Foreign Spies Are Serious. Are We?
Michelle Van Cleave writes in The Washington Post:
In 2003, when I began my three years as the first congressionally mandated national counterintelligence executive (known by the unpronounceable acronym NCIX), Washington seemed ready to transform the fight against foreign espionage into a focused, coherent enterprise. But today, this vital national security mission is on life support.
Think this isn't a big deal? Think again. Most Americans would be astonished to learn how successful foreign intelligence services have been at stealing our national security secrets and threatening our vital interests.
The Chinese stole the design secrets to all -- repeat, all -- U.S. nuclear weapons, enabling them to leapfrog generations of technology development and put our nuclear arsenal, the country's last line of defense, at risk. To this day, we don't know quite when or how they did it, but we do know that Chinese intelligence operatives are still at work, systematically targeting not only America's defense secrets but our industries' valuable proprietary information.
ad_icon
The Soviets, of course, were especially aggressive at spying -- a tradition that has roared back to life in Vladimir Putin's Russia. It was bad enough that the KGB learned so much about U.S. vulnerabilities, but scores of hostile intelligence services and terrorist groups have also been schooled in the tradecraft that the Soviets perfected.
More
here.
Hat-tip: GroupIntel
French Fighter Planes Grounded by Computer Virus
Kim Willsher writes on The Telegraph:
The aircraft were unable to download their flight plans after databases were infected by a Microsoft virus they had already been warned about several months beforehand.
At one point French naval staff were also instructed not to even open their computers.
Microsoft had warned that the "Conficker" virus, transmitted through Windows, was attacking computer systems in October last year, but according to reports the French military ignored the warning and failed to install the necessary security measures.
The French newspaper Ouest France said the virus had hit the internal computer network at the French Navy.
Jérome Erulin, French navy spokesman told the paper: "It affected exchanges of information but no information was lost. It was a security problem we had already simulated. We cut the communication links that could have transmitted the virus and 99 per cent of the network is safe."
However, the French navy admitted that during the time it took to eradicate the virus, it had to return to more traditional forms of communication: telephone, fax and post.
More
here.
PCI Compliance and Terrorism
Via The PCI Compliance Blog.
We have read complaints on other blogs about the PCI standards, claiming they are a burden for merchants and software developers. But when considering the documented link between credit card fraud—which PCI DSS was developed to fight against—and terrorism, perhaps complaints about security standards will fall silent.
Kimberly Kiefer Peretti, Senior Counsel in the Computer Crime and Intellectual Property Secti on of the U.S. Department of Justice, recently wrote an excellent white paper, “Data Breaches: What the Underground World of ‘Carding’ Reveals” [.pdf] . In this paper, she gives a concise overview of large scale data breaches by skilled hackers—who is doing it and how, as well as the implications of these breaches.
One of Peretti’s most salient points comes in her discussion of how carding—activities surrounding the theft and fraudulent use of credit and debit card account numbers—is linked to other criminal behavior, including terrorism and drug trafficking.
More
here.
DTV Storm Coming?
Clayton Sandell writes for ABC News:
As a meteorologist and storm expert who flies into hurricanes, Paul Flaherty knows how important it is to prepare for a disaster.
But as he looked over some of the emergency supplies in his closet a couple of weeks ago, he realized that one important item on his checklist is going to be useless in the next hurricane: his portable analog television.
It's one of the potential problems for people living in a hurricane zone, or any potential disaster area, as television stations make the government-mandated switch from traditional analog broadcasts to ones that are all digital.
When the power goes out in a hurricane, untold thousands of residents will find that their battery-powered analog TVs, which provide vital information including where a storm is headed and when the worst of it has passed, will no longer be compatible with the digital broadcasts.
More
here.
U.S. Toll in Iraq, Afghanistan

Iraq and Afghanistan statistics via The Boston Globe (AP).
As of Friday, Feb. 6, 2009, at least 4,237 members of the U.S. military had died in the Iraq war since it began in March 2003, according to an Associated Press count.
The figure includes eight military civilians killed in action. At least 3,406 military personnel died as a result of hostile action, according to the military's numbers.
The AP count is two fewer than the Defense Department's tally, last updated friday at 10 a.m. EST.
As of Friday, Feb. 6, 2009, at least 573 members of the U.S. military had died in Afghanistan, Pakistan and Uzbekistan as a result of the U.S. invasion of Afghanistan in late 2001, according to the Defense Department. The department last updated its figures Friday at 10 a.m. EST.
Of those, the military reports 418 were killed by hostile action.
More
here and
here.
Also, a
very troubling note:
Just one week after the Army announced that more U.S. soldiers killed themselves in 2008 than in any other year on record, the U.S. Army announced today that they had 24 possible suicides during the month of January.
That is more than the nine soldiers killed in Afghanistan last month, and the 14 killed in Iraq -- combined.
More
here.
And as always, the
Iraq Coalition Casualty Count keeps the grim watch on their website
here.
Honor the Fallen.
In Passing: James Whitmore

Cuba to Keep Internet Limits After Fiber Optic Cable
An AFP newswire article, via France24, reports that:
Cuba will continue to limit Internet access even after a fiber optic cable linking the island with Venezuela comes online in 2010, a top official said.
The new cable is 1,550 kilometers (960 miles) long and will dramatically increase the island's level of connectivity, according to officials.
"We believe that the most responsible policy is to privilege collective access" to the Internet, said Boris Moreno, deputy minister of computer science and communication.
Nevertheless, there is a desire for "larger number of citizens to have Internet access," technical and economic conditions allowing, Moreno told the daily Juventud Rebelde.
But he warned that the new fiber optic cable "will not necessarily decrease the price the country pays for connection to international networks."
More
here.
Port of Los Angeles Prepares to Cancel Controversial Chinese X-ray Contract
Jacob Goodwin writes on Government Security News:
Nearly seven months after taking delivery of a mobile X-ray system manufactured in the People's Republic of China, the Port of Los Angeles is on the verge of canceling the controversial contract.
The staff at the port has recommended that the Board of Harbor Commissioners find DULY Research, Inc., the California-based broker who represents the Chinese manufacturer, in default of the terms of the contract, when it next meets on Feb. 5.
The contract created a stir in the media and on Capitol Hill because the manufacturer is Nuctech Company Limited, a Chinese company headquartered in Beijing, whose president happens to be the son of the President of the People's Republic of China.
Critics of the deal argued that procuring a Chinese-built X-ray scanning system could endanger U.S. national security, that it would outsource U.S. manufacturing jobs, and that it was possible that Nuctech had "reverse engineered" patented U.S. and European X-ray technologies. The fact that a large portion of the purchase price would be reimbursed with a port security grant from the U.S. Department of Homeland Security drew additional criticism.
More
here.
Hat-tip: ThreatsWatch.org
U.S. Congressman Twitters an Iraq Security Breach
John M. Donnelly writes on CQ Politics:
A congressional trip to Iraq this weekend was supposed to be a secret.
But the cat’s out of the bag now, thanks to a member of the House Intelligence Committee who broke an embargo via Twitter.
A delegation led by House Minority Leader John A. Boehner , R-Ohio, arrived in Iraq earlier today, and because of Rep. Peter Hoekstra , R-Mich., the entire world — or at least Twitter.com readers—now know they’re there.
“Just landed in Baghdad,” messaged Hoekstra, a former chairman of the Intelligence panel and now the ranking member, who is routinely entrusted to keep some of the nation’s most closely guarded secrets.
Before the delegation left Washington, they were advised to keep the trip to themselves for security reasons. A few media outlets, including Congressional Quarterly, learned about it, but agreed not to disclose anything until the delegation had left Iraq.
Nobody expected, though, that a lawmaker with such an extensive national security background would be the first to break the silence. And in such a big way.
More
here.
Friday Monkey Blogging: Baby Chimp Flies to Germany on Commercial Jet
 Bili
BiliAs I
mentioned a couple of months ago, I have started a regularly recurring blog entry meme every Friday afternoon, inspired by Bruce Schneier's regular series of
"Friday Squid Blogging" posts, and my very own maddening
Monkey Theory.
Here is this week's installment.
Via The Telegraph.Wrapped in a white cotton cloth, three-month-old bonobo Bili sat amongst other bemused passengers on the flight to Frankfurt.
The tiny ape who was rejected by his birth mother Maringa at Twycross Zoo flew nearly five hundred miles to meet its new foster family.
Bili was carried on to the plane in a soft cotton security blanket he had been nursed in since birth.
He was left to enjoy the in-flight entertainment as he snuggled into the arms of his new German Keeper, who had flown to the UK a few days previously.
Kim Riley at Twycross Zoo said: "We were so excited when we found out Bili had a foster family to go to.
"We've never had any of our animals travel on board an aircraft before- but he is just like a little baby.
"The keeper from Frankfurt Zoo had bonded with him over the past few days and Bili had started stretching his arms out to him for cuddles before they left."
Staff at Twycross took on the role of surrogate parents after Bili was rejected by its mother in October.
More
here.
Image source: The Telegraph /Caters News Agency
Homeland Security Intelligence Bill Aims to Improve Sharing
Corey McKenna writes on Government Technology:
U.S. intelligence gathering is pretty good. Investigations post-9/11 showed that information had been known that could have stopped the hijackers at several points. The point where it breaks down is in the sharing. The result is the worst attack against civilians on U.S. soil in history. Sharing intelligence may have helped those indicators stick out by connecting the dots. Legislation passed by the House earlier this week may make sharing the necessary intelligence more common.
On Tuesday, the U.S. House of Representatives passed a bill that seeks to reduce the over-classification of intelligence information and increase the amount that gets shared. "Though hard to believe, sheriffs and police chiefs can't readily access the information they need to prevent or disrupt a potential terrorist attack because those at the federal level resist sharing information," U.S. Representative Jane Harman said. "Over-classification and pseudo-classification -- stamping with any number of sensitive but unclassified markings -- remain rampant."
The 9/11 Commission and others have observed that the over-classification of information related to homeland security interferes with timely sharing of accurate and actionable information. It also increases the cost of information security and needlessly limits public access to information.
Therefore, DHS should assume that all information that is not properly classified or designated as controlled unclassified information and otherwise exempt from disclosure should be made available to the public under the Freedom of Information Act.
More
here.
NIST Updates FISMA Recommendations
William Jackson writes on GCN.com:
The National Institute of Standards and Technology has released an initial draft for public comment of a revised version of its Recommended Security Controls for Federal Information Systems and Organizations.
Although this is Revision 3 [.pdf] of Special Publication (SP) 800-53, NIST calls it the first major update of the guidelines since its initial publication in December 2005. NIST tries to revisit its security guidance every two years and update them as needed, said senior computer scientist Ron Ross. But revising a 200-plus-page comprehensive set of recommendations is expensive and time-consuming.
“We don’t want to undertake it unnecessarily,” Ross said. “But the threat environment has changed quite a bit and we’ve learned a lot in that time from the agencies in their implementation of the controls. All of this made a compelling need to do an update.”
SP 800-53 is part of a series of documents setting out standards, recommendations and specifications for implementing the Federal Information Security Management Act (FISMA).
More
here.
OpenDNS to Step Up Fight Against Conficker Worm
Robert Westervelt writes on SearchSecurity:
OpenDNS is stepping up the battle against the Microsoft Conficker/Downadup worm, with a new service launching next week that predicts the worm's command and control domains and ultimately blocks them, rendering the worm useless.
The service relies on researchers from antivirus vendor Kaspersky Lab, who have dissected the worm's domain algorithm, and can predict which domains the worm will use to get its orders. Kaspersky will pass the information on to OpenDNS, which will update its servers and bulk block the domains, said David Ulevitch, founder and chief technology officer of OpenDNS.
"We'll be able to effectively cut the worm off at its knees," Ulevitch said. "Infected machines will not be able to phone home, and without being able to phone home the worm is dead in the water."
More
here.
Computer Virus Shuts Down Houston Municipal Courts
Dale Lezon writes in The Houston Chronicle:
A computer virus struck some City of Houston computers earlier this week, forcing municipal court operations to shut down for at least two days beginning at 4 p.m. today. officials said.
Court offices will remain open and people can pay tickets and other fines as well as get assistance for court matters, but judges will not call dockets and handle cases, said Gwendolyn Goins, municipal courts spokeswoman.
The city hopes to have the problem fixed by Tuesday so that courts can resume full operation. However, she said, officials are uncertain how long it will take to correct the problem.
Goins said cases scheduled for dates and times when the courts will be closed will be automatically reset to later dates and people will be notified by mail.
She said the virus, which was first detected in some city computers Wednesday, has blocked access to files at the court.
More
here.
Toon of The Day: Spare Change

We love Mr. Fish.
Via Truthdig.com.
- ferg
Russia Now 3 and 0 in Cyber Warfare
Kevin Coleman writes on Defense Tech:
In January of 2009 the world witnessed the third successful cyber attack against a country. The target was the small country of Kyrgyzstan. The country is only about 77,000 square miles in size with a population of just over 5 million. The attackers focused on the three of the four Internet service providers. They launched a distributed denial of service attack traffic and quickly overwhelmed the three and disrupting all Internet communications.
The IP traffic was traced back to Russian-based servers primarily known for cyber crime activity. Multiple sources have blamed the cyber attack on the Russian cyber militia and/or the Russian Business Network (RBN). RBN is thought to control the world's largest botnet with between 150 and 180 million nodes. These reports go on to say that Russian Officials hired the technically capable group to do this.
It is widely believed that this group also played a substantial role in the Estonia Attack in 2007 and the attack on Georgia in 2008. The mechanism of attack was a fairly large botnet with nodes distributed in countries around the world. One significant difference in the Kyrgyzstan attack is that most of the DDoS traffic was generated in Russia.
More
here.
U.S. Spies Form Virtual Units 'On The Fly' to Track Terror
James Gordon Meek writes on Mouth of The Potomac:
When a cell of 10 Islamic militants stole into the Indian port city of Mumbai in November and began to unleash a fusillade of hell on two hotels, a train depot in rush hour and a Jewish center, US spooks scrambled to make sense of it all. About 20 analysts from across the globe immediately convened - not in the same room, but on two classified Web sites called Intellipedia and A-space.
Think of it as Wikipedia and Facebook for spies.
The first Mumbai entry was posted by a watch officer at the National Counterterrorism Center at the onset of the attacks, officials told The Mouth. Soon, analysts from across America’s 16 spy agencies familiar with extremists in India and Pakistan logged on to A-space - a discussion site accessible to only a few thousand US intelligence analysts with the highest security clearances - to weigh who the attackers might be.
Analysts posted realtime satellite imagery and video depicting the carnage outside the Taj Mahal Hotel, which showed a sluggish response by Indian security forces. They also uploaded the first news photos of one young terrorist in Mumbai’s rail station who was later nabbed alive - noting how professionally he carried his weapons, and how he was dressed as blandly Western as the 9/11 hijackers 7 1/2 years ago.
The ad hoc group of analysts, who did not all know each other - including at least one in a Far East military outpost - quickly agreed that a claim of responsibility by the unheard of “Deccan Mujahadeen” was malarkey. It was really the handiwork of Pakistan’s Al Qaeda-affiliated Lashkar-e-Taiba.
More
here.
Kyrgyzstan: U.S. Air Base Decision is Final
Via Reuters AlertNet.
Kyrgyzstan said on Friday its decision to shut a U.S. air base in the Central Asian country was final.
"The decision has been made," said Kyrgyz government spokesman Aibek Sultangaziyev. "The U.S. embassy and the (Kyrgyz) Foreign Ministry are exchanging opinions on this, but there are no discussions on keeping the base."
Link.
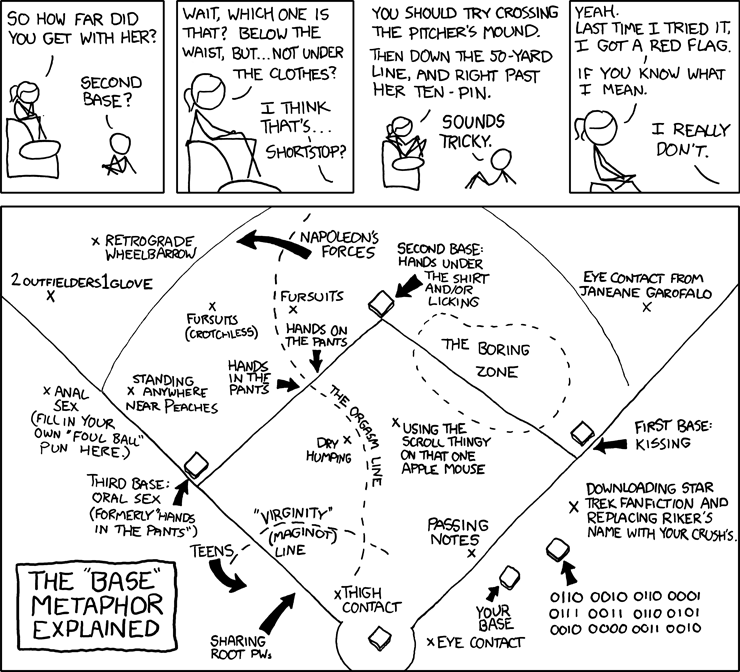
Classic xkcd: All Your Base...
Click for larger image.
xkcd rocks the house - big time.
- ferg
Defense Tech: Russia's Bears Spread Their Wings Over the Arctic Ocean
 Russian Tupolev Tu-95 Bear Bomber
Russian Tupolev Tu-95 Bear Bomber
Martin Sieff
writes for UPI:
Russia is continuing its new series of strategic nuclear bomber long-range missions over the Arctic Ocean.
Two Tupolev Tu-95 Bear strategic bombers crossed the Arctic Ocean and flew as far as Alaska, a Russian air force spokesman announced Jan. 28.
"Two Tu-95MS strategic bombers took off from an airbase in eastern Russia on Tuesday and successfully carried out a patrol mission over the neutral waters of the Arctic Ocean and near Alaska," Lt. Col. Vladimir Drik informed RIA Novosti.
Drik said the flight lasted 10 hours, indicating it covered a distance of 4,500 to 5,000 miles, given the usual cruising speed of a turboprop-engine-powered Tu-95MS. The crews of the two planes carried out instrumental flight exercises in arctic climate conditions, RIA Novosti said.
The flight was also notable for the kind of cat-and-mouse encounters with the U.S. Air Force reminiscent of the Cold War.
More
here.
More Heartland Details Leak Out (And Some May Be Trying To Leak Back In)
Evan Schuman writes on StorefrontBacktalk:
Details surrounding the Heartland data breach continue to dribble out, with one respected payment systems newsletter reporting that the forensic investigators Heartland brought in were Cybertrust and Neohapsis.
Heartland had tried keeping those names confidential, an effort that was succeeding prior to the Wednesday, Feb. 4 issue of The Nilson Report. That newsletter also quoted from a MasterCard alert, which provided new details about what was taken and when.
“According to a MasterCard alert, this sniffer program stole card numbers and expiration dates from credit and debit cards processed by Heartland from May 14, 2008, through Aug. 19, 2008, as the information entered Heartland’s payment switch,” the Nilson story said. “Only an estimated 5 percent of the stolen card numbers also included names. The malware was likely deactivated when Heartland conducted regular system upgrades as part of its PCI Data Security Standards (PCI DSS) compliance program, although it’s possible that the hackers shut it down to try and avoid being traced.”
In other Heartland news, it seems that officials there may be preparing to backtrack on some of the details they previously disclosed. Since Friday (Jan. 30), Heartland has been promising a written statement to clarify—and apparently back off from—some of the details they revealed in interviews. As of Wednesday (Feb. 4) night, no such statement had materialized, nor were Heartland officials willing to discuss what would be in the statement.
More
here.
CSC to Manage FBI Call Center
David Hubler writes on Washington Technology:
Computer Sciences Corp. will continue to manage FBI call center operations under a five-year task order that has a potential value of $59 million.
The award calls for the contractor to continue supporting the FBI National Instant Criminal Background Check System (NICS) with call center and help desk services.
Federal firearms licensees use the call center’s toll-free telephone number to request background checks on individuals purchasing firearms, company executives said.
The original contract was awarded to Datatrac Information Systems Inc. in 2003. Datatrac was acquired by CSC in 2006. This new contract was awarded to CSC during the company’s third quarter of fiscal year 2009, officials said.
More
here.
Deloitte: Firms Lack Confidence They Can Deter Internal Attacks
Chuck Miller writes on SC Magazine US:
Human error is the leading cause for IT system breaches, and most corporate security officials do not feel confident they can protect their organizations from internal cyberattacks, according to Deloitte Touche Tohmatsu's annual survey.
In all, the survey [.pdf] , released Wednesday, found that the global recession is putting information at great risk for these companies.
“The economic situation has heightened the concern with a number of institutions, and the threats and the vulnerabilities and the risks have increased," Mark Steinhoff, principal in Deloitte's security and privacy services practice, told SCMagazineUS.com Thursday. "You have tighter budgets, and greater concerns over internal breaches."
Eight-six percent of survey respondents said human error is the leading cause of information systems failure. This finding indicates that normally trustworthy employees can act abnormally during the stressful times of a poor economy, according to Deloitte. More than a third (36 percent) of respondents expressed concern about insiders' misconduct, compared to only 13 percent who were concerned about external threats. Despite this, 58 percent of respondents said they do not feel confident they can prevent internal attacks.
More
here.
More Security Angst For Android
Andy Greenberg writes on Forbes.com:
For Google, keeping its Android mobile platform secure may be becoming a game of "whack-a-bug."
In a talk at the Shmoocon hacker conference in Washington, D.C., on Saturday, security researcher Charlie Miller plans to present a vulnerability in Google's (nasdaq: GOOG - news - people ) mobile software that he says would allow a hacker to remotely take control of the device's browser, allowing him to steal passwords stored in the software, watch a users' browsing or siphon off credit card data as it's entered on the Web.
It won’t be the first time that Miller has poked a hole in Android. Within days of the October release of T-Mobile's G1, the first phone to use Google's open-source platform, Miller and fellow researchers at Independent Security Evaluators found a similar vulnerability that allowed them to take control of the phone's browser and potentially steal users' information or spy on their browsing. Miller's team warned Google about the problem, and the company released a patch in early November.
But Miller, who has gained notoriety in the data security world by compromising high-profile devices ranging from the iPhone to the MacBook Air, says his repeated hacks may be a sign that Google's relatively new software is "a little immature" from a security standpoint, compared to others such as Windows or Mac OS that have been field-tested for years by security firms.
More
here.
Calififornia DMV Tried to Sneak In Biometrics for Driver's Licenses, Groups Claim
Jaikumar Vijayan writes on ComputerWorld:
Consumer rights groups in California are protesting what they claim is an attempt by the state Department of Motor Vehicles to sneak in via the backdoor a fingerprint and facial-recognition system for issuing driver's licenses in the state.
The groups claim that the use of such biometric technology has been opposed by state legislators in the past, and that the DMV was trying to do an end-run around opposition by hiding its plans in a seemingly innocuous vendor contract.
If unchallenged, the contract would allow the DMV to establish a new government biometric database containing facial and fingerprint information on more than 25 million Californians over the age of 16, without first giving legislators and technology experts a chance to vet the proposal.
The DMV did not respond to a request for comment.
More
here.
ICANN: Proposed Global Policy for Remaining IPv4 Address Space - Final Call for Comments and Background Report
Via ICANN.org.
On 4 February 2009, the Chair of the Address Supporting Organization Address Council forwarded a Proposed Global Policy for Remaining IPv4 Address Space, for ratification by the ICANN Board. Essentially, the proposal states that each Regional Internet Registry, RIR, be allocated one /8 IPv4 address block when the IANA free pool of IPv4 address space reaches five remaining /8 blocks. For the full text of the proposal click here.
The development of Global Internet Number Resource Policies is the subject of an MoU, known as the ASO MoU, between the RIRs/NRO and ICANN. There are also specific ICANN Board Procedures for handling global policy proposals in this context. In line with the procedures, a final call for public comments is now open until 26 February 2009.
Much more
here.
Patch Tuesday Advance Notice: Microsoft Plans Critical Patches for IE, Exchange
Gregg Keizer writes on ComputerWorld:
Microsoft Corp. today said it will deliver four security updates on Tuesday, two of them pegged "critical," and will finally issue a patch for SQL Server that it's been working on since last April.
The four updates detailed in the advance notice published today will quash bugs in Internet Explorer 7 (IE7); its Exchange mail server software; the Visio application that's part of the Office line-up; and SQL Server. The IE and Exchange vulnerabilities will be labeled critical, the company's highest threat ranking, while the SQL Server and Visio bugs will be marked as "important," one step lower.
Microsoft will release the updates on Feb. 10.
More
here.
Experts Question Fallout from New Monster Hack
An AP newswire article by Jordan Robertson, via SFGate.com, reports that:
For the second time in less than 18 months, the job-search Web site Monster.com was breached, along with USAJobs.gov, which Monster's parent company runs for the federal government. And yet Monster might suffer little fallout — because the overall state of computer security is so bad anyway.
Attacks against Web sites have become so common, security experts say, that Monster Worldwide Inc. won't necessarily scare customers away with its January disclosure that its database was plundered of user IDs, passwords, e-mail addresses, names and phone numbers. Monster makes money by charging employers that post jobs and scan the resumes of applicants, who use the service for free.
Security experts said Monster didn't appear to be doing enough to secure its computers, but many played down the latest breach because Monster said no Social Security numbers, personal financial information or resumes were stolen. However, Monster didn't say how many records were exposed. In a previous breach, in August 2007, con artists grabbed resumes on 1.3 million people.
Both incidents affected Monster.com, which boasts more than 75 million members, and USAJobs.gov, which has 8 million registered users. They're both alluring targets because people give job search sites all kinds of personal information. Even just the user names and passwords people use on the sites can be golden to a thief, since people often don't change their information from site to site.
More
here.
Alleged Attacker Flaunts Details of phpBB Hack
Robert Lemos writes on SecurityFocus:
A vulnerability in the PHPlist newsletter manager, which was publicly disclosed in mid-January but not fixed until two weeks later, allowed an attacker to access critical files on phpBB.com, the person claimed over the weekend.
In a post on Blogger on Saturday, a person who claims to have breached the Web site of open-source online community software phpBB gave a detailed account of how he did it. Using a vulnerability in PHPlist publicly disclosed on January 14, the attacker gained access to the password and configuration files for the server, according to the post. The attack occurred before the PHPlist developers issued a patch for the problem on January 29.
"So I login and see what I can come across, wow 400,000 registered emails, I’m sure that will go quick on the black market, sorry people but expect a lot of spam," the self-proclaimed attacker wrote.
The incident matches the description of the attack posted by administrators of phpBB.com on Monday.
More
here.
Mark Fiore: Wall Street Executive Air

More Mark Fiore brilliance.
Via The San Francisco Chronicle.
Enjoy.
- ferg
Toon of The Day: D.C. Radicalism

We love Mr. Fish.
Via Truthdig.com.
- ferg
ANZ Bank Internet Portal Breached - UPDATED
Mitchell Bingemann writes on Australian IT:
ANZ Bank has warned customers not to surrender personal information after its online banking system was breached.
The bank said customers are being prompted to enter personal details in an online form after successfully logging on to the ANZ internet banking portal.
"There is a known issue in the marketplace affecting banks where a "Personal Details form" appears to customers after they log on to internet banking," reads an ANZ security warning.
ANZ instructs customers to not enter any personal details and to immediately end their internet banking session if the form is displayed.
More
here.
Note: More details will be posted as additional information becomes available.
-fergUpdate 1: This story has been
updated.
-ferg
OpenOffice Installs Insecure Java Version
Brian Krebs writes on Security Fix:
An alert reader let me know that the latest version of OpenOffice, the open source alternative to the Microsoft Office productivity suite, also installs a very old, insecure version of Java.
Users who accept the default installation options for OpenOffice 3.0.1 also will get Java 6 Update 7, a version of Java that Sun Microsystems released last spring (the latest version is Java 6 Update 12).
This is notable because not only could attackers target security vulnerabilities that were fixed in subsequent versions of Java, but Java 6 Update 7 was released prior to Sun's inclusion of a feature known as "secure static versioning," which is intended to prevent Web sites from invoking even older versions of Java that may be present on the user's system.
More
here.
Porn Site Feud Spawns New DNS Amplification Attack
Robert McMillan writes on PC World:
A scrap between two pornographic Web sites turned nasty when one figured out how to take down the other by exploiting a previously unknown quirk in the Internet's Domain Name System (DNS).
The attack is known as DNS Amplification. It has been used sporadically since December, but it started getting talked about last month when ISPrime, a small New York Internet service provider, started getting hit hard with what's known as a distributed denial of service (DDOS) attack. The attack was launched by the operator of a pornographic Web site who was trying to shut down a competitor, hosted on ISPrime's network, according to Phil Rosenthal, the company's chief technology officer.
The attack on ISPrime started on the morning of Sunday, Jan. 18. It lasted about a day, but what was remarkable was that a relatively small number of PCs were able to generate a very large amount of traffic on the network.
One day later, a similar attack followed, lasting three days. Before ISPrime was able to filter the unwanted traffic, attackers were able to use up about 5GB/second of the company's bandwidth.
More
here.
Terry Childs Files $3M Suit Against City of San Francisco
Robert McMillan writes on PC World:
The network administrator who was jailed for allegedly holding San Francisco's city government network hostage has filed a US$3 million claim against the city.
Terry Childs made national headlines last year, when he was arrested after refusing to hand over the passwords he used to the wide area network that he managed for the city. Childs eventually did comply, giving the information to San Francisco Mayor Gavin Newsom, but he has remained in jail since his July 12 arrest, held on a $5 million bond. He faces seven years in prison if convicted.
His $3 million claim for damages was filed with the city on Jan. 8, and was first reported by the San Francisco Examiner on Wednesday. "The claim alleges that the city and county of San Francisco, through the manager that Terry worked for ... made claims that resulted in his wrongful arrest," said Childs' lawyer, John Prentice.
Childs, formerly a network administrator with the city's Telecommunications and Information Services (DTIS), had argued that the department's staff was incompetent and that the mayor was the only person qualified to handle the passwords.
More
here.
House Approves Whitelist of People Who Aren't Terrorists
David Kravets writes on Threat Level:
The House overwhelmingly adopted legislation this week mandating the creation of a new kind of terrorist watchlist: a database of people who aren't terrorists, but are routinely flagged at airports anyway.
The U.S. government maintains a list of about a million names of suspected terrorists that is crosschecked with passenger names ahead of airline boarding. The list has been dogged for years by sloppy name matches that have ensnared innocent travelers, children, prominent politicians and government officials, the U.S. Conference of Catholic Bishops' secretary of education and all men named David Nelson.
Under the new plan, approved late Tuesday 413-3, innocent victims of the terrorist watchlist must prove to the Department of Homeland Security, through an undetermined appeals process, that they are not terrorists. They would then get their names put on what the legislation calls the "Comprehensive Cleared List."
More
here.
Estonian Defense Minister: Europe Has Not Done Enough on Cyber-Defense
Via Monsters & Critics.
Europe has not yet done enough to protect its internet and communications systems from web-based attacks, the politician whose country fought the world's first-ever cyber war told Deutsche Presse-Agentur dpa on Wednesday.
'A lot has been done, but whether enough has been done or not, I hesitate: most probably not,' Estonian Defence Minister Jaak Aaviksoo said in an exclusive interview with dpa.
Estonia's famously internet-based government fought off a major cyber-attack in April 2007 as pro-Russian hackers targeted the country in retaliation for the government's decision to relocate a Soviet-era war memorial from central Tallinn.
Aaviksoo, who was defence minister at the time, has since emerged as a leading authority on the issue, delivering the keynote speech to an EU cyber-defence seminar in Brussels on Wednesday.
More
here.
Off Topic: Can of Spam

Really.
- ferg
Hat-tip: MX Logic
Hackers Break Into AT&T e-Mail Accounts
Via MySanAntonio.com.
Hackers broke into AT&T Inc.’s Worldnet e-mail accounts that “use easy-to-guess user passwords,” a spokesman confirmed Tuesday.
The hackers took over a few hundred accounts and began sending out large amounts of spam during the past three weeks, said Mike Barger, AT&T spokesman. AT&T disabled those accounts.
AT&T also sent notices to all of its 600,000 e-mail customers notifying them to strengthen their passwords to a “complex password” by Feb. 15 to better protect their account.
More
here.
Hat-tip: Office of Inadequate Security
Report: Most Spam Sites Tied to Just 10 Registrars
Brian Krebs writes on Security Fix:
Nearly 83 percent of all Web sites advertised through spam can be traced back to just 10 domain name registrars, according to a study to be released this week.
The data come from millions of junk messages collected over the past year by Knujon ("no junk" spelled backwards and pronounced "new john"), an anti-spam outfit that tries to convince registrars to dismantle spam sites.
While there are roughly 900 accredited domain name registrars, spammers appear to register the Web sites they advertise in junk e-mail through just one percent of those registrars. Knujon's rankings include:
1. XinNet Cyber Information Company Limited
2. eNom
3. Network Solutions
4. Register.com
5. Planet Online
6. Regtime Ltd.
7. OnlineNIC Inc.
8. Spot Domain LLC
9. Wild West Domains
10. Hichina Web Solutions
More
here.
In Remembrance: Justin Polazzo

One year ago today, a friend and colleague departed on a different kind of journey.
Although I never met "Dude Van Winkle" (Justin's online persona), we chatted often, for a couple years, on network security issues & life in general -- and I felt as though I did know him a bit more than someone who merely shared the same trail of electrons occasionally in "the ether".
We miss you, Dude.
I still have you in my OTR cert/key cache.
Really.
- ferg
Twitter Clickjacking Hack Released
Kelly Jackson Higgins writes on Dark Reading:
A Web developer has released a proof-of-concept clickjacking attack targeting Twitter that demonstrates how an attacker could take over a member's "update" function on the microblogging site.
In a nutshell, all it takes is for the victim to click on a seemingly innocent link on a Webpage while logged into Twitter, and then his or her "What are you doing?" status is under the attacker's control. "It means anyone can update your Twitter status without you knowing," says James Padolsey, the independent Web developer who wrote the PoC and published it on his Website.
More
here.
Analysis: Russia, Ukraine - Crimea a Ticking Bomb
 Crimea
Crimea
Joshua Kucera
writes in
The San Francisco Chronicle:
A marble plaque on the wall of the Russian Sailors' Club, one of the city's trademark white granite neoclassical buildings, reads: "Time Capsule: To be opened by service members of the Russian Black Sea Fleet and citizens of the hero city of Sevastopol, 22/2/2021."
In 2021, however, there may be a problem finding a Russian naval official to open it - Sevastopol is part of Ukraine, whose government wants Russia and its fleet to vacate this port city of 400,000 inhabitants by 2017.
While the Russian-Ukrainian dispute over natural gas has garnered international headlines in recent months, it is Crimea - an autonomous 10,000-square-mile peninsula on the northern coast of the Black Sea - that has more long-term potential for conflict between the two former Soviet states, most analysts agree.
About 58 percent of Crimea's 2 million inhabitants are ethnic Russians, and Sevastopol is home to a major Russian naval base. Ukraine has drawn Russia's ire by its friendly relations with the West and firm desire to join NATO. And like South Ossetia, the breakaway state that helped fuel last year's war between Georgia and Russia, Crimea is an enclave whose residents mostly favor closer ties with Russia.
More
here.
Image source: travel2crimea.com
FireFox 3.0.6 Now Available
Get it here.
- ferg
Fixed in Firefox 3.0.6
MFSA 2009-06 Directives to not cache pages ignored
MFSA 2009-05 XMLHttpRequest allows reading HTTPOnly cookies
MFSA 2009-04 Chrome privilege escalation via local .desktop files
MFSA 2009-03 Local file stealing with SessionStore
MFSA 2009-02 XSS using a chrome XBL method and window.eval
MFSA 2009-01 Crashes with evidence of memory corruption (rv:1.9.0.6)
Federal Workers Notified After SRA Breach
Robert McMillan writes on NetworkWorld:
Employees at federal security agencies are being notified that their personal information may have been compromised after hackers planted a virus on computer networks of government contractor SRA International.
SRA began notifying employees and all of its customers after discovering the breach recently, company spokeswoman Sheila Blackwell said Tuesday. The malicious software may have allowed hackers to get access to data maintained by SRA, including "employee names, addresses, Social Security numbers, dates of birth and healthcare provider information," the company said in a notification [.pdf] posted at the Maryland Attorney General's Web site.
The breach is embarrassing for SRA, a 6,600-employee technology consulting company that sells cybersecurity and privacy services to the federal government. The company wouldn't say which federal agencies were affected by the breach, but in U.S. Securities and Exchange Commission filings it lists intelligence agencies and those such as the U.S. Department of Defense, the U.S. Department of Homeland Security and the U.S. National Guard among its clients.
More
here.
FinCEN Gets 'So-So' Security Report Card From GAO
Angela Gunn writes on BetaNews:
The Treasury Department bureau responsible for watching for money laundering isn't watching its security closely enough, according to GAO auditors. Worse, much of FinCEN's problems lie with the notoriously security-poor IRS.
FinCEN needs to step up its documentation efforts and its implementation of security control, according to a report from the US Government Accountability Office.
The report was presented last week to members of the House of Representatives, examined FinCEN's own information systems and the points at which FinCEN (the Financial Crimes Enforcement Network) draws on IRS and Treasury Communications System (TCS) data. Data was compiled from March 2008 to January 2009.
Together, FinCEN uses those three systems to administer the Bank Secrecy Act, which works with law enforcement here and abroad to nail down money laundering and the crimes associated with it. You probably know the BSA best as "that rule that you can't get access right away to all the funds when you deposit a really big check, and then they ask all those questions."
More
here.
FBI Investigates $9 Million ATM Scam
John Deutzman writes on MyFOXNY.com:
A Fox 5 investigation exposes a worldwide ATM scam that swindled $9 million and possibly jeopardized sensitive information from people around the world. Law enforcement sources told Fox 5 it's one of the most frightening well-coordinated heists they've ever seen.
Photos from security video obtained by Fox 5 show of a small piece of a huge scam that took place all in one day in a matter of hours. According to the FBI , ATMs from 49 cities were hit -- including Atlanta, Chicago, New York, Montreal, Moscow and Hong Kong.
"We've seen similar attempts to defraud a bank through ATM machines but not, not anywhere near the scale we have here," FBI Agent Ross Rice told Fox 5.
More
here.
Hat-tip: Office of Inadequate SecurityNote: More here on
Threat Level.
Drive-By 'War Cloning' Attack Hacks Electronic Passports, Driver's Licenses
Kelly Jackson-Higgins writes on Dark Reading:
With a $250 used RFID scanner he purchased on eBay and a low-profile antenna tucked away in his car, a security researcher recently cruised the streets along Fisherman's Wharf in San Francisco, where he captured -- and cloned -- a half-dozen electronic passports within an hour.
Chris Paget, who will demonstrate the privacy risks with these IDs at the Shmoocon hacker confab later this week in Washington, D.C., coined this newest RFID attack "war cloning" given its similarity to war-driving, or wireless sniffing. "War cloning -- it's the new hacker sport," he says.
The security weaknesses of the EPC Gen 2 RFID tags, which lack encryption and true authentication, have been well-known and of concern to privacy advocates for some time. These tags are being used in the new wallet-sized passport cards that the U.S. Department of Homeland Security offers under the new Western Hemisphere Travel Initiative for travel to and from Western Hemisphere countries. The e-cards are aimed at simplifying and speeding up the border-crossing process, providing U.S. Customs and border agents with information on the individual as he or she queues up to inspection booths at the border.
More
here.
Turkish 'Hacker' Spied for PKK
Via Today's Zaman.
A prosecutor is seeking a sentence of up to 10 years for a man who was taken into custody last November on suspicion of theft but who turned out to be a hacker working for the terrorist Kurdistan Workers' Party (PKK).
A Diyarbakır prosecutor has completed his indictment against R.Ç., who admitted in late November that he was a hacker working for the outlawed PKK. The prosecutor is requesting a sentence of up to 10 years on charges of "consciously and willingly aiding a terrorist organization."
A police search of a computer belonging to R.Ç., who had been detained in Diyarbakır on suspicion of theft, revealed files containing classified information belonging to institutions including the General Staff and the National Intelligence Organization (MİT).
A search of the computer showed that the suspect had not only sent MİT documents to the PKK, but also had an "online friendship" with Murat Karayılan, the commander of PKK terrorists in northern Iraq. R.Ç. was arrested on Nov. 14 on charges of "acquiring state secrets and confidential documents on behalf of the PKK terrorist organization."
More
here.
Hat-tip: Politically Motivated Computer Crime & Hacktivism
More Security Problems Turn Up At Los Alamos
Robert O'Harrow Jr. writes on Government Inc.:
The Project On Government Oversight has found evidence of more security breaches at Los Alamos National Laboratory -- one of the places in America's security-industrial complex that's supposed to be safe.
You all may recall multiple reports over the last few years of impossible-seeming breaches at the top-secret protected weapons lab. In 2007, authorities recommended a record fine against the lab's contract manager, the University of California, after finding that security procedures were riddled with gaps.
That recommendation followed the discovery that more than 1,000 pages of classified documents and "several computer storage devices in a trailer" occupied by an employee of a subcontractor who once worked as an archivist at the lab.
Now there's more, according to POGO.
"According to a Los Alamos internal email, it has not been a good week for Los Alamos National Laboratory (LANL). There was a break-in at the Santa Fe home of a LANL scientist, from which three LANL computers were stolen. And in an unrelated incident, a LANL Blackberry was lost in a "sensitive foreign country." The internal email from the Threat Reduction (TR) unit notes that "this is garnering a great deal of attention with senior management as well as NNSA representatives."
More
here.
Classic xkcd: Crypto Crackers
Click for larger image.
We
love xkcd.
Enjoy!
- ferg
Congratulations, Pittsburgh Steelers - Super Bowl Champs

Image source: Matt Slocum / AP
Pat Tillman's Spirit Very Much Alive at Super Bowl

Jennifer Waters writes on MarketWatch:
Pat Tillman wasn't at Raymond James Stadium for Sunday's 43rd annual Super Bowl, but his spirit was very much alive here.
Among the Warner, Fitzgerald and Boldin jerseys that Arizona Cardinals fans were donning were a noticeable number of red-and-white shirts bearing Tillman's No. 40.
"He's the man," said Tom Rector of Phoenix, who has been wearing his Tillman jersey since 2002, the last year that the Cardinals safety played in the NFL. "He's a hero. Everyone else is a professional athlete or role model, but Tillman's a hero."
Tillman's football record isn't as impressive as his life record, which gained star status when he gave up a $3.6 million football contract to enlist in the Army's elite Rangers after the Sept. 11, 2001 terrorist attacks. Three years later, the 27-year-old was killed in Afghanistan in friendly fire. The incident became controversial after it was discovered that the Army covered up that Tillman was killed by fellow soldiers in the confusion of battle.
"To give that up for the country is just an amazing thing," said Scottsdale, Ariz., resident Glenn Allbritton, who bought his jersey through the Pat Tillman Foundation. "I'll do anything to help support his memory and help his foundation."
More
here.
Cyber Crime Threat Rising Sharply
Tim Weber writes for The BBC:
The threat of cybercrime is rising sharply, experts have warned at the World Economic Forum in Davos.
They called for a new system to tackle well-organised gangs of cybercriminals.
Online theft costs $1 trillion a year, the number of attacks is rising sharply and too many people do not know how to protect themselves, they said.
The internet was vulnerable, they said, but as it was now part of society's central nervous system, attacks could threaten whole economies.
The past year had seen "more vulnerabilities, more cybercrime, more malicious software than ever before", more than had been seen in the past five years combined, one of the experts reported.
More
here.