and place of employment.
More
here.
Note: Of course, this isn't the "biggest" cyber theft incident -- that would be the
TJX thefts with roughly 100 million credit cards stolen.
-ferg
UPDATE: 20:27 PDT, 24 August 2008: Best Western Hotels has issued a statement saying that the claims their systems have been compromised is unsubstantiated. -ferg
UK: Thousands of Cyber Attacks Each Day on Key Utilities
Jonathan Richards writes on The Times Online:
Computer networks controlling electricity supplies, telecommunications and banking are being attacked thousands of times a day in a new cyberwar against Britain waged by criminals and terrorists — some of them backed by foreign states — the Government has said.
Lord West of Spithead, the Security Minister, told The Times that a mixture of state-sponsored individuals “and those operating at a terrorist level” frequently tried to break into the key networks.
Intelligence organisations such as MI5 have given warning of the threat of state-sponsored “cyber-espionage” from countries such as Russia and China, but this is thought to be the first time that the Government has quantified the extent of the threat to the nation’s networks, furthering the prospect of more widespread computer-based “warfare”.
“If you take the whole gamut of threats, from state-sponsored organisations to industrial espionage, private individuals and malcontents, you’re talking about a remarkable number of attempted attacks on our system — I’d say in the thousands,” Lord West said. “Some are spotted instantly.Others are much, much cleverer.”
More
here.
New Scientist: Surveillance Made Easy
Laura Margottini writes on NewScientist.com:
"This data allows investigators to identify suspects, examine their contacts, establish relationships between conspirators and place them in a specific location at a certain time."
So said the UK Home Office last week as it announced plans to give law-enforcement agencies, local councils and other public bodies access to the details of people's text messages, emails and internet activity. The move followed its announcement in May that it was considering creating a massive central database to store all this data, as a tool to help the security services tackle crime and terrorism.
Meanwhile in the US the FISA Amendments Act, which became law in July, allows the security services to intercept anyone's international phone calls and emails without a warrant for up to seven days. Governments around the world are developing increasingly sophisticated electronic surveillance methods in a bid to identify terrorist cells or spot criminal activity.
However, technology companies, in particular telecommunications firms and internet service providers, have often been criticised for assisting governments in what many see as unwarranted intrusion, most notably in China.
Now German electronics company Siemens has gone a step further, developing a complete "surveillance in a box" system called the Intelligence Platform, designed for security services in Europe andAsia. It has already sold the system to 60 countries.
More
here.
U.S. Toll in Iraq, Afghanistan

Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Friday, Aug. 22, 2008, at least 4,146 members of the U.S. military have died in the Iraq war since it began in March 2003, according to an Associated Press count.
The figure includes eight military civilians killed in action. At least 3,370 died as a result of hostile action, according to the military's numbers.
The AP count is two fewer than the Defense Department's tally, last updated Thursday at 10 a.m. EDT.
As of Friday, Aug. 22, 2008, at least 508 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department.
The department last updated its figures Thursday at 10 a.m. EDT. Of those, the military reports 361 were killed by hostile action.
More
here and
here.
And as always, the
Iraq Coalition Casualty Count keeps the grim watch on their website
here.
Honor the Fallen.
Ohio Voting Machines Contained Programming Error That Dropped Votes
Mary Pat Flaherty writes on The Washington Post's "The Trail" Blog:
A voting system used in 34 states contains a critical programming error that can cause votes to be dropped while being electronically transferred from memory cards to a central tallying point, the manufacturer acknowledges.
The problem was identified after complaints from Ohio elections officials following the March primary there, but the logic error that is the root of the problem has been part of the software for 10 years, said Chris Riggall, a spokesman for Premier Election Solutions, formerly known as Diebold.
The flawed software is on both touch screen and optical scan voting machines made by Premier and the problem with vote counts is most likely to affect larger jurisdictions that feed many memory cards to a central counting database rapidly.
More
here.
How Hacker Found Proof of He Kexin's Age - UPDATE
Stephen Hutcheon writes on The Sydney Morning Herald:
In his spare time Mike Walker likes to find things on web servers that were never meant to be found.
On Monday, after curiosity got the better of him, the 33-year-old computer security consultant toiled for hours without success, as he tried to dig up more information about the allegedly under-aged Chinese gymnast He Kexin.
On Tuesday, after redefining the parameters of his Google Hack, he hit the jackpot. Bingo! The mother lode.
On Google's cache he found evidence of a record of He Kexin's birth on a spreadsheet belonging to the General Administration of Sport of China - the country peak sports body.
But the data had been removed.
On the Chinese search engine Baidu, he went one better. He found two caches of Excel spreadsheet which had been published on the web and both of them showed He Kexin's birthday as January 1, 1994.
More
here.
UPDATE: 23:28 PDT, 23 August 2008: Oh -- it was just a paperwork mix-up. Right. -ferg
Kevin Mitnick Looks Back in Forbes Interview
 Kevin Mitnick
Kevin MitnickAndy Greenberg
writes on
Forbes.com:
There was a time when the name Kevin Mitnick represented everything that the world's chief security officers feared most: a reckless geek with the power to break any network in the world.
Prosecutors and journalists, including the New York Times' John Markoff, further aggrandized his cybercrime exploits, claiming he was a criminal hacker mastermind who had wiretapped the FBI to stay ahead of his pursuers, hacked into Pentagon computers and could launch nuclear weapons simply by whistling tones into a pay phone.
Mitnick wound up serving five years in prison--four before his conviction and eight months in solitary confinement. He got out in 2000. Now Mitnick, 45, has reinvented himself as a security consultant. In his second career, he performs the same cyber-intrusions he once used to steal data to suss out flaws in companies' defenses. That means Mitnick has to convince major corporations and even government agencies that he's a trustworthy professional--rather than a cyberpunk.
But Mitnick isn't hiding his hacker background. In fact, he says the notoriety of his criminal past has only boosted his business. And last month, at the HOPE hacker conference in New York, Mitnick announced that a lapsed statute of limitations will allow him to publish a book detailing his exploits as a cybercriminal and a fugitive. The book won't be ready for about a year but Forbes.com talked with Mitnick about telling all, the state of cybersecurity and why true hackers make the best security professionals.
More
here.
Canadian Police: Identity Thieves Cashing In On Canadians' Info Online
Via CBC News.
Criminal organizations are cashing in on lucrative but low-risk identity theft as Canadians increasingly put personal information in the public realm, law enforcement agencies warned Friday.
"As we move more and more to the internet and technology being used, the risks are increasing, and I think that a lot of the public are not very careful about their identity," RCMP Commissioner William Elliott said.
The collection and trafficking of personal information brings in big profits for organized criminal groups, with little possibility of detection and prosecution, warns the 2008 annual report from Criminal Intelligence Service Canada, a network for exchanging information on organized crime that includes about 400 law enforcement agencies .
Lower-level criminal groups are typically involved in collection and trafficking of personal information while higher-level groups use the data to commit crimes, the report says.
More
here.
Shocker: Flaws Found in U.S. Terrorist Watch List
Siobhan Gorman writes in The Wall Street Journal:
The government's main terrorist-watch-list system is hobbled by technology challenges, and the $500 million program designed to upgrade it is on the verge of collapse, according to a preliminary congressional investigation.
The database, which includes an estimated 400,000 people and as many as 1 million names, has been criticized for flagging ordinary Americans. Now, the congressional report finds that the system has problems identifying true potential terrorists, as well.
Among the flaws in the database, which was quickly built by Lockheed Martin Corp. in the wake of the Sept. 11, 2001, terrorist attacks, is its inability to do key-word searches. Instead, an analyst needs to rely on an indexing system to query the database, according to congressional investigators who learned of the issues from a whistleblower. Lockheed spokesman Tom Jurkowsky said he could not comment on a report he had not read.
Meanwhile, tens of thousands of "potentially vital" messages from the Central Intelligence Agency have not been included in the database, known as the Terrorist Identities Datamart Environment, or TIDE, congressional investigators found.
More
here.
Rights Group Suing AT&T for Spying Will Sue Government Too
Ryan Singel writes on Threat Level:
A civil liberties group suing AT&T for helping the government warrantlessly spy on Americans isn't abandoning its lawsuit after Congress voted to give retroactive immunity to the nation's telcoms.
Instead, the scrappy San Francisco-based Electronic Frontier Foundation now says that it will expand its efforts and sue the government over the spy program that operated outside of the court system for more than six years.
"If Congress wants to shut down one avenue, we will go down another," EFF legal director Cindy Cohn said, noting that the amnesty provisions in the FISA Amendments Act of 2008 do not apply the government itself as the Administration had first wanted.
The full extent of the government's warrantless spying has yet to be revealed, but it is reported to involve massive data-mining of Americans' phone records, and broad wiretapping of communicationst that enter or leave the U.S. border .
After the portion that targeted Americans' international communications was submitted to the nation's acquiesent secret spying court for blanket approval in January 2007, the program was quickly found to be illegal.
More
here.
PCI Council to Merchants: Kiss Your WEP Goodbye
Bill Brenner writes on CSO Online:
The security savvy know WEP is full of holes and shouldn't be used. That's not stopping some merchants from doing just that.
As a result, the PCI Security Standards Council is mandating its eradication in the next two years. The first step toward that is some fresh language on wireless security in the next version of the PCI Data Security Standard (PCI DSS).
The council released a summary [.pdf] of PCI DSS Version 1.2 earlier this week and will officially launch it Oct. 1. Among other things, the council will remove references to WEP security and instead push organizations to use stronger forms of wireless network encryption. New WEP deployments won't be allowed after March 31, 2009, and current implementations must stop using WEP after June 30, 2010.
More
here.
ID Theft Sentencing: When The Punishment Doesn't Fit The Crime
Tim Wilson writes on Dark Reading:
Some Canadian critics are outraged today over the sentencing of Bradley Moisan, the man convicted of heading up the largest identity theft ring in the history of the country.
Moisan walked out of jail about three days after his sentence, according to Canadian news reports about the identity theft conviction. He had faced a maximum of 14 years in prison.
Moisan pleaded guilty to his crimes, and the judge gave him a year in jail. But because he had spent six months in custody awaiting trial -- time which is weighed twice because it's before trial -- he had effectively finished the sentence before it began.
Last February, police discovered that a nondescript building in Newton, Canada, was actually an identity theft factory, with hundreds of CDs packed with names, address, phone numbers, and mothers' maiden names. They recovered stacks of passports, driver's licenses, and credit cards -- both real and fake -- as well as reams of stolen mail. Moisan and an accomplice were charged and convicted of the thefts.
More
here.
Red Hat, Fedora Servers Compromised
Elinor Mills writes on C|Net News:
Red Hat warned on Friday that a network attack compromised some servers last week that are involved with both its commercially supported and free versions of Linux.
The breaches involved Red Hat Linux Enterprise servers and those from its community-supported Fedora project that it sponsors.
Red Hat said in a security advisory that it is confident the intrusion did not compromise the Red Hat Network, which is the chief mechanism used to distribute changes to its Red Hat Enterprise Linux product, or updates sent over the network. Therefore customers are not at risk, the company said.
A Fedora project leader issued an alert to a Fedora e-mail list that some Fedora servers were taken offline after they were found to have been illegally accessed last week.
More
here.
Security Fix: Web Fraud 2.0 - Distributing Your Malware
Brian Krebs writes on Security Fix:
The allure of cyber crime lies in its promise of quick riches, much like that of the illegal drug trade. But building a network of hacked personal computers that can distribute your data-stealing malicious software is a time-consuming process that requires a modicum of skill. That is, until recently, when several online services have emerged that promise to help would-be cyber crooks graduate from common street dealers to distributors overnight.
Such is the aim of services like "loads.cc," which for a small fee will take whatever malware you provide and inject it into a pre-selected number of PCs already compromised and under the thumb of the service owners.
More
here.
Internet Eavesdropping: A Brave New World of Wiretapping
Whitfield Diffie and Susan Landau write on Scientific American:
As long as people have engaged in private conversations, eavesdroppers have tried to listen in. When important matters were discussed in parlors, people slipped in under the eaves—literally within the “eavesdrop”—to hear what was being said. When conversations moved to telephones, the wires were tapped. And now that so much human activity takes place in cyberspace, spies have infiltrated that realm as well.
Unlike earlier, physical frontiers, cyberspace is a human construct. The rules, designs and investments we make in cyberspace will shape the ways espionage, privacy and security will interact. Today there is a clear movement to give intelligence activities a privileged position, building in the capacity of authorities to intercept cyberspace communications. The advantages of this trend for fighting crime and terrorism are obvious.
The drawbacks may be less obvious. For one thing, adding such intercept infrastructure would undermine the nimble, bottom-up structure of the Internet that has been so congenial to business innovation: its costs would drive many small U.S. Internet service providers (ISPs) out of business, and the top-down control it would require would threaten the nation’s role as a leader and innovator in communications.
Furthermore, by putting too much emphasis on the capacity to intercept Internet communications, we may be undermining civil liberties. We may also damage the security of cyberspace and ultimately the security of the nation. If the U.S. builds extensive wiretapping into our communications system, how do we guarantee that the facilities we build will not be misused? Our police and intelligence agencies, through corruption or merely excessive zeal, may use them to spy on Americans in violation of the U.S. Constitution. And, with any intercept capability, there is a risk that it could fall into the wrong hands. Criminals, terrorists and foreign intelligence services may gain access to our surveillance facilities and use them against us. The architectures needed to protect against these two threats are different.
Such issues are important enough to merit a broad national debate. Unfortunately, though, the public’s ability to participate in the discussion is impeded by the fog of secrecy that surrounds all intelligence, particularly message interception (“signals intelligence”).
More
here.
These Guys Rock, Too
 Todd Rogers (L) and Phil Dalhausser
Todd Rogers (L) and Phil Dalhausser The
U.S. Men and
Women make a full Gold Medal sweep in Beach Volleyball in Beijing.
Rock and roll!
- ferg
Image source: The Patriot Ledger / Holly Stein
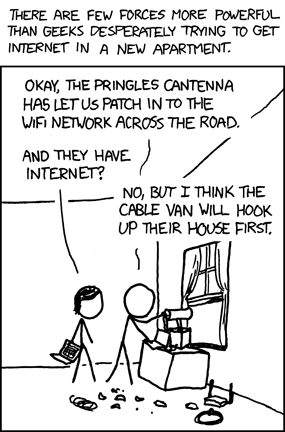
xkcd: Moving - And Getting Connectivity
We've all
been there.
And yes - we
love xkcd.
Enjoy!
- ferg
Pentagon Contracts Lockheed-Martin For Messaging Support
Via UPI.
The U.S. Defense Department has contracted Lockheed Martin to support the Pentagon Telecommunications Center's messaging systems.
U.S. company Lockheed Martin, under a two-year, $5.8 million follow-on network-centric contract, will continue to support the Pentagon's message routing infrastructure.
Officials say the Lockheed Martin contract with the Pentagon Telecommunications Center supports the message technologies that provide a constant open channel to top defense officials, commanders and other decision-makers in order to maintain U.S. military operations.
More
here.
Brazilian Charged in U.S. in Connection With Operating Botnet
Elinor Mills writes on C|Net News:
A Brazilian man has been charged in connection with operating a botnet composed of more than 100,000 computers infected with malicious software allegedly designed to send spam, the U.S. Department of Justice said on Thursday.
A federal grand jury in New Orleans handed down an indictment charging Leni de Abreu Neto, a 35-year-old from Taubate, Brazil, with one count of conspiracy to cause damage to computers worldwide. If convicted, he faces up to five years in prison and up to three years of supervised release, as well as a fine of $250,000 or more based on the gross amount of monetary loss determined to have been suffered by victims.
The indictment alleges that Neto conspired with Nordin Nasiri, a 19-year-old from Sneek, Netherlands, to "use, maintain, lease and sell an illegal botnet."
More
here.
IOC Reportedly Probing Chinese Gymnast's Age After Security Expert Reveals Documents - UPDATE [2]
Via MSNBC.com.
The International Olympic Committee is launching an investigation into Chinese gold-medal-winning gymnast He Kexin's age, the Times of London is reporting. Mounting allegations that Chinese authorities covered up the Olympian's age triggered the IOC to act.
Mike Walker, a U.S. computer expert said on Thursday, that he had uncovered Chinese documents that prove He is just 14, making her ineligible to compete. Officials in China insist she is 16.
If an investigation finds that He is indeed 14, and not 16 as her passport indicates, she could be stripped of her gold medals in both team and individual gymnastics events.
More
here.
UPDATE: 23:01 PDT: It looks like the IOC
is waffling on the issue. We'll have to wait and see what the final outcome of this mess turns out.
-ferg
UPDATE: 23:28 PDT, 23 August 2008: Oh -- it was just a paperwork mix-up. Right. -ferg
In Passing: Gene Upshaw

Appeals Court Punts on AT&T Spying Case Appeal
Ryan Singel writes on Threat Level:
More than a year after hearing oral arguments, a federal appeals court has declined to rule on whether lawsuits targeting the president's warrantless wiretapping of Americans are too secret to be challenged in court, according to an order released Thursday.
Instead, the court deferred to Congress's recent passage of amnesty for telecoms that secretly helped the spying, returning the case to a lower court where the government will fight to have the suits dismissed using the amnesty provision.
More
here.
These Girls Rock
 Kerri Walsh (L) and Misty May-Treanor
Kerri Walsh (L) and Misty May-TreanorIn the rain.
Rock and Roll.
Congrats -- you rock. Gold.
- ferg
Mark Fiore: Vote For Oil!

Perhaps the most brilliant Mark Fiore cartoon ever.
Via The San Francisco Chronicle.
Enjoy!
- ferg
DARPA Awards Phase III of Disruption Tolerant Networking System to BBN
Via UPI.
The U.S. Defense Advanced Research Projects Agency has contracted BBN Technologies for continued development of a disruption resistant data network.
Massachusetts-based BBN was awarded an $8.9 million DARPA contract for the development of its Disruption Tolerant Networking program. Under the phase III deal, BBN will be required to integrate the working prototype of the DTN system into fielded military networks, among other investigations.
The DTN program is part of an effort to develop a data network that can withstand interruptions like those that occur in traditional Internet Protocol suite networks. Officials say the DTN system will permit a constantly available connection.
More
here.
Hacker Breaks Into FEMA Phone System
An AP newswire article by Eileen Sullivan, via MSNBC, reports that:
A hacker broke into a Homeland Security Department telephone system over the weekend and racked up about $12,000 in calls to the Middle East and Asia.
The hacker made more than 400 calls on a Federal Emergency Management Agency voicemail system in Emmitsburg, Md., on Saturday and Sunday, according to FEMA spokesman Tom Olshanski.
FEMA is part of Homeland Security, which in 2003 put out a warning about this very vulnerability.
More
here.
U.S. Senators: FBI Rules Could Target Innocent People
An AP newswire article by Lara Jakes Jordan, via The Boston Globe, reports that:
Proposed rules to help the FBI catch terrorists could lead to innocent Americans being spied upon by government agents or informants "all without any basis for suspicion," a group of Democratic senators said Wednesday.
The rules, known as the attorney general guidelines, have not been approved or even publicly released yet, but four Democrats joined a growing chorus of lawmakers raising concerns after being briefed on what the guidelines say.
Among their fears: Americans could be targeted in part based on their race, ethnicity or religion -- or free speech activities protected by the Constitution.
More
here.
U.S. Army Cyber Ops Faces Forensic Backlog
Wyatt Kash writes on GCN.com:
As the number of potential assaults on military information technology networks continues to escalate, so does the challenge of conducting forensic and attribution analysis in order to respond appropriately, said Col. Barry Hensley at the 2008 LandWarNet conference in Fort Lauderdale, Fla., this week.
“There are 360 million scans or attempted scans [per day] across the [Defense Department] network,” said Hensley, director of the Army Global Network Operations and Security Center. But those scans are merely part of the noise that Army security specialists must deal with in analyzing a variety of incidents and potential assaults on military networks.
More
here.
Thwarting Data-Loss Via Steganography: 'Double-Stegging'
Sally Adee writes in IEEE Spectrum:
Earlier this year, someone at the United States Department of Justice smuggled sensitive financial data out of the agency by embedding the data in several image files. Defeating this exfiltration method, called steganography, has proved particularly tricky, but one engineering student has come up with a way to make espionage work against itself.
Keith Bertolino, founder of digital forensics start-up E.R. Forensics, based in West Nyack, N.Y., developed a new way of disrupting steganography last year while finishing his electrical engineering degree at Northeastern University, in Boston.
Bertolino’s method turns this technology on itself. The key to jamming steganography, he says, is using steganography—what he calls “double-stegging.” Double-stegging adds some noise, scrambling some of the image’s least-significant bits. “As long as you’re damaging at least some part of the file,” Bertolino explains, the hidden file becomes garbled and cannot be deciphered. If the cat in the picture is just a cat, the file comes to no harm. But a hidden file, once processed by the double-stegging algorithm, will yield only gibberish. “Our results are simple,” Bertolino says. “An extremely high percentage of the hidden files were destroyed.”
More
here.
Watch-Listed Fliers Can Sue, Appeals Court Rules
Ryan Singel writes on Threat Level:
Airline passengers on the government's no-fly list can sue the government to get their names removed, according to a federal appeals court ruling Monday that swept aside complicated judicial rules that insulated the government from lawsuits over the sprawling list of suspected terrorists.
The decision marks the first time that an individual has been allowed to use the court -- rather than a form mailed to a Homeland Security office -- to contest their inclusion in the nation's secret anti-terrorism database. In a recent interview, Homeland Security chief Michael Chertoff said such court reviews would destroy the watch lists and lead to another hijacking like 9/11. Those who continually run up against the list describe the experience of trying to figure out how to get off the list as Kafkaesque.
More
here.
Security Fix: Web Fraud 2.0 - Validating Your Stolen Goods
Brian Krebs writes on Security Fix:
If there is any truth to the old saying that there is no honor among thieves then it is doubly true for thieves who transact with one another yet never actually meet face-to-face. Perhaps that explains the popularity of certain services in the underground cyber crime economy that make it easy for crooks to purchase stolen credit and bank accounts in bulk and check whether the accounts are legitimate and active.
From the many hours Security Fix spent skulking around some of the more active cyber crime communities online recently, I saw a site called sh0pp0rtal.net mentioned quite a bit. I managed to acquire an account on this exclusive service, and found some 78,628 individual MasterCard and Visa credit and debit accounts for sale at various prices there.
More
here.
China Restricts Domain Registrations of Olympians' Names
An AP newswire article, via The International Herald Tribune, reports that:
China has banned the use of its Olympic gold medalists' names as Internet addresses by anyone but the athletes themselves.
The move announced Tuesday came after companies registered the names of winning Chinese athletes at the 2004 Athens Olympics as Web addresses, prompting an outcry by sports fans.
"The move will better protect the interests of the Olympic gold medalists," said an official of the government's China Internet Network Information Center, quoted by the state Xinhua News Agency. It identified him only by the surname Hu.
The Chinese government controls the awarding of Web addresses using the ".cn" suffix but has no power over those assigned in other countries.
The General Administration of Sport gave the agency a list of Chinese Olympians ahead of the games and registered all possible domain names using their names, Xinhua said.
More
here.
Note: China is setting a very good example in this case -- there are currently about
300 registered domain names that contain "Michael Phelps" in their name, and I'm quite sure that not all of them are "above-board", so to speak.
-ferg
Citizens' U.S. Border Crossings Tracked
Ellen Nakashima writes in The Washington Post:
The federal government has been using its system of border checkpoints to greatly expand a database on travelers entering the country by collecting information on all U.S. citizens crossing by land, compiling data that will be stored for 15 years and may be used in criminal and intelligence investigations.
Officials say the Border Crossing Information system, disclosed last month by the Department of Homeland Security in a Federal Register notice, is part of a broader effort to guard against terrorist threats. It also reflects the growing number of government systems containing personal information on Americans that can be shared for a broad range of law enforcement and intelligence purposes, some of which are exempt from some Privacy Act protections.
While international air passenger data has long been captured this way, Customs and Border Protection agents only this year began to log the arrivals of all U.S. citizens across land borders, through which about three-quarters of border entries occur.
More
here.
UK: Bletchley Park - A National Disgrace

Via The Independent.
Sixty-six years ago in Block B of the old Bletchley Park, a discovery was made that saved thousands of lives. A young woman, doing the filing, noticed a lot of coded messages, all concerning fuel deliveries to a small village in northern Germany called Peenemünde.
She didn't think much of them at the time. But she reported the information upwards – and the Allies stumbled on the concealed factory site where the Germans were constructing the V1 and V2 flying bombs. An air strike later and the factory was destroyed. Proof, if ever it was needed, that a well-run filing system can help win a war.
Today moss, weeds and wild flowers have taken over in Block B, a place where the course of history was changed. Nature has reclaimed its ceiling and its floor, and unless something is done soon it will either collapse or be pulled down.
Bletchley Park is one of the world's greatest and most neglected wartime monuments. But large parts of it are being left to rot. The north wall of the main building, a 19th-century country house, is now covered in scaffolding, and part of the roof is missing. The Bletchley Park Trust scraped together £100,000 to repair a quarter of the roof. The rest of the building also needs attention, but the money is not there.
More
here.
Image source: The Independent / David Sandison
Unhappy Hackers Hit Brazilian Olympic Website
Via The New Zealand Herald.
Disgruntled hackers targeted the Brazilian Olympic Committee's website to complain about the country's poor performance at the Beijing Games.
The hackers replaced regular content with criticisms of Brazilian athletes, the committee said.
"Brazil stinks in these Olympics" was one of the messages posted, according to the Universo On Line news service of the Folha de S. Paulo newspaper.
Brazil was in 39th place with one gold and five bronze medals yesterday.
The site was not operating for several hours, including during the Brazil-Argentina semifinal football match which Argentina won 3-0.
More
here.
Russian Rocket Launches New Communications Satellite
Peter B. de Selding writes on Space.com:
The third and last Inmarsat 4 mobile-broadband satellite was successfully placed into orbit Tuesday by an International Launch Services (ILS) Proton Breeze M rocket, ILS and Inmarsat announced.
The launch completed a decade-long, $1.5 billion investment by London-based Inmarsat and returned ILS to commercial service five months after a failure that forced a redesign of the Proton Breeze M upper stage.
The 13,139-pound (5,960-kg) Inmarsat 4 F3 satellite will be operated from 98 degrees west. Once its operations begin there, the two other Inmarsat 4 satellites will be moved to new orbital slots to optimize global broadband data services from the three-satellite system. Moving these two satellites will cause partial shutdowns of Inmarsat broadband services for a five-week period as the Inmarsat 4 F2 is moved from 53 degrees west to 25 degrees west, and then for a three-week period during the relocation of Inmarsat 4 F1 from 64 degrees east to 143.5 degrees east.
Operating three satellites in geostationary orbit will permit Inmarsat to offer broadband data and hand-held telephone access globally, except for the polar regions. The two previously launched Inmarsat 4 satellites, in orbit since March and November 2005, have provided services to 85 percent of the Earth's land mass but have left broad coverage gaps in the Pacific Ocean region.
More
here.
In Passing: LeRoi Moore

Internet Terrorist: Does Such A Thing Really Exist?
Rick Lawhorn writes on Help Net Security:
Recently, I have experienced an increase in organizations questioning how real is the threat of Internet terrorism and what they can do to protect themselves. As a former CISO, this was one of the last concerns that crossed my mind, especially since it was a daily up-hill battle getting buy-in for the most basic security controls and services. The notion of worrying about the potential risk of terrorism against my organization seemed to be the lowest priority given the choices at hand.
Ironically, terrorism today seems to be an emerging concern in the commercial world and many are actively pursuing methods and technology to help combat the problem. As a result, I began to research this trend to determine its drivers and potential implications to information security as we know it today.
More
here.
Note: I found this lengthy, albeit well-thought out, article on this topic very well done. Definitely worth the read. Just an FYI.
-ferg
Germans Urge Tougher Laws After New Privacy Scandal
Via Reuters.
German politicians called for tougher privacy laws on Tuesday after officials revealed personal and financial information on millions of Germans was readily available for cash on the Internet.
The scandal over the illegal trading of bank account and phone data came just months after snooping cases at some major German corporations raised alarms.
The new debate was triggered by reports that a call centre employee alerted authorities to a problem with his company's data collection practices by handing over data on some 17,000 addresses and bank account details to a privacy protection office in the northern state of Schleswig-Holstein.
Prosecutors have launched an investigation.
More
here.
China Busts Hacking Ring That Managed to Penetrate 10 Gov't Databases
Dancho Danchev writes on the ZDNet "Zero Day" Blog:
If you needed a university certificate in China during the last couple of months, there’s a big chance that a group of ten people could have supplied with you such, going a step further and adding your details in more than ten government databases across different provinces in the country, making $300k in the process.
Shanghai Daily is reporting on this sophisticated group of local hackers who were selling “valid” educational certificates by modifying government databases. How they got caught? Apparently, by cross-checking the validity of the certificate, and since they couldn’t hack each and every database in order to add a reference to it, their business model was quickly detected and shut down.
More
here.
DHS Orders Work to Stop on SBInet
Alice Lipowicz writes on FCW.com:
Under orders from the Homeland Security Department, Boeing has stopped construction of the multibillion-dollar SBInet border surveillance project along the border between Arizona and Mexico until further notice, officials from the agency and company said today.
DHS halted the work because the Customs and Border Protection agency has not received the necessary permissions from the Interior Department, said DHS spokesman Barry Morrissey.
“Because CBP does not have an agreement with the Interior Department, we cannot proceed with tower construction,” Morrissey said. “We have asked Boeing to stand down on the Arizona deployment. We cannot install sensor technology on towers that have not been built.”
Other sources close to the project said the work cannot proceed until DHS has land-use and environmental permissions from Interior.
More
here.
Judge Backs MIT Hackers in Boston Subway Dispute
A Reuters newswire article, via eWeek, reports that:
Three students from the elite Massachusetts Institute of Technology who found a way to hack into Boston's transit system to get free rides can talk publicly about the security flaw, a court ruled on Tuesday in a decision hailed as a victory for academic freedom.
The students from the university, regarded as one of the world's top science and engineering schools, raised the ire of the Massachusetts Bay Transportation Authority with a paper demonstrating how someone could work around flaws in Boston's "Charlie Card" automated fare system.
They had planned to present the paper, which showed how anyone could take thousands of free rides on subways and buses, at a hackers conference in Las Vegas this month.
The MBTA sued to block that presentation, contending that it would violate U.S. laws on computer fraud. MBTA officials said they wanted to stop the students from publicly exposing the security flaws before the transit authority had a chance to review them.
U.S. District Court Judge George O'Toole in Boston federal court found that presenting an academic paper would not violate computer fraud laws.
More
here.
Sources: Iran Tried But Failed To Launch Satellite
James Oberg writes on MSNBC.com:
Last weekend's launch of an Iranian rocket sparked days of debate over what its intended mission was — and although officials in Tehran are characterizing it as merely a test of the launch vehicle, U.S. military intelligence officials now see it as a failed attempt to put a satellite in orbit.
A defense official confirmed to NBC News on Tuesday that the Iranian attempt was being viewed as a failure, and that Iran's claims about the missile test were seen as a cover story to conceal this.
According to the Pentagon source, the Safir ("Messenger") rocket was launched just before 3 p.m. ET on Saturday from a base near Semnan in northern Iran, carrying what he called a "crude communications satellite" with only "limited capability."
Soon after reaching an altitude above 500,000 feet, the missile failed and broke apart, the source said. The missile broke up when the second stage was firing, and the resulting debris was scattered across Iran and the Gulf of Oman, he said. The rocket was apparently aiming for an orbit about 400 miles (650 kilometers) high, inclined to the equator about 62 degrees.
More
here.
Security Fix: Web Fraud 2.0: Cloaking Connections
Brian Krebs writes on Security Fix:
Even the greenest cyber crook knows you never use your own Internet connection to conduct business. In the past, masking your true Internet address online meant configuring your browser to use multiple "open proxies," connections belonging to hacked or misconfigured systems that will happily forward any Web traffic.
But why bother with that manual, labor intensive process, when you can download a tiny program and subscribe to a service that handles it for you?
More
here.
TSA Changes Course on $2B IT Contract Competition
Nick Wakeman writes on Washington Technology:
The Transportation Security Administration has changed course on its $2 billion Information Technology Infrastructure Program contract and will allow Northrop Grumman Corp. and Unisys Corp. to compete for the lucrative contract, an agency spokesman said.
The two companies filed protests with the Government Accountability Office and the Federal Aviation Administration claiming that they should not have been eliminated by TSA during a down select process.
Unisys is the incumbent on the contract, which it originally won in 2002, shortly after TSA was formed.
In late June, TSA said that Computer Sciences Corp., General Dynamics Corp. and Lockheed Martin Corp. were qualified to compete for the contract.
More
here.
Quote of The Day: Charles Cooper
"First, they decided to unleash a legal jihad. Then it was off to use technology to disrupt high-traffic networks suspected of assisting illegal digital file swapping. Now it's pushing a Orwellian agenda where it's perfectly fine to spy because it's all serving a higher good."
- Charles Cooper, writing on the C|Net "Coop's Corner" Blog on the machinations of the film and recording industry.
IOC Wants Olympic Torrents Off The Pirate Bay

Via TorrentFreak.com.
In an official letter to the Swedish Minister of Justice Beatrice Ask, the International Olympic Committee (IOC) has asked for “assistance” from the Swedish government with preventing video clips from the Olympics in Beijing to be shared on The Pirate Bay.
The Pirate Bay, however, does not plan to take anything down, and renamed their tracker to The Beijing Bay.
More
here.
Image source: TorrentFreak.com
Malicious 'Ransomware' Banner Ads Go Undetected - UPDATED
Dan Kaplan writes on SC Magazine US:
Security researchers believe a legitimate toolkit used to create Flash animation is also helping cybercriminals fashion malicious banner advertisements that scare users into believing their machines are infected with malware.
Sandi Hardmeier, author of the Spyware Sucks blog, said Sunday that some malicious ads created using Fuse Kit are able to evade detection scans run by websites or third-party ad networks. She said Newsweek.com is the latest trusted website to unknowingly host a "malvertizement."
Simply visiting a page on the Newsweek site that contains the ad will cause a warning screen to appear that falsely tells users their machine is overrun by viruses. They are prompted to pay for and install a bogus anti-virus solution.
A Newsweek spokesperson could not be reached for comment.
More
here.
UPDATE: 22:08 PDT, 18 August 2008: Alex Eckelberry
points out that those who have pointed out the
Fuse Kit may have pulled the trigger a bit prematurely. Having said that, while
Fuse may not be the source of the maliciousness, it is indeed being used for that purpose by criminals who are -- at the moment -- unknown.
-ferg
Biometric Data Obtained by DHS Analysis Tool Exempt From Some Privacy Laws
Ben Bain writes on FCW.com:
People whose biographic or biometric data is being analyzed by a new Immigration and Customs Enforcement (ICE) data system will not automatically be granted access to their records or be able to review them for accuracy as usually permitted by federal privacy protection laws.
The Homeland Security Department has decided to exempt the Immigration and Customs Enforcement Pattern Analysis and Information Collection System (ICEPIC) -- which contains data culled from numerous DHS databases -- from several Privacy Act provisions that allow individuals to access their records. DHS, ICE’s parent organization, said in a final rule for the system published today in the Federal Register that the exemptions were necessary because of “criminal, civil, and administrative enforcement requirements."
Although ICEPIC is exempt from normal record access procedures, individuals can request access from ICE, which will review requests on a case-by-case basis, according to DHS.
The information contained by ICEPIC can include names, dates of birth, phone numbers, addresses, nationalities, fingerprints, photographs, a person's immigration history and alien registration information, according to DHS. Agents and analysts can also use commercial databases to verify or resolve any gaps in ICEPIC data.
More
here.
New Unit of DIA Will Take the Offensive On Counterintelligence
Walter Pincus writes in The Washington Post:
The Defense Intelligence Agency's newly created Defense Counterintelligence and Human Intelligence Center is going to have an office authorized for the first time to carry out "strategic offensive counterintelligence operations," according to Mike Pick, who will direct the program.
Such covert offensive operations are carried out at home and abroad against people known or suspected to be foreign intelligence officers or connected to foreign intelligence or international terrorist activities -- but not against U.S. citizens, said Toby Sullivan, director of counterintelligence for James R. Clapper Jr., the undersecretary of defense for intelligence.
Sullivan and Pick, who is chief of the agency's Counterintelligence Human Intelligence Enterprise Management Office, spoke to reporters during a Pentagon briefing this month.
These sensitive, clandestine operations are "tightly controlled departmental activities run by a small group of specially selected people" within the Defense Department, said Sullivan, who exercises authority over all Pentagon counterintelligence activities. The investigative branches of the three services -- the Army's Counterintelligence Corps, the Air Force Office of Special Investigations and the Naval Criminal Investigative Service -- have done secret offensive counterintelligence operations for years, and now DIA has been given the authority.
More
here.
Privacy in an Age of Terabytes and Terror
Peter Brown writes on Scientific American:
A cold wind is blowing across the landscape of privacy. The twin imperatives of technological advancement and counterterrorism have led to dramatic and possibly irreversible changes in what people can expect to remain of private life. Nearly 10 years ago Scott McNealy of Sun Microsystems famously pronounced the death of privacy. “Get over it,” he said.
Some people, primarily those younger than about 25, claim to have done just that, embracing its antithesis, total public disclosure. And of course in many cases—determining the whereabouts of a terrorist or the carrier of a disease—public interest has an overwhelming claim on information that is usually private.
More
here.
The Web Ushers In New Weapons of War and Terrorism
Dr. Dorothy Denning writes in Scientific American:
In the early days of the Internet, optimists projected that it would usher in an era of unprecedented peace and prosperity. Maybe this will happen yet, but currently the net is proving to be a powerful tool in the hands of criminals and terrorists.
On top of the rising number of globally based online thieves bent on stealing our identities and money, a growing cadre of state and nonstate actors are adding Internet weapons to their traditional arsenals that can be unleashed in cyber attacks.
More
here.
Ireland: 20,000 Credit Cards Skimmed by Opportunistic Data Thieves
Via SiliconRepublic.com.
Opportunistic data thieves — masquerading as bank technicians — have fooled shop owners into giving them access to credit card terminals and managed to download the details of over 20,000 credit and debit cards, it emerged this morning.
The Irish Payment Services Organisation has warned that individuals pretending to be from Irish banks convinced shop owners they were carrying out maintenance on behalf of banks.
This enabled them to plug in wireless devices that pushed the data to the internet and allowed the card numbers to be used overseas.
The scam has forced banks to restrict cash withdrawals to €100 a day for card holders travelling outside the country.
More
here.
Props: Pogo Was Right
Dangerous Situation: Moscow Assists in Dismissal of South Ossetian Government

Via RIA Novosti.
South Ossetian President Eduard Kokoity has dismissed the government of the Georgian breakaway republic and proclaimed a one-month state of emergency, his spokesman said on Monday.
The decrees were signed on Sunday. The state of emergency will last until September 17.
An emergency committee is also to be set up to deal with the aftermath of Georgia's August 8 attack on the de facto independent republic, Kokoity told Russia's Vesti-24 television. The speaker of the separatist parliament, Znaur Gassiyev, has been appointed its head.
Boris Chochiev has been named as acting prime minister. Chochiev, a former South Ossetian vice-premier, will replace Yuri Morozov. The reasons for Morozov's dismissal were not specified.
More
here.
Note: This is looking very dangerous, especially given
other reports from Russian media.
-ferg
Homeland Security Officials to Scan DC Area License Plates
Via WTOP.com (AP).
Homeland security officials in the Washington area plan to dramatically expand the use of automated license plate readers to prevent possible terrorist attacks.
Officials from Maryland, Virginia and the District of Columbia have agreed to install 200 license plate readers on police vehicles, at airports and along roads. The plan announced Friday will be funded by federal homeland security grants for the area.
Britain used the readers in the 1990s to deter Irish Republican Army attacks. But in the United States, the devices have mostly been used to regulate parking or catch car thieves.
The readers will scan every license plate that passes by and will run the numbers through federal criminal and terrorist databases.
More
here.
Hactivisim: Some Russian PCs Used to Cyber Attack Georgia
Byron Acohido writes on USA Today:
Thousands of Russian supporters are volunteering their PCs to be used in cyberattacks against websites supporting the rival state of Georgia.
This new style of cyberwarfare — in which ordinary citizens instantly enlist their PCs to help bedevil the enemy — has caused little damage of substance, security experts say. But it affirms the untapped potential for using the Internet to cause mass confusion for political gain.
"This type of attack will form at least a part of all geopolitical conflicts from now on," predicts Steve Santorelli, director of investigations at research firm Team Cymru.
And also, not to be lost in this report, this:
Russian cybercrime lords are also helping out by directing parts of their vast networks of compromised PCs, called botnets, to involuntarily join the attacks. On Friday, Damballa identified a few hundred botted PCs in the U.S. attacking pro-Georgia websites.
More
here.
UK: How Big Brother Watches Your Every Move
Richard Gray writes on Telegraph.co.uk:
With every telephone call, swipe of a card and click of a mouse, information is being recorded, compiled and stored about Britain's citizens.
An investigation by The Sunday Telegraph has now uncovered just how much personal data is being collected about individuals by the Government, law enforcement agencies and private companies each day.
In one week, the average person living in Britain has 3,254 pieces of personal information stored about him or her, most of which is kept in databases for years and in some cases indefinitely.
The data include details about shopping habits, mobile phone use, emails, locations during the day, journeys and internet searches.
In many cases this information is kept by companies such as banks and shops, but in certain circumstances they can be asked to hand it over to a range of legal authorities.
More
here.
Hat-tip: PublicRadar.com
Feds Seek to Nab Credit Thieves in La., Miss.
Via KATC.com.
A ring of cyber-thieves has stolen tens of thousands of credit card numbers from Louisiana and Mississippi restaurants this year, leading to over $1 million in losses for the banks that issued them.
The restaurants began reporting the thefts beginning in March in Baton Rouge, followed by similar cases in Flowood, Miss., Lafayette, Lake Charles and West Monroe. The hackers have swiped credit and debit card numbers off 16 restaurants' computer systems, then sought to sell them for anywhere between $1 and $100 each, according to Special Agent Sean Connor of the U.S. Secret Service, an arm of the Treasury Department that investigates financial crimes.
"Once they get a big pile of credit card numbers, they turn around and sell them on the Internet," Connor said.
The cases appear connected and probably involve a criminal network that stretches overseas, which would be consistent with other identity theft cases, U.S. Attorney David Dugas said. A group indicted in a separate case earlier this month includes defendants from three continents.
Authorities have no total dollar figure for the losses sustained in the Louisiana-Mississippi cases because the victims _ local and national banks _ are still compiling figures, Connor said. The hardest hit is a bank reporting over $1.1 million in losses, he said.
More
here.
Hat-tip: Pogo Was Right