Los Angeles: Video Cameras Urged to Monitor the Police
Patrick McGreevy and Richard Winton write in The Los Angeles Times:
Alarmed by a number of incidents involving police abuse allegations, civil rights groups called Friday for the Los Angeles Police Department to install surveillance cameras in all police stations and to expedite putting the devices in all patrol cars.
LAPD officials said they were taking steps to carry out that task.
It was a video surveillance camera installed in the Central Division station that captured images of an officer allegedly assaulting a 16-year-old detainee while the youth was handcuffed this week, leading Police Chief William J. Bratton on Thursday to announce the officer's arrest.
However, LAPD officials acknowledged Friday that video surveillance systems have not been installed in several police stations and that the city is just beginning to test putting cameras in patrol cars. The Los Angeles County Sheriff's Department does not have video cameras in its patrol cars either, a representative said.
More
here.
Toon: Those Evil Video Games
Click for larger image.
VCU Mistakenly Divulges Student Personal Information, Grades
Gary Robertson writes in The Richmond Times-Dispatch:
For the second time this year, the personal information and Social Security numbers of hundreds of Virginia Commonwealth University students have been compromised.
According to the university's technology services Web site, personal information on 561 VCU students in the College of Humanities and Sciences was inadvertently included in two attachments in an e-mail.
The information included names, Social Security numbers, local and permanent addresses and grade-point averages.
The e-mail was sent Nov. 20 to 195 students to inform them about their eligibility for scholarships from Phi Kappa Phi, a national honor society. They were part of the larger group of 561 students whose personal information was released, according to the university.
More
here.
(
Props, Pogo Was Right.)
Fox, Viacom, CBS and NBC discuss YouTube Rival
From the "How do we cash in on that?!?" Department:
This is just about the most retarded thing I've ever heard of... Don't the big media companies get it?
Via Reuters.
News Corp.'s Fox, Viacom Inc., CBS Corp.. and NBC Universal are in talks about creating a video Web site to compete with Google Inc.'s YouTube, the Wall Street Journal reported on Friday.
While a deal is still far off, the four media companies envision a jointly owned site that would be the primary Web source for videos from their television networks, the paper said in an online report on wsj.com, citing people close to the situation.
The companies aim to cash in on the fast-growing market of Web video advertising and have also discussed building a Web video player that could play clips, the Journal said.
More
here.
Traveler Data Program Defied Ban, Critics Say
Spencer S. Hsu and Ellen Nakashima writes in The Washington Post:
The Department of Homeland Security violated a congressional funding ban when it continued to develop a computerized program that creates risk assessments of travelers entering and leaving the United States, according to lawmakers and privacy advocates.
Although congressional testimony shows that department officials apparently disclosed some important elements of the controversial Automated Targeting System program to lawmakers in recent months, several key members of Congress said that they were in the dark about the program and that it violated their intentions.
More
here.
Local: Oakland Student Raped After Answering Craigslist Ad
An AP newswire article, via CBS5.com, reports that:
An Alameda man is under arrest for allegedly raping a graduate student who answered a classified ad on a popular Web site.
Police say a 31-year-old student at Mills College in Oakland was raped Thursday night after answering an ad on Craigslist offering modelling jobs.
49-year-old Gregory Hayes was picked up by police Friday morning after the woman spotted him at a gas station near campus.
More
here.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Friday, Dec. 8, 2006, at least 2,928 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,356 died as a result of hostile action, according to the military's numbers.
The AP count is three higher than the Defense Department's tally, last updated Friday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casuality Count website
here.
Health Providers' Social Security Numbers Posted on Vermont State Website
An AP newswire article by David Gram, via The Boston Globe, reports that:
At least several hundred, likely more, Social Security numbers of health care providers were posted to the Internet in a state contractor's mistake that officials were scrambling to fix Friday.
Human Resources Commissioner Linda McIntire said the names and Social Security numbers of doctors, psychologists and others were posted on a Web site where the state had posted a request for bids by contractors to be the state's health insurance administrator.
More
here.
The Lowdown on the Sex.com Case
Kieren McCarthy writes on his blog:
Sex.com thief released from prison -- and his Mexican lawyer shot the next day.
In yet another twist in the extraordinary tale of Sex.com, the con-man who stole the world’s most valuable domain has been released from jail - in order to locate the millions of dollars he owes the original owner.
Stephen Michael Cohen has been ordered to hand Gary Kremen $65 million by a US court but despite years of intense fighting has yet to hand over one cent. On Tuesday morning, after 14 months in jail for civil contempt, Cohen was released by Judge James Ware because Kremen’s lawyers had been unable to chase down his offshore bank accounts.
Cohen claims he is only able to get the details of his various accounts - held in Lithuania, Liechtenstein and the Isle of Man - in person and outside jail, and is due back in court in San Jose on 26 February to tell the judge how that search has gone.
Kudos, Kieren.
Much more
here.
Cisco Urges FCC to Break Gridlock on AT&T-Bellsouth Merger
Mark Sullivan writes on Light Reading:
Cisco Systems Inc. today filed a letter with the Federal Communications Commission (FCC) asking it to hurry up and approve the merger of AT&T Inc. and BellSouth Corp.
Cisco, in its first comment to the FCC on the subject, says that the delay is hurting equipment manufacturers.
More
here.
BREAKING UPDATE: Via the
Associated Press, "The Federal Communications Commission's top lawyer on Friday authorized a commission member to vote on the proposed buyout of BellSouth Corp. by AT&T Inc., despite an apparent conflict of interest. The move could break a deadlock on the deal."
Full story
here.
California AG Attempting Deal Between HP, Pretext Victims
K.C. Jones writes on InformationWeek:
California Attorney General Bill Lockyer is working to settle any victims' claims arising from Hewlett-Packard's probe into media leaks, which involved pretexting, or deception, to obtain phone records.
Lockyer's office confirmed Friday that the attorney general planned to meet with journalists and others whose phone records were accessed as part of HP's investigation. Lockyer hopes to help broker a settlement between victims and the company accused of violating their privacy.
More
here.
Senate Passage Of Phone Records Privacy Bill Likely - UPDATE
K.C. Jones writes on InformationWeek:
Buying, selling, or obtaining phone records without a customer's permission could become a felony if no one in the U.S. Senate objects to a bill that lawmakers have put on a fast track for passage.
The bill, the Telephone Records and Privacy Protection Act of 2006, could pass Friday or in the early morning hours Saturday, when observers expect the Senate to wrap up business for the year. Senate staffers said Thursday their chamber had hot-lined the so-called "pretexting" bill, which passed the U.S. House of Representatives on April 25. That means if no one objects before the close of session, the technology-neutral bill will pass the Senate by unanimous consent.
More
here.
UPADTE 12/8 21:57 PST: It has passed Senate vote.
Fate of Net Neutrality Has Now Been Passed On to a More Internet-Friendly 110th U.S. Congress
Via SaveTheInternet.com.
The gavel has fallen on the 109th Congress marking the demise of entrenched corporate efforts to legislate away our Internet freedoms — and a stunning victory for real people who want to retain control of the Internet.
The fate of Net Neutrality has now been passed to what appears to be a more Web-friendly Congress. Our Coalition pledges to work with new Members to craft policies that ensure all Americans can access the Internet and enjoy the unlimited choices it has to offer.
Companies like AT&T, Verizon, BellSouth and Comcast spent more than $150 million to push Congress to gut Net Neutrality.
More
here.
Alabama Computer Forensics Duo Cracks High-Profile Hacker Attacks
A Mobile (Alabama) Press-Register article by David Ferrara, via Ledger-Inquirer.com, reports that:
Gus Dimitrelos and Kevin Levy, of the Alabama Computer Forensics Laboratory in Spanish Fort, cracked one of the year's most high-profile identity theft cases. The team, paid for with federal funds administered by the state of Alabama, works with prosecutors and police to solve crimes.
In September, they began tracking down the woman who had hacked her way into the computer and phone records of Chester Bennington - the frontman for the band Linkin Park - and wife Talinda, Dimitrelos said.
More
here.
(
Props, Flying Hamster.)
How to Help the James Kim Family
Jai Singh writes on C|Net News:
To our readers:
For the last several days, thousands of you have sent condolences and shared your feelings over the tragic loss of CNET Senior Editor James Kim. Your outpouring of support has been overwhelming.
We at CNET would like to extend our heartfelt thanks to all of you around the globe who wrote in. Your expressions of goodwill have been comforting through this difficult time.
If you wish to write to the Kim family directly, you can do so at JamesandKati.com. Many of you have also expressed a desire to make donations. The Kim family is working on setting up an official fund. In the meantime, you can make out checks to "The James Kim Memorial Fund" and mail it to this address:
The Kim Family
c/o CNET Networks
235 2nd Street
San Francisco, CA 94105
Sincerely,
Jai Singh
Editor in chief and senior vice president, CNET
More
here.
Gapingvoid: Barriers to Entry
Via gapingvoid.com. Enjoy!
ComScore Networks: The Big Brother of the Internet?
Lisa Lerer writes on Forbes.com:
ComScore Networks is the Big Brother of the Internet. The widely-used online research company takes virtual photos of every Web page viewed by its 1 million participants, even transactions completed in secure sessions, like shopping or online checking. Then comScore aggregates the information into market analysis for its over 500 clients, including such large companies as Ford Motor, Microsoft and The New York Times Co.
ComScore says that its participants are willing exhibitionists, happily selling their online privacy for gift certificates and free screensavers. But two computer scientists are raising new questions about comScore, claiming that company tracking software is being installed without consent on an unknown number of computers.
More
here.
Security-Conscious NASA Tightens e-Mail Policy - UPDATE
Alan Boyle writes for MSNBC:
Even as it prepares for its first nighttime shuttle launch in four years, NASA has clamped down on its computer network policies, due to security concerns raised about documents sent as e-mail attachments.
Shuttle planners were reportedly adjusting their e-mail routines to accommodate the new network limits, and the policy change wasn't expected to impact plans to launch the shuttle Discovery on its 12-day mission to the international space station. Liftoff is scheduled at 9:35 p.m. ET Thursday, although unacceptable weather conditions could force a postponement.
Representatives at NASA Headquarters told MSNBC.com on Thursday that the new limits would block the receipt of Microsoft Word documents coming in to the space agency's core computer network as e-mail attachments.
More
here.
UPDATE 12/8 13:11 PST: Perhaps it's because of
this?
ICANN Approves .ASIA TLD
Ed Sutherland writes on internetnews.com:
In a move reflecting the growing Asian flavor of the Internet, the Internet Corporation for Assigned Names and Numbers (ICANN) yesterday approved the first top-level domain registry based in the Asia-Pacific region.
The .asia top-level domain will join other Asian-Pacific Internet domains, such as Japan, China, and South Korea already managed by DotAsia Organization. The addition brings the total number of Internet domain suffixes to 266.
Despite the fact that more than 64 percent of Internet users coming from non-English-speaking countries and Asian speakers comprise 33 percent of the online population, only 11 percent of .com or .net registrations come from Asia, argued the Hong Kong-based DotAsia.
More
here.
Internet Gangs Hire Students for Cybercrime
Peter Griffiths writes for Reuters:
Organized gangs have adopted "KGB-style" tactics to hire high-flying computer students to commit Internet crime, a report said on Friday.
Criminals are targeting universities, computer clubs and online forums to find undergraduates, according to Internet security firm McAfee.
Some gangs have sponsored promising students from other disciplines to attend computer courses before planting them in businesses as "sleepers".
McAfee said the students write computer viruses, commit identity theft and launder money in a multi-billion dollar industry that is more lucrative than the drugs trade.
The gangs' tactics echo the way Russian agents sought out experts at trade conferences or universities during the Cold War, the company said in an annual report.
More
here.
Quote of the Day [2]: Marion Ashley
"We feel like the IRS is the Grinch that stole Christmas."
- Riverside County Supervisor Marion Ashley, reacting to the shocking news that the more than $1 million donated after an arson blaze killed five firefighters can't be distributed to their families because the charity didn't follow IRS rules.
Botnet Infected User's PC Results In Armed Police Raid
Via ABC 7 News (Denver).
A Denver woman who didn't have adequate security on her home computer paid the price.
Serry Winkler was visited by several officers with a search warrant who demanded that she turn over her computer.
They were investigating a case of computer fraud. The woman's computer was apparently infected by a bot or robot.
Investigators said someone hacked into Winkler's computer, stole her IP address and used it with a stolen credit card to make fraudulent purchases online. Police said they were trying to get to the bottom of it.
More
here.
Toon: Isolated
Click for larger image.
Quote of the Day: Michelle Quinn
"The best of technology couldn't find James Kim in time.
"It hurts. Our personal technology makes us feel all knowing, invincible, able to navigate the world beyond the limits of our immediate knowledge and surroundings. We can sit in San Jose and find the coolest spot to spend the night on the Oregon coast or the best sushi place in Abidjan, Ivory Coast. We see a traffic accident on 880 and dial up the CHP.
"But in the end, despite our iPods and Blackberries, we are really just ticking clocks that wind down without food, water, shelter."
- Michelle Quinn, in a Mercury News article entitled "Kim's Death Underscores Limits of Technology."
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Thursday, Dec. 7, 2006, at least 2,922 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,339 died as a result of hostile action, according to the military's numbers.
The AP count is 14 higher than the Defense Department's tally, last updated Thursday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casuality Count website
here.
Florida Botmaster Pleads Guilty in DDoS Attack
Linda Rosencrance writes on ComputerWorld:
A 32-year-old Florida man pleaded guilty yesterday in federal court to hacking into computer systems at two major universities as part of plot to launch a distributed denial-of-service (DDoS) attack on computer servers managed by Akamai Technologies, according to the U.S. attorney's office in Boston.
John Bombard, 32, of Seminole, Fla., pleaded guilty before U.S. District Judge Patti Saris in the U.S. District Court for the District of Massachusetts to two counts of intentionally accessing a protected computer without authorization.
Bombard will be sentenced on March 7. He faces up to two years in prison, to be followed by one year of supervised release, and a $100,000 fine.
Officials from Cambridge, Mass.-based Akamai could not be reached for comment. The company distributes online content and business processes over a network of computer servers.
More
here.
ICANN Reviews Revoking Outdated Suffixes
An AP newswire article by Anick Jesdanun, via PhysOrg.com, reports that:
Over the past few years, the Internet has seen new domain names such as ".eu" for Europe and ".travel" for the travel industry. Now, the key oversight agency is looking to get rid of some.
Meeting in Sao Paulo, Brazil, the Internet Corporation for Assigned Names and Numbers began accepting public comments this week on how best to revoke outdated suffixes, primarily assigned to countries that no longer exist.
More
here.
Patented: Network Access Control Technology
Sean Michael Kerner writes on internetnews.com:
Network Access Control (commonly referred to as NAC) is one of the hottest trends in networking. Although Cisco helped popularize the term (or at least an implementation of NAC), another company just snapped up a patent for it.
Mirage Networks has been awarded US Patent #7,124,197 for its NAC technology.
The official title, according to the U.S. Patent and Trademark office, is "Security apparatus and method for local area networks." The invention "includes a method and apparatus for controlling data link layer access to protected servers on a computer network by a client device."
Grant Hartline, CTO for Mirage Networks, told internetnews.com that the patent embraces a peer-based model, but does not dictate one. "In the world of IPv4, this would cover approaches like ARP (Address Resolution Protocol), which is used in the example shown in the patent," Hartline said. "The methodology in the patent could also include the use of DHCP."
More
here.
...And if You Though RFID was Dangerous Before, This Should Make You Think...
Via Beverage Daily.
Crown and QinetiQ are jointly developing radio-frequency identification (RFID) tracking that will turn metal packaging into an antenna and help reduce the costs of using the technology.
The two announced the partnership this week saying the development will solve problems with reading RFID tags attached to metal containers and cut the costs of using the technology. The technology will allow processors to integrate ultra high frequency (UHF) RFID tags into metal packaging at the single item level, they said. The two companies plan to target the technology at manufacturers of higher end products such as perfumes, liquors, confectionary and ink cartridges, before moving on to the wider beverages markets.
It doesn't take a genius to figure out the leap in logic here poses unique security-related & confidentiality threats.
More
here.
(
Big props, Flying Hamster.)
Conan O'Brien Sketch Forces NBC to Buy HornyManatee.com

Caroline McCarthy writes on the C|Net "Missing Links" Blog:
It's not something that a broadcast TV network does every day, for sure. After a sequence about football mascots on "Late Night with Conan O'Brien" mentioned a fictional webcam site called "HornyManatee.com," NBC quickly snapped up the domain before pranksters could get to it.
They've actually put a site up there. It's pretty funny.
I agree. :-)
Link.
NFL Quarterback Tom Brady Sues Yahoo!
 Tom Brady
Tom Brady.
Along with a sweeping management reorganization and shrinking stock price, Yahoo! also has to contend with a lawsuit filed against it by the gridiron's golden boy, New England Patriots quarterback Tom Brady, who claims that the online giant improperly used his image to promote its fantasy football game.
In a federal complaint, Brady, 29, charges Yahoo! used his photo without authorization in a September 2006 Sports Illustrated ad and in banner ads on Yahoo! Sports pages.
More
here.
Solar Flares May Damage ComSat Links
Via UPI.
Russian scientists warned Wednesday that U.S. and other satellites could be damaged by a new wave of intense solar flares.
Russia's geophysical forecast center said in a statement reported by the RIA Novosti news agency that it predicted "powerful solar flares, vast explosions in the sun's atmosphere around sunspots, to occur in the near future."
"Solar flares can expel billion-ton clouds of electrified gas or plasma into space at a speed of 1 million miles per hour. Eruptions from the sun can damage satellites and disrupt electrical and communications systems on Earth, RIA Novosti said.
"An X9 solar flare was registered last Tuesday. Over 30 years of regular X-ray observations of the sun, only about 25 powerful flares have been registered, and they had never previously been observed in the solar minimum [the lowest point of the sun's 11-year activity cycle]. This is surprising, because normally such flares occur at the peak of the sun's activity," the center said according to the RIA Novosti report.
More
here.
U.S. Senate May Vote on Pretexting Bill This Week
Anne Broache writes on C|Net News:
Before politicians go home for the year at the end of the week, the U.S. Senate may vote to generally prohibit telephone "pretexting," a stealthy and usually fraudulent investigative technique made famous by a high-profile probe of media leaks at Hewlett-Packard.
U.S. Senate Majority Leader Bill Frist is using a procedure known as "hotlining," which would allow an already approved House of Representatives bill targeting pretexting to clear the Senate without debate and head to the president's desk to be signed into law. If no senators raise objections, the bill could be added to the Senate calendar and approved with a batch of other noncontentious items as soon as Thursday, a Republican leadership aide said.
More
here.
New Congress Turns Hostile to Ma Bell’s Man at the FCC
Via SaveTheInternet.com.
Incoming congressional leaders are taking a bleak view of efforts by FCC Chairman Kevin Martin to push through a series of Internet and media rulings before the Democratic Congress gains oversight of his agency.
This week the he’s scrambling to approve the merger of AT&T and BellSouth without protecting consumers or preserving Net Neutrality. To accomplish this he’s turning screws on one commissioner, Robert McDowell, pressuring him to violate professional ethics, “un-recuse” himself and rubber stamp the $82 billion deal.
More
here.
Internet Fuels Rise in Number of Jailed Journalists
Via CPJ.org.
The number of journalists jailed worldwide for their work increased for the second consecutive year, and one in three is now an Internet blogger, online editor, or Web-based reporter, according to an analysis by the Committee to Protect Journalists.
CPJ’s annual worldwide census found 134 journalists imprisoned on December 1, an increase of nine from the 2005 tally. China, Cuba, Eritrea, and Ethiopia were the top four jailers among the 24 nations who imprisoned journalists.
More
here.
(
Props, Declan McCullagh's Politech.)
Class Action Filed Against Kazaa on Behalf of Customers Sued by RIAA
Ray Berckerman writes on The Recording Industry vs. The People:
In Chicago, Illinois, a Kazaa customer has filed a class action against Kazaa, Lewan v. Sharman, U.S.Dist. Ct., N.D. Ill 06-cv-6736.
The lead plaintiff, Catherine Lewan, was a Kazaa customer who was sued by the RIAA for her use of Kazaa, and paid a settlement to the RIAA.
In her complaint she alleges, among other things, that:
- Kazaa deceptively marketed its product as allowing "free downloads" (Complaint, par. 30);
- It designed the software in such a manner as to create a shared files folder and make that folder available to anyone using Kazaa, while at the same time failing to make the user aware that it had done so (Complaint, par. 36-37); and
- It surreptitiously installed "spyware" on users' computers which made the shared files folder accessible to the Kazaa network even after the user had removed the Kazaa software from his or her computer (Complaint, par. 42-45).
More
here.
e-Mail, IM Registry for Sex Offenders Proposed
Robert Lemos writes on SecurityFocus:
A bill proposed on Thursday by two U.S. Senators would force Internet service providers to report any online content related to child exploitation they find on their networks and require that sex offenders provide state registries with all their online identifiers.
The bill, dubbed the "Stop the Online Exploitation of Our Children Act," is the brainchild of Republican Senator John McCain of Arizona and Democratic Senator Charles Schumer of New York. The registration of sex offenders online identities exactly matches a request made by MySpace earlier this week; the company hopes that mandating such information will help keep sex offenders out of the MySpace community.
More
here.
Six Security Vulnerabilities for Upcomg Microsoft Patch Tuesday
Via the Microsoft Security Response Center (MSRC) Blog.
Next Tuesday, on December 12, 2006 at approximately 10:00 am PT we are slated to release six new security bulletins:
- Five Microsoft Security Bulletins affecting Microsoft Windows. The highest Maximum Severity rating for these is Critical. These updates will be detectable using the Microsoft Baseline Security Analyzer and the Enterprise Scan Tool. Some of these updates will require a restart.
- One Microsoft Security Bulletins affecting Microsoft Visual Studio. The highest Maximum Severity rating for these is Critical. These updates will be detectable using the Microsoft Baseline Security Analyzer and the Enterprise Scan Tool. These updates may require a restart.
We will also be making our regular monthly update to the Microsoft Windows Malicious Software Removal Tool.
More
here.
ACS Slow to Notify on ID Theft Risk
Felix Doligosa Jr. writes in The Rocky Mountain News:
A company waited for a week to warn the public about the risk of identity theft after its computer containing names and Social Security numbers of as many as 1.4 million people was stolen, according to state documents.
Sometime during the weekend of Oct. 13, a computer was stolen from the 27th floor of the Affiliated Computer Services Inc. office in the 1900 block of Broadway. ACS is a Dallas- based company that processes child-support payments for the Colorado Department of Human Services.
The company reported the stolen computer to police on the evening of Oct. 16, according to a police report. The computer contains names and personal information on about 1.4 million child-support recipients, payers and new hires within the state.
More
here.
(
Props, Pogo Was Right.)
DoD Needs More Than a Few Good Spectrum Managers
Deconfliction? Is that a real word?
Bob Brewin writes on FCW.com:
The Defense Department’s radio frequency spectrum is an invisible and finite resource that is so critical to network-centric warfare that the Navy has allowed 250 electronic warfare officers to work with the Army to manage deconfliction issues in Iraq, said John Grimes, DOD chief information officer and assistant secretary of Defense for networks and information integration.
He gave a keynote speech here at the AFCEA’s Defense Spectrum Summit Dec. 6.
The Army considers spectrum management so important it has decided to develop a primary Military Occupational Specialty (MOS) for spectrum managers and expects approval of that new career field soon, Brig. Gen. Jeffrey Foley, the Army’s director of architecture, operations and space, told the conference attendees.
More
here.
Update: Police Raid IBM's Moscow Office
Jeremy Kirk writes on InfoWorld:
Police raided IBM's Moscow headquarters Wednesday in addition to two other IT suppliers in a $38.18 million investigation into procurement fraud, government officials said Thursday.
IBM spokesman Jonathan Batty confirmed that the raid had taken place. However, he wouldn't say if the authorities seized documents or computer equipment.
"We're stating for the time being that we are cooperating with the Russian authorities but declining to give any further comment now," Batty said.
Later on Thursday, Russia's Interior Ministry said the raids were part of an investigation into computer purchases by the country's Pension Fund. Executives of the Pension Fund are accused of conspiring to buy equipment from the companies at higher-than-market prices, according to Novosti, one of Russia's government-owned news agencies.
More
here.
Defense Tech: How Nuke Secrets Left Los Alamos
Via CBS News.
After seven years of security scandals at the nation's premier nuclear weapons research facility, the Los Alamos National Laboratory, the latest incident shows security — at least for some — amounts to little more than an honor system.
CBS News has learned how shockingly easy it was for a young employee to walk out of Los Alamos with classified data — data related to decades of U.S. underground nuclear weapons tests.
More
here.
Despite Growing Scams, U.S. Secret Service Pulls Agents Out of Nigeria
Brian Ross reports on ABC News' "The Blotter":
Despite massive counterfeiting of U.S. currency and checks in Nigeria, the American law enforcement agency with principal jurisdiction, the Secret Service, has closed its office in Lagos, Nigeria.
Nigerian officials said the decision has hurt efforts to crack down on criminal rings that produce the counterfeit currency and cheat thousands of Americans with online scams.
More
here.
Fergie Naked Hot Sex Porn

Aha! Gotcha!
You guys who keep coming to my blog looking for porn need to start looking here or here or elsewhere altogether.
So there. Now bugger off! :-)
- ferg
In Remembrance: Pearl Harbor
 USS California sinking.
USS California sinking.
Pearl Harbor Collection of pictures taken by military personnel.Image source: Wikimedia
You Are Not Forgotten
On this day in 1941 --
a day that will live in infamy -- the Imperial Japanese Navy made its
attack on Pearl Harbor.
The surprise attack on Pearl Harbor, Oahu, Hawaii, was aimed at the Pacific Fleet of the United States Navy and its defending Army Air Corps and Marine air forces. The attack damaged or destroyed twelve U.S. warships, destroyed 188 aircraft, and killed 2,403 American servicemen and 68 civilians.
Admiral Isoroku Yamamoto planned the raid as the start of the Pacific Campaign of World War II, and it was commanded by Vice Admiral Chuichi Nagumo, who lost 64 servicemen. However, the Pacific Fleet's three aircraft carriers were not in port and so were undamaged, as were oil tank farms and machine shops. Using these resources the United States was able to rebound within six months to a year.
The U.S. public saw the attack as a treacherous act and rallied strongly against the Japanese Empire, resulting in its ultimate defeat.
It absolutely
"...awakened the sleeping U.S. behemoth".
DHS Passenger Scoring Illegal?
Ryan Singel writes on Wired News:
A newly revealed system that has been assigning terrorism scores to Americans traveling into or out of the country for the past five years is not merely invasive, privacy advocates charge, it's an illegal violation of limits Congress has placed on the Department of Homeland Security for the last three years.
The Identity Project, founded by online rights pioneer John Gilmore, filed official objections to the Automated Targeting System, or ATS, on Monday, calling the program clearly illegal.
The comment cited a little-known provision in the 2007 Homeland Security funding bill prohibiting government agencies from developing algorithms that assign risk scores to travelers not on government watchlists.
More
here.
Gapingvoid: My Day Job?
Via gapingvoid.com. Enjoy!
Some Disturbing News: Online Directions Actually Really May Have Misled Kim Family
I blogged on this yesterday, regarding an MSNBC (AP Newswire) story that suggested that "...authorities say the cyber-savvy family may have plucked the route from Grants Pass to Gold Beach from an online mapping service, unaware of the elements."
My colleague, Jon O., sent me a message to the funsec list earlier this evening with revelations that this actually may have been the case.
Chills went down my spine when I read it, considering the tragic end to the story of the Kim family and the unfortunate situation that unfolded over the course of the past week or so.
My heart goes out to Katie Kim and her family.
Getting back to my point, Jon O. says:
I grew up "out in the woods" in Oregon and my Dad still works for the Forest Service out there. The Forest Service was providing some logistics support to the SAR teams. He spoke to the sheriff and suggested the police find out what type of GPS the car is equipped with, get the same model, and plot in the destination and drive the route. This comes from our experience in the woods of Maine and getting mis-routed by the in-car GPS (we almost ended up in the Atlantic, but we knew we were off route and knew how to get back).
The Kim family ate at Denny's in Glendale, OR. Here's the map from there to where they were going:
http://tinyurl.com/y55e5q
Mapquest does something interesting, it routes you the same way as google:
http://tinyurl.com/y4k6cd
But it has a checkbox:
Avoid Seasonally-Closed Roads
That doesn't change the route at all ;(. This is probably because there are roads that have planned closure during the winter and ones that just become impassable during bad weather.
Read the entire exchange
here.
Thanks to Jon O. for pointing this out.
Again, this entire story is very, very tragic. Our hearts are heavy...
ChoicePoint ID Theft Victims' Day Has Come
Roy Mark writes on internetnews.com:
Victims of the ChoicePoint identity theft scandal will soon be receiving claims forms to recover out-of-pocket expenses.
The Federal Trade Commission (FTC) mailed more than 1,400 of the forms Wednesday and made them available for download at the FTC ChoicePoint site. Restitution claims must be postmarked by Feb. 4.
The victims will be paid out of a $5 million fund established by ChoicePoint as part of its January settlement with the FTC. ChoicePoint also agreed to pay a $10 million fine for failing to adequately protect the consumer information in its databases.
The Georgia-based ChoicePoint is a credit report service used by more than 50,000 landlords and merchants to conduct background checks on potential tenants and customers. It also has several law enforcement and government agencies as clients.
More
here.
Quote of the Day: FBI Director Robert Mueller
"Public corruption is a betrayal of the public’s sacred trust. It erodes public confidence and undermines the strength of our democracy. Unchecked, it threatens our government and our way of life. That is why it is our top criminal investigative priority."
"Over the last two years, the FBI has convicted more than 1,060 government employees involved in corrupt activities, to include 177 federal officials, 158 state officials, 360 local officials, and more than 365 police officers. In FY 2005 alone, the Public Corruption Program saw a 25% increase in public corruption cases investigated, resulting in 890 indictments, 759 convictions, and 2,118 cases still pending. There are 622 agents currently working public corruption matters, an increase of 264 since 2002."
- FBI Director Robert Mueller, in a prepared statement presented before the Senate Judiciary Committee. Via The Project for Government Oversight.
An Early Christmas Present from the TSA
The Department of Homeland Security is apparently still hassling Chris Shoghoian, the guy who put up the fake boarding pass generator to prove a point about airline security access being a farce:
Dear Christopher,
We were slightly worried that you might spend Christmas relaxing and spending quality time with your family. We can't have that.
Thus, please enjoy the enclosed letter - we're quite confident that it'll occupy your thoughts for the next few weeks. Have fun mulling things over. We expect a reply from you by Christmas day.
Enjoy your holidays!
Love,
Your Friends at TSA.
More
here.
Report Finds Rampant Censorship at American Colleges and Universities
Via Government Technology.
A report released today by the Foundation for Individual Rights in Education (FIRE) reveals that burdensome restrictions on speech are commonplace at America's colleges and universities.
The report, entitled Spotlight on Speech Codes 2006: The State of Free Speech on Our Nation's Campuses [.pdf], surveyed more than 330 schools and found that an overwhelming majority of them explicitly prohibit speech that, outside the borders of campus, is protected by the First Amendment to the U.S. Constitution ["Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the Government for a redress of grievances."]
"There is a common misconception that 'speech codes' are a thing of the past -- a relic of the heyday of political correctness of the 1980s and 90s -- but the public needs to know that speech codes are perhaps more pervasive and restrictive than ever," FIRE President Greg Lukianoff said.
More
here.
Barracuda Spam Firewall Open to Attack for 20 Months?
Via heise Security.
The Barracuda Spam Firewall has been open to attacks for 20 months, according to an analysis by security specialist Jean-Sébastien Guay-Leroux. It is even possible for an attacker to open a shell on the firewall via the internet.
The firewall promises protection from spam, viruses, spoofing, phishing, spyware and DoS attacks. To do so it uses libraries, including the Convert-UUlib Perl library that provides an interface to uulib libraries, in order to be able to access different types of coded data. A buffer overflow in Convert-UUlib was discovered in April 2005 which could be exploited to infiltrate and execute malicious code via crafted BinHex files. Barracuda Networks apparently failed to notice this problem, with the result that the bug in their product was not fixed.
More
here.
German Prosecutors Eavesdrop on Media
Via UPI.
German prosecutors have tapped in on conversations between a lawyer and journalists in the case of CIA extraordinary rendition victim Khaled al-Masri.
According to the Sueddeutsche Zeitung newspaper and Stern news magazine, prosecutors from Munich eavesdropped on talks between Masri's lawyer, Manfred Gnjidic, and reporters from the German weekly magazine Stern and German public broadcaster ZDF. They considered five calls and one text message relevant to the investigation, and argued the move was aimed at finding the kidnappers of Masri, as they could have tried to contact him.
But Gnjidic, journalists and opposition politicians are furious about the eavesdropping on the lawyer, calling the move unconstitutional and a threat to civil liberties.
More
here.
Scotts Employee Gone in a Puff of Smoke
Paul J. Martinek writes in The Boston Herald:
Privacy in the modern workplace is virtually non-existent. Your employer can put video cameras pretty much everywhere but the bathroom. Every keystroke you make on your computer can be monitored. If you receive a voicemail or e-mail at work, not only can it be listened to or read by your boss, but it could be turned over to somebody who is suing your company. Just about the only thing you can do at your desk that is truly private is a live telephone conversation, due to strict wiretapping laws.
Scotts’ anti-smoking policy treats the lungs of employees as essentially company property. As Scotts apparently sees it, you have no more right to damage your lungs in your spare time then you do to drop a company laptop off your roof.
Controversial? Absolutely. Unlawful? Probably not, at least under existing laws.
More
here.
Background
here.
(
Props, Flying Hamster.)
UK Government Struggles to Prosecute Spammers
Tom Espiner writes on ZDNet UK:
The UK's privacy watchdog has admitted that it has not successfully prosecuted any UK spammers, despite regulations designed to curb spam being brought in three years ago.
The Information Commissioner's Office (ICO) has frequently said it has a lack of power to combat spam, and blames its lack of power on the UK Government. "We have not prosecuted spammers," said an ICO spokesman. "We have limited powers as you know to deal with people who pedal unsolicited marketing emails."
More
here.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Wednesday, Dec. 6, 2006, at least 2,918 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,330 died as a result of hostile action, according to the military's numbers.
The AP count is 19 higher than the Defense Department's tally, last updated Wednesday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casuality Count website
here.
Scary, Yet Real: Medical Records Database Would Span a Lifetime
Candice Lombardi writes on C|Net News:
Five major companies have joined forces and invested in what appears to be the ultimate personal medical-records database.
Applied Materials, BP America, Intel, Pitney Bowes and Wal-Mart Stores have sunk an undisclosed amount of money into the Omnimedix Institute, a nonprofit organization that developed and will manage the database, called "Dossia."
Dossia, which in 2007 will be made available to the companies' 2.5 million U.S. employees, dependents and retirees, will hold medical records from multiple sources for a person over their entire lifetime. The database could include test results and medical evaluations from various doctors' offices, hospitals and pharmacies.
More
here.
Groups Target Another Spyware Operator
Roy Mark writes on internetnews.com:
FastMP3Search.com.ar is the latest alleged spyware operator to get caught in the crosshairs of consumer and advocacy groups.
The Center for Democracy and Technology (CDT) and StopBadware.org are expected to file a complaint with the Federal Trade Commission (FTC) Thursday claiming the site's free plug-in installation contains adware and Trojan horse applications.
In addition, the complaint claims the free download disables the Windows firewall, changes homepage settings, sabotages valid Web addresses for legitimate security companies and impairs the performance of computers.
More
here.
Police: C|Net's James Kim Body Found
Via NBC11.com.
Authorities said Wednesday that James Kim's body has been found dead, NBC11's Susan Siravo reported.
"At 12:03 p.m., the body of James Kim was located in Big Windy Creek," said Brian Anderson, Undersheriff of Josephine County.
Anderson then broke down and could not continue his statement.
Gregg Hastings of the Oregon State Police Department then stepped to the microphone and said, "Arrangements are being made to have him moved from the area to an undisclosed location. The Kim family has made a specific request not to be contacted from any members of the media."
Authorities said at a 1:45 p.m. news conference, they did not know when the cause of death would be released.
More
here.
Bush 'Privacy Board' Just a Gag
Ryan Singel writes on Wired News:
The first public meeting of a Bush administration "civil liberties protection panel" had a surreal quality to it, as the five-member board refused to answer any questions from the press, and stonewalled privacy advocates and academics on key questions about domestic spying.
The Privacy and Civil Liberties Oversight Board, which met Tuesday, was created by Congress in 2004 on the recommendation of the 9/11 Commission, but is part of the White House, which handpicked all the members. Though mandated by law in late 2004, the board was not sworn in until March 2006, due to inaction on the part of the White House and Congress.
The three-hour meeting, held at Georgetown University, quickly established that the panel would be something less than a fierce watchdog of civil liberties. Instead, members all but said they view their job as helping Americans learn to relax and love warrantless surveillance.
More
here.
Lawmakers Question FCC Recusal Maneuver
Roy Mark writes on internetnews.com:
Key Democratic lawmakers leveled sharp criticism Tuesday at Federal Communications Commission (FCC) Chairman Kevin Martin's efforts to break the agency's deadlock over approval of the AT&T-BellSouth merger.
Last Friday, Martin informed Congress he is seeking the legal authority to allow Republican Commissioner Robert McDowell, who has recused himself from the vote, to participate in the merger approval process.
Without McDowell, the remaining two Republicans and two Democrats on the FCC are split along party lines over approving the deal that would create the world's largest telecommunications company.
More
here.
Computer Stolen from 130th Airlift Wing in Charleston
Via WTRF-TV (West Virginia/Ohio).
A laptop computer with personal information about every member of West Virginia's Army National Guard 130th Airlift Wing in Charleston recently was stolen.
The government-owned laptop computer was stolen from a member of the unit while he was attending an offical training course.
Maj. Todd Harrell said the computer's hard drive contains personal information, including Social Security numbers, names and birth dates of everyone in the 130th Airlift Wing.
More
here.
(
Props, Flying Hamster.)
Update: Satellite to be Rerouted in James Kim Search
Wow. Mountains moved.
Greg Sandoval writes on C|Net News:
A commercial satellite-imagery company said Tuesday it is rerouting one of its satellites to fly over the Oregon wilderness where rescue crews search for CNET editor James Kim.
GeoEye's Ikonos satellite will fly over the Western seaboard at about 10:30 a.m. PT Wednesday at a distance from the Earth of about 423 miles, said Mark Bender, a spokesman for the Dulles, Va.-based GeoEye. The satellite could record images of an area as large as 2,000 square kilometers.
The cameras on the Ikonos could once boast the world's highest resolution, able to get a bead on objects 39 inches wide.
More
here.
Reminder: psiphon is now released

For more information, see: http://psiphon.civisec.org/
A brief description:
psiphon is a human rights software project developed by the Citizen Lab at the Munk Centre for International Studies that allows citizens in uncensored countries to provide unfettered access to the Net through their home computers to friends and family members who live behind firewalls of states that censor.
For additional background, see here.
How Vista Lets Microsoft Lock Users In
Cory Doctorow writes on InformationWeek:
What if you could rig it so that competing with your flagship product was against the law? Under 1998's Digital Millennium Copyright Act, breaking an anti-copying system is illegal, even if you're breaking it for a legal reason. For example, it's against the law to compete head-on with the iPod by making a device that plays Apple's proprietary music, or by making an iPod add-on that plays your own proprietary music. Nice deal for Apple.
Microsoft gets the same deal, courtesy of something called "Information Rights Management," a use-restriction system for Office files, such as Word documents, PowerPoint presentations, and Excel spreadsheets.
More
here.
The U.S. Counter-Terror Nerve Center
Frank Gardner writes for The BBC:
In a Washington suburb, I am on a journey. No address, no postcode.
Just the phone number of a US government official known only as "T".
After months of requests, he has granted us permission to visit one of America's newest and most secret establishments: the National Counterterrorism Center, the NCTC.
It is a nondescript building, but inside is the beating heart of America's counter-terrorism nerve centre.
Hey, isn't AT&T's stock symbol "T"? :-)
More
here.
U.S. Toll in Iraq
Via The Boston Globe (AP).
As of Tuesday, Dec. 5, 2006, at least 2,906 members of the U.S. military have died since the beginning of the Iraq war in March 2003, according to an Associated Press count. The figure includes seven military civilians. At least 2,330 died as a result of hostile action, according to the military's numbers.
The AP count is seven higher than the Defense Department's tally, last updated Tuesday at 10 a.m. EST.
More
here.
And as always,
cryptome.org keeps a very, very extensive list
here, as does the
Iraq Coalition Casuality Count website
here.
Yahoo! Announces Major Reorganization
Elise Ackerman writes in The Mercury News:
Yahoo announced a major reorganization this evening, finally addressing critics who for months have questioned Yahoo's ability to effectively compete with other Internet giants.
In an announcement sent at 5:38 p.m., Yahoo said Dan Rosensweig, the chief operating officer, would leave Yahoo at the end of March.
Sue Decker, the chief financial officer, is being promoted to head one of three new business groups focused on advertisers and publishers. The other two groups are a technology group, which will be headed by Chief Technology Officer Farzad Nazem, and an audience group, whose leader has not yet been determined.
More
here.
Offbeat: Family Sues U.S. Mint Over Rare Coins
 A 1933 "Double Eagle"
A 1933 "Double Eagle"Image source: www.nationalcollectorsmint.com
An AP newswire
article by JoAnn Loviglio, via
SFGate.com, reports that:
A family is suing the U.S. Mint, saying it illegally seized 10 gold coins that are among the rarest and most valuable in the world that the family found among a dead relative's possessions.
The lawsuit, filed Tuesday in U.S. District Court in Philadelphia, accuses the Mint of violating the Constitution and breaking federal forfeiture laws by refusing to return the 1933 "double eagle" coins to the family after it handed the coins over to have their authenticity confirmed.
More
here.
Defense Tech: DHS Eyes Frickin' High-Powers Lasers for Protecting Commercial Flights
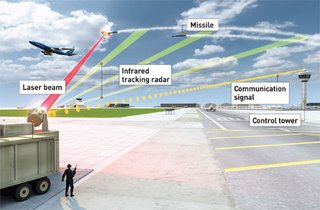 Image source: PopSci.com / John MacNeill
Image source: PopSci.com / John MacNeill
Stephen Handelman
writes on
Popular Science:
This summer’s war between Lebanon and Israel was the most recent demonstration of the deadly threat posed by shoulder-fired missiles. Lebanese Hezbollah fighters armed with portable rocket launchers fired more than 3,700 missiles into Israeli cities during the 34-day conflict. With a growing number of such weapons, referred to in military-speak as MANPADS (Man-Portable Air Defense Systems) showing up on the black market, U.S. officials are becoming increasingly concerned about their risk to commercial aircraft. That’s why the Department of Homeland Security is nearly doubling its spending on countermeasure research to $110 million this year.
One particularly notable technology under consideration is a laser called Skyguard that can make mincemeat out of a missile in a matter of seconds, according to its developer, defense contractor Northrop Grumman, which adapted the laser from a larger militarized version. Packed inside a unit the size of three school buses and stationed close to the runways, Skyguard is essentially a giant laser gun with brains. It focuses a powerful energy beam with pinpoint accuracy on a missile, heating up the explosives inside to make them detonate before reaching their target.
More
here.
Online Directions May Have Misled Kim Family
An AP newswire article, via MSNBC, reports that:
The snow-covered back-country road that trapped the Kim family of San Francisco was meant for tourists, but not at this time of year.
Authorities say the cyber-savvy family may have plucked the route from Grants Pass to Gold Beach from an online mapping service, unaware of the elements.
Despite its impassable snowdrifts and single-lane, Bear Camp Road is offered as the preferred route on some Web sites and on-board-directions software available on some new cars, most of which have no business in those mountains in the winter.
More
here.
Sun Unleashes Major Solar Flare
 A solar flare recorded early on Dec. 5, 2006.
A solar flare recorded early on Dec. 5, 2006.
Image source: NOAA / SEC
Robert Roy Britt
writes on
Space.com:
The Sun is just past its low-point in an 11-year cycle of activity. But big eruptions can happen anytime. One just did.
A major X-9 flare erupted this morning. It emanated from a large sunspot, numbered 929, which is just coming into view around the eastern limb of the Sun.
The flare lifted off the Sun at 5:35 a.m. ET. It was directed away from Earth. But this sunspot will rotate toward the center of the Sun over the next few days and could offer up more major blasts that could take direct aim at our planet, forecasters say.
Flares of this magnitude (X-class flares are all major) can damage satellites and disrupt telecommunications on Earth. They can also threaten astronauts in space. NASA sometimes orders astronauts aboard the International Space Station to retreat to the most well-protected part of the orbiting outpost to avoid excess radiation exposure. Spacewalks are avoided during solar storms.
More
here.
New Microsoft Word 0-Day Vulnerability
Via Microsoft TechNet.
Microsoft is investigating new public reports of limited “zero-day” attacks using a vulnerability in Microsoft Word 2000, Microsoft Word 2002, Microsoft Office Word 2003, Microsoft Word Viewer 2003, Microsoft Word 2004 for Mac, and Microsoft Word 2004 v. X for Mac, as well as Microsoft Works 2004, 2005, and 2006.
In order for this attack to be carried out, a user must first open a malicious Word file attached to an e-mail or otherwise provided to them by an attacker.
As a best practice, users should always exercise extreme caution when opening unsolicited attachments from both known and unknown sources.
More
here.
Survey: NAC Backlash Growing
Here's something that caught me somewhat unexpectedly.
Tim Greene writes on NetworkWorld:
Network Access Control technologies may be waning as a priority for U.S. businesses because decision makers worry that the technology isn’t quite baked yet, according to an upcoming study by TheInfoPro.“People are taking it off their books for the next 12 months and waiting for it to mature,” says Bill Trussell, managing director of networking for the analyst firm.
Research to be published next month says that of 126 network professionals, 37% say it is very likely or extremely likely they will decide to develop or implement a NAC policy initiative in the next 12 months, down 17% from earlier this year.
More
here.
'Bad Guys are Winning' Despite Fight Against Spam
Brad Stone writes on The International Herald Tribune:
Three years ago at the World Economic Forum in Davos, Switzerland, Bill Gates, the Microsoft chairman, made an audacious prediction: The problem of unsolicited junk e-mail messages on the Internet would "be solved by 2006," he said.
Mehran Sabbaghian scoffs at that forecast. Sabbaghian, the network engineer at the Web-hosting company Lanset America, said that a sudden Internetwide increase in spam last month clogged his company's servers so badly that delivery of regular e-mail messages to customers was delayed by hours.
More
here.
Breaking: Rescue Crew Find C|Net's James Kim's Pants
Via NBC11.com.
Searchers Tuesday found pants belonging to a missing San Francisco man who set out three days ago seeking help for his family stranded in the snowy Oregon Coast Range, according to NBC affiliate KGW.
The search for James Kim, an editor for the technology Web site CNET, began again Tuesday at daybreak, giving rescuers some much-needed light.
Trackers said he had headed downhill and apparently walked out of an area covered with snow. The trackers "were following scuff marks" in dirt and rock, said Undersheriff Brian Anderson of Josephine County.
The drainage Kim followed headed for the nearby Rogue River, and the search and rescue teams brought out rafts Tuesday to check the river.
More
here.
Privacy Board Knows Number of Americans Targetted by NSA but Won't Share the 411
What a farce.
Ryan Singel writes again over on 27B Stroke 6:
Lisa Graves, the Deputy Director of the Center for National Security Studies, had two simple questions for the White House Privacy and Civil Liberties Board: Did they know how many Americans had been eavesdropped on by the warrantless wiretapping program and if so, how many?
Alan Raul, the panel's vice chairman, acknowledged in a roundabout way that the members had gotten such data, but said that the data were too sensitive to release. Graves then asked if the Board had pushed to have that data made public, as are the Justice Department is required to do with raw numbers of typical spy wiretaps.
Raul declined to say if the board had suggested that.
More
here.
Thieves Exploit Phone System for the Deaf
Lisa Myers, Tim Sandler & the NBC News Investigative Unit:
About 22 million calls are expected to be placed this way this year, at a cost of $92.5 million. The IP Relay system is funded by little-noticed charges on our monthly phone bills, charges described in terms like "Disability Access Fee" or "Carrier Cost Recovery Fee."
But an NBC News investigation shows that this well-meaning service may now be helping the criminal community more than the deaf community because of serious flaws in the relay system.
For instance, operators are required to repeat any message — no matter how vile or obscene.
More
here.
IE7 Targeted by Adware Firms
Phil Muncaster writes on IT Week (UK):
Adware writers are likely to target the latest version of Internet Explorer with increasing frequency in 2007, causing a threat to user productivity, according to the Trend Micro chief technology officer for anti-spyware, Ed English.
In London this week with the firm's two other CTOs, Raimund Genes and Dave Rand, English told IT Week that adware companies will take advantage of the new features in IE7 to make money, such as the new tabbed browsing function, which can be hijacked to display the link to a dedicated adware site.
"IE7 will soon be the most dominant browser on the market, and it will [provide new opportunities] for exploits like 'tab-jacking'," he argued. "IE7 is also about to become the world's most popular RSS reader, so there is an opportunity for adware to be injected into RSS feeds."
The three also added their voices to the growing number calling on ISPs to use better content-based filtering to clamp down on spam and to provide security services alongside their basic connectivity packages.
More
here.
Full Disclosure: Trend Micro is my employer...

















