U.S. Cyber Security Review Sets Turf Battle
Siobhan Gorman writes in The Wall Street Journal:
President Barack Obama's cybersecurity review has ignited turf battles inside the White House, with economic adviser Lawrence Summers weighing in to prevent what he sees as a potential threat to economic growth, according to people familiar with the deliberations.
During the presidential campaign, Mr. Obama said he would appoint a cybersecurity adviser who would report directly to him on efforts to secure U.S. computer networks against spies, criminals and terrorists.
However, a White House review of cybersecurity policy has produced spirited debate on how high the adviser should rank and who should have veto power over his or her moves. A senior administration official called the debate an example of "creative tension," adding: "Far from being concerned about creative tension, I think this president and this team welcomes it...because, quite frankly, we've got to get this right."
Mr. Summers is arguing that his National Economic Council should "co-lead" the issue with the National Security Council, which was originally envisioned as housing the cybersecurity office, people familiar with the debate said. Mr. Summers's council, joined by the White House Office of Science and Technology Policy, worries that regulation or other limits could tie companies in red tape and hamper a recovery.
More
here.
In Passing: Jack Kemp

Image source: Center for U.S. Global Engagement
Hackers May Have Gotten to Virginia Health Professions Computers
Tammie Smith writes on The Richmond Times Dispatch:
Hackers may have infiltrated computers containing licensing information on doctors, nurses and other professions overseen by the Virginia Department of Health Professions.
By yesterday afternoon, all 36 computer servers storing the state agency's records were shut down after a midday message popped up on some computer screens that implied the system was being hacked.
The situation was being investigated as a security breach and possible criminal matter.
"Part of the system may have been hacked," said Sandra Whitley Ryals, director of the state agency that oversees licensing of health professionals, including doctors, nurses, dentists, funeral directors, physical therapists, social workers and others.
"We are trying to verify that. That is why the precautionary measure was done to shut the entire system down."
Ryals said they have no reason at this point to think the problem went beyond one server on which the initial message came up.
That shutdown meant employees could not send or receive e-mail or use their Web browsers, and for a time some telephones were not working.
More
here.
Experts: Cyber Chief Needs To Be In White House
Diane Bartz writes for Reuters:
The cybersecurity chief named to battle Internet viruses and larger challenges facing the information technology networks used by U.S. companies and national defense should be based in the White House, experts told a congressional panel on Friday.
Cybersecurity is important enough to warrant a White House staffer with real authority and a real budget, said Larry Clinton, president of the Internet Security Alliance and one of those who made recommendations to the Obama team.
"It can't be just a figurehead," he told an Energy and Commerce subcommittee. "We tend to think it should be somewhere in the White House structure."
No date has been set for when, or if, such an appointment would be made.
More
here.
Two Brothers Among Indictees in $4M Spam Case
Jaikumar Vijayan writes on ComputerWorld:
Two Missouri men who made over $4 million pitching and selling everything from electronics to teeth whiteners to students in more than 2000 colleges and universities have been indicted by a federal grand jury on a variety of e-mail spamming and related charges.
Amir Ahmad Shah, 28, of St. Louis, and his brother, Osmaan Ahmad Shah, 25, of Columbia, Mo., were charged in a 51-count sealed indictment by a federal grand jury on April 23. Also indicted in the nationwide spamming case were Liu Guan Ming, a Chinese citizen, Paul Zucker, a 55-year-old from Wayne N.J, and I20 Inc., the company owned by the Shah brothers.
According to the indictment papers, the spam e-mail scheme affected virtually every college and university in the country. It began around 2001 with the Shah brothers allegedly using e-mail extracting programs to harvest e-mail addresses from colleges and universities around the country which they then used to send targeted spam e-mails pitching various products.
More
here.
LexisNexis Warns of Possible Data Breach
An AP newswire article by Amy Westfeldt, via MSNBC, reports that:
The LexisNexis online information service is warning 32,000 people their personal information may have been improperly accessed in a credit card fraud scheme that postal officials say bilked hundreds.
New York-based LexisNexis says in a letter mailed Friday that former customers of the service may have viewed information including names, birth dates and Social Security numbers.
U.S. Postal Service officials have launched a criminal investigation and say 300 people in the databases of LexisNexis and a Santa Fe, N.M., company called Investigative Professionals were victims in the credit card fraud scheme. No suspects have been arrested.
Link.
Gunter Ollmann: A Botnet by Any Other Name
Gunter Ollmann writes on SecurityFocus:
The news has been awash the last few weeks with fears over globe-spanning botnets and their criminal intent: Conficker managed to hog the limelight for well over a month, and then came Finjan's disclosure of a previously unknown — and currently unnamed — botnet consisting of some 1.9 million malicious agents.
All this attention underscores a increasingly significant problem for botnet researchers: how precisely should botnets be usefully named?
It's not an easy problem to solve. The antivirus industry has had decades to reach a consensus for naming new malware, yet it has failed to do so. Such a track record does not build confidence for botnet naming. Despite botnets not being the same as viruses the historical process has been to name a botnet after the primary malware discovery, and this approach is already proving to be an increasingly redundant convention.
More
here.
Quote of The Day: Bruce Schneier
"Nuclear war is not a suitable response to a cyberattack."
- Bruce Schneier, commenting on yet another New York Times "Cyberwar" article.
Experts Chart Spike in Cyber Sieges
Brian Krebs writes in The Washington Post:
Cyber attacks with enough firepower to knock entire countries off the Internet have spiked in recent months, raising fresh concerns within the security community about weaknesses in the Internet infrastructure that help create such weapons of mass disruption.
These "distributed denial of service" or DDoS attacks use robot networks or "botnets" -- many hundreds or thousands of compromised PCs -- to flood targets with so much junk traffic that they can no longer accommodate legitimate visitors.
While DDoS attacks have been a common threat since the dawn of the commercial Internet, DDoS watchers, such as Arbor Networks, have tracked a recent spike in the number, sophistication and size of attacks against major Internet providers. Attackers also appear to be picking bigger targets.
"We've certainly seen in last 120 days an uptick in critical infrastructure impacting attacks," said Danny McPherson, Arbor's chief security officer. "Suffice it to say, 'interesting' activity in this area has indeed increased from our perspective over the past 6 months or so, and the virulence of infrastructure attacks continues to be evident."
More
here.
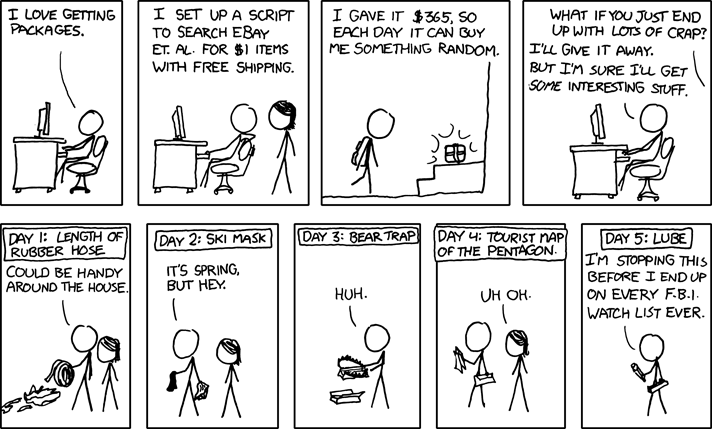
Classic xkcd: Packages
Click for larger image.
We love
xkcd.
- ferg
Sri Lankan Army Says Its Website Hacked by LTTE
Via The Hindustan Times.
The Tamil Tigers on Friday took their war into the cyberspace by hacking the official website of the Sri Lankan army.
The Webmaster of the Army called the attack a desperate bid by the LTTE propagandists to hold the truth on humanitarian mission being revealed to the world. He said measures are being taken to restore the website soon.
"LTTE propagandists have been extensively using the Internet as a platform to launch their misinformation, and disinformation campaigns against Sri Lanka since 1997," the ministry said.
More here.
Russian Military Launches New Surveillance Satellite
Via Space.com.
Russia launched a Soyuz rocket Wednesday carrying a covert military payload believed to be a spy satellite with a high-resolution optical camera.
The Soyuz rocket lifted off at 1658 GMT from the Plesetsk Cosmodrome in northern Russia, according to Roscosmos, the Russian space agency.
The launcher reached orbit and deployed the spacecraft about eight minutes later, the Itar-Tass news agency reported.
Russian military officials said the craft would be named Kosmos 2450, fitting with the defense ministry's nomenclature for military satellites.
Tracking data indicate Kosmos 2450 is in an orbit with a high point of about 208 miles and a low point of about 105 miles. The orbital inclination was reported as 67.1 degrees.
Analysts believe Kosmos 2450 is a Kobalt-class satellite with retrievable film canisters that can return imagery to Earth through a mission lasting at least several months.
More
here.
EU: Batten Down the Cyber-Hatches
Via The Economist.
Over the past ten years the European Union has failed to protect the continent’s energy security. Will it do any better when it comes to cyber-security?
At an EU conference on that subject in Tallinn on April 27th, participants wrestled with the need to act and the difficulty of deciding what exactly to do. The location was a suitable one: Estonia is the only EU member state to have suffered a full-scale cyber-attack, in April 2007. Amid a furious row with Russia about the relocation of a Soviet-era war memorial, a flood of bogus internet traffic disabled the country’s main websites, briefly shutting down vital public services and crippling businesses such as online banking.
Yet two years later, the EU and its member states are still wrestling with the issue. Knowing whether such attacks come from pranksters, hooligans, terrorists, criminals or an unfriendly government is difficult—sometimes impossible. But the potential damage is clear: everything from water and electric power to financial industries and retail distribution depends on the internet. The right combination of malicious code, stolen or hacked passwords and a badly designed system could mean catastrophe.
More
here.
The EFF Digs Deep Into The FBI's 'Everything Bucket'
Jon Stokes writes on ARS Technica:
Earlier this week, the EFF published a new report detailing the FBI's Investigative Data Warehouse, which appears to be something like a combination of Google and a university's slightly out-of-date custom card catalog with a front-end written for Windows 2000 that uses cartoon icons that some work-study student made in Microsoft Paint. I guess I'm supposed to fear the IDW as an invasion of privacy, and indeed I do, but given the report's description of it and my experiences with the internal-facing software products of large, sprawling, unaccountable bureaucracies, I mostly just fear for our collective safety.
The idea behind the system, which the FBI has been working on since at least 2002, is that the Bureau can dump all of its information in there so that it can be easily searched and shared. IDW contains more documents than the library of congress—a stew of TIFFs with OCRed text, multiple Oracle databases, news streamed in from the Internet, reports and records in various in-house data formats, watch lists, telephone data, and an alphabet soup of smaller databases and records repositories—all accessible as one sprawling system that processes batch jobs, runs queries, and issues alerts. In short, the IDW is an "everything bucket" for the FBI.
Complicating the picture is the fact that some parts of the system are classified as "secret," while others aren't. I'm sure the entire thing is a joy to use.
More
here.
Yet Another Case of Bad Password Management: Twitter Employee Account Hijacked
Thomas Claburn writes on InformationWeek:
Another Twitter administrative account has been compromised, apparently as a result of the same weakness in the Yahoo Mail password-recovery system that allowed someone to hijack Alaska Gov. Sarah Palin's e-mail account last year.
Three days ago, Jason Goldman, a product manager at Twitter, posted that his Yahoo Mail account had been hacked.
On Wednesday evening, someone going by the name "Hacker Croll" posted 13 screenshots of Twitter's administrative console at several Web sites. One screenshot shows administrative information about Barack Obama's Twitter account. Another shows information about Britney Spears' account.
Over several posts, "Croll" explains that one of Twitter's administrators has a Yahoo account and that he or she reset the password by answering to the secret question. Croll adds that the mailbox contained a message with the Twitter account's password.
A Twitter spokesperson did not immediately respond to an e-mailed request to confirm that Goldman's account was compromised. Calls to the company headquarters in San Francisco went unanswered.
More
here.
SCADA Watch: Critics Say Bill to Protect Electric Grid from Cyber Attacks Lacks Teeth
Jill R. Aitoro writes on NextGov.com:
A bill [.pdf] expected to be introduced in the House and Senate this week would help protect the computers that control the country's power grid, but it does not go far enough, security experts said on Wednesday.
The legislation would give federal regulatory agencies more power, but would not prompt owners and operators of electrical facilities to do their part to enhance cybersecurity, critics said. The bill also should be expanded to address other components of the nation's critical infrastructure, such as transportation and water, they added.
The measure -- which represents a joint effort by Senate Homeland Security and Governmental Affairs Chairman Joseph Lieberman, I-Conn., and House Homeland Security Chairman Bennie Thompson, D-Miss. -- would amend the 1935 Federal Power Act to provide "additional legal authorities to adequately protect the critical electric infrastructure against cyberattack." It would require the Federal Energy Regulatory Commission, which administers security standards for most of the nation's power plants, to establish within 120 days of its enactment interim cybersecurity standards to replace existing guidelines deemed inadequate.
The legislative effort follows a report earlier this month that intelligence officials discovered malicious software on computers that control the nation's power grid.
More
here.
Pentagon Sharing Classified Cyber Threat Intelligence With Companies
Shane Harris writes in The National Journal:
In response to an unprecedented wave of attacks on the Defense Department's computer networks, and possible theft of information about U.S. weapons systems by foreign governments, the Pentagon has quietly begun sharing classified intelligence about hackers and online threats with the country's biggest defense contractors. The intelligence-sharing program began almost two years ago, after top Pentagon leaders realized that hackers were trying to steal information not just by breaking into government computers but also by going after corporations that contract with the government. These private computers and networks often contain the same sensitive and classified information found in the government's systems.
The new intelligence partnership, which has not been previously reported, is known as the Defense Industrial Base initiative, or "the DIB." The department formally launched the program in September 2007, but it took a year to work out a legal arrangement by which the contractors and the government could confidentially share information. In mid-2008, the effort ramped up after what was described as a hair-raising meeting in a secured facility at the Pentagon in which officials gave temporary security clearances to chief executives from the biggest defense firms and delivered a no-holds-barred briefing on the range of successful cyberattacks launched against the government and their companies. The executives "went in with dark hair and came out with white hair," said James Lewis, a prominent cyber-security expert and a fellow at the Center for Strategic and International Studies, who is familiar with the meeting. "I think that was a shocker for most people."
More
here.
Mark Fiore: Taliban Fever

More Mark Fiore brilliance.
Via The San Francisco Chronicle.
- ferg
Report: U.S. Cyber Warfare Needs Oversight
An AP newswire article by Lolita C. Baldor, via The Army Times, reports that:
Shrouded in secrecy, the U.S. government’s policies on how and when to wage cyber warfare are ill-formed, lack adequate oversight and require a broad public debate, a new report by the National Research Council says.
The report warns that the “undeveloped and uncertain nature” of the government’s cyber warfare policies could lead to them being used hastily and ill-advisedly during a crisis. That danger is compounded by secrecy and lack of oversight, the report’s authors cautioned on Wednesday.
“Unsound policy formulated and implemented during crisis may prove difficult to change or reverse when the crisis has passed,” concludes the report, the first to take a comprehensive look at American cyber war capabilities. The research council is the working arm of the National Academy of Sciences.
The U.S. government has spoken only broadly about cyber warfare in the past, noting its value as a national security tool. Officials routinely refuse to talk about computer attacks America has launched.
More
here.
PCI’s Grading System Is Failing
David Taylor writes on StorefrontBacktalk:
For months, retailers and Congress have been attacking retail security standards, but few realize that the problem is not in the standard itself. The problem is a grading system that causes most retailers to be out of compliance most of the time because the rules require 100 percent compliance. How often in school did you score 100 percent?
The system is oriented to forcing retailers to fail and it does this by being utterly insensitive to risk, which is surprising because the financial services industry runs on risk management. So if big finance runs on risk management, why are retail payment security rules running away from it?
At the recent Electronic Transactions Association (ETA) conference, Visa and MasterCard executives again defended the standard against industry and government criticisms that the standard is insufficient to prevent breaches. They cited instances where merchants (e.g., Hannaford) and processors (e.g., Heartland) who claimed to be PCI compliant were actually not compliant during the extended period of time during which the breach occurred. That happened because, from a technical perspective, “companies can fall in and out of compliance,” and because sometimes “the PCI assessment is not comprehensive enough,” according to the executives. From these statements, it sounds like the blame for why a “compliant” company can get breached is due to either technology or the assessors. But I maintain that the culprit in all of this is the grading system used to measure PCI compliance, and it’s time for a change.
More
here.
Hacker Behind P2P Botnet Gets No Jail Time
Dan Goodin writes on The Register:
A hacker who confessed he created one of the world's first botnets to use peer-to-peer technology won't spend any time in prison because of the assistance he's provided to prosecutors.
Jason Michael Milmont, 20, of Cheyenne, Wyoming, was sentenced on Tuesday to five years of supervised probation and a year of home confinement. US District Judge William Downes of Casper, Wyoming also ordered him to pay almost $37,000 in restitution. The relatively lenient sentence - he faced a maximum five years in federal prison and a $250,000 fine - came in exchange for help he's provided prosecutors since pleading guilty.
"This young man has quite a bit of talent and we asked that he turn that talent toward good," said John Powell, a spokesman for the US Attorney's office in Cheyenne. "He's helped us somewhat toward that."
Last year, Milmont admitted to creating the so-called Nugache Worm, which spawned one of the first botnets to use a decentralized system to send instructions to drones, according to security researcher Dave Dittrich. The peer-to-peer mechanism was considered a break-through because it eliminated the need for a single master control channel. That made it much harder to shut down the botnet.
More
here.
U.S. Cyber-Security 'Embarrassing'
Maggie Shiels writes for The BBC:
America's cyber-security has been described as "broken" by one industry expert and as "childlike" by another.
The criticism comes as President Obama prepares to release the results of a review he had ordered.
Tim Mather, chief strategist for security firm RSA, told BBC News: "The approach we have relied on for years has effectively run out of steam."
Alan Paller from security research firm SANS Institute said the government's cyber defences were "embarrassing".
The government review, which will outline a way forward, is expected to be opened up for public comment at the end of this month.
More
here.
Obama's First 100 Days 'Blank' on Eastern Europe
Via EU Observer.
As US President Barack Obama marks his 100th day in office on Wednesday, several blanks in his policies towards eastern Europe and Russia still need to be filled, experts on transatlantic affairs told this website.
Mr Obama, who has travelled to Europe and met all the bloc's leaders, as well as his Russian counterpart, Dmitry Medvedev, has provided a sharp change of style compared to his predecessor's approach, yet his policies towards this part of the world so far have remained vague.
On eastern Europe, the policies are "blank" and no particular statements were made on the situation in Ukraine, Georgia or recently Moldova, Michael Emerson from the Centre for European Policy Studies, a centre-right Brussels-based think tank told this website.
"Some people speculate that Mr Obama is not interested in the region and will leave it to Russia and the EU to sort it out. I wouldn't say that. We will have to see, as his administration is not fully staffed yet," he said.
More
here.
'Hackers Wanted' Ad Fed Security Misconception
Ira Winkler writes on IT World:
I should never be surprised at things related to government security efforts, but I did think the concept of hiring hackers was pretty much dead in government circles. Then comes the recent headline, " U.S. Looks to Hackers to Protect Cyber Networks." Frankly, I think it set the security profession back at least three years.
The story, widely quoted throughout the U.S. and the world, makes people think that hackers are superior to the best security professionals. Now, admittedly, recent stories have made it appear that the government's security efforts are poor at best. We've had foreign intelligence agencies infiltrating the power grid, and The Wall Street Journal recently reported that the F-35 designs have been hacked for years. All of that is something to ponder. But hiring hackers to fix security breaches? Hackers are not security experts. A recent, and most telling, survey from Verizon basically found that hackers' skills reside in the ability to exploit very basic mistakes on the part of their victims.
Some people will contend that this is all a misunderstanding, because "hackers" are not computer criminals by definition. Criminals are "crackers," they will point out. Others will say that the story used the word "hackers" for sensationalist purposes and that the workers actually being sought were people to perform professional penetration tests. There's some truth to that argument, but there's no mistaking the article's implication that hackers are criminals. To quote from the introduction, "Federal authorities are looking for hackers -- not to prosecute them, but to pay them to secure the nation's networks."
It's one thing for moronic CEOs of small companies such as exqSoft Solutions to hire the Twitter hacker for the publicity, but the U.S. government and General Dynamics, its proxy in this case, should know better. And it could be that this ad was just a misstep. But it was a misstep with unfortunate consequences.
More
here.
UK: Home Office 'Colluded With Phorm'
Via The BBC.
The Home Office has been accused of colluding with online ad firm Phorm on "informal guidance" to the public on whether the company's service is legal.
E-mails between the ministry and Phorm show the department asking if the firm would be "comforted" by its position.
The messages show Phorm making changes to the guidance sought by the ministry.
Lib Dem Home Affairs spokeswoman Baroness Sue Miller, who has questioned the Home Office about Phorm, said the e-mails were "jaw dropping".
No-one from the Home Office was immediately available for comment.
More
here.
Adobe Investigating New Vulnerabilities in Reader
Larry Seltzer writes on eWeek:
Adobe says they are investigating reports of a new vulnerability in their PDF Reader program.
The Adobe report refers to a single vulnerability report on SecurityFocus, but in fact there are two similar reports there, both credited to "Arr1val." Both include proof of concept Javascript code.
Both vulnerabilities are reported as affecting Adobe Acrobat Reader 8.1.4 and 9.1. Arr1val tested them on Linux, not other platforms, but it's highly plausible, based on the reports and the proof of concept code that they are portable to other operating systems. The actual exploits, which call shell code, are not likely as portable, as the details of an exploit are often platform-specific.
More
here.
Proposal Would Shore Up Government Cyber Defenses
Brian Krebs writes on Security Fix:
While cyber attacks have evolved dramatically since the beginning of this decade, the regulations governing how federal agencies defend against digital intruders haven't been updated since 2002. Legislation expected to be introduced Tuesday in the Senate would seek to correct that imbalance.
The "U.S. Information and Communications Enhancement Act of 2009," which would update the Federal Information Security Management Act, or FISMA, calls for the creation of hacker squads to test the defenses of federal agency networks. In addition, agencies would be required to show that they can effectively detect and respond to the latest cyber attacks on their information systems.
Critics of the current law say it merely requires agencies to show they have the proper cyber security policies in place, but not necessarily demonstrate that those policies are helping to block or mitigate real-world attacks.
"Only about five federal agencies are testing to see whether they are actually implementing these requirements," said Alan Paller, director of research for the SANS Institute, a security training group based in Bethesda, Md. "Agencies need to be measured on how well they block known attacks, and that's the opposite of what they're measured against now, which is how secure they are on paper."
More
here.
Firefox 3.0.10 Now Available
Get it.
Fixed in Firefox 3.0.10:
MFSA 2009-23 Crash in nsTextFrame::ClearTextRun()
- ferg
Classic xkcd: Swine Flu
Click for larger image.
We love
xkcd.
Enjoy!
- ferg